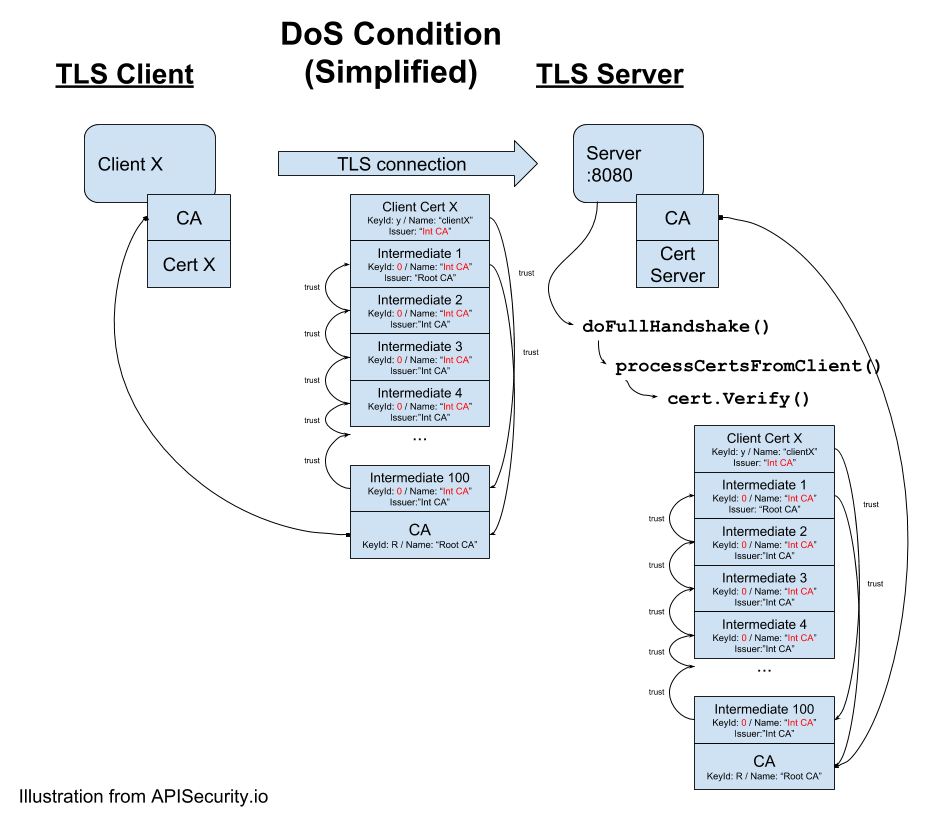
This week, an Authy API was misused to verify the registered phone numbers of millions of users and recent injection attacks are prompting US security agencies to promote secure by design for software development. A research team demonstrates IoT hacking via API. As this is a significant milestone for 42Crunch and APIsecurity.io, namely our 250th […]
Issue 250: Authy API breach, US agencies push secure by design, APIs grill IoT devices, shares by our readers