This week, we have a report on how attackers are exploiting APIs faster than previously based on research into over 650 API-related vulnerabilities and a walkthrough guide into DVGA, a vulnerable GraphQL application. We also have further coverage of the Twitter API (this time an outage) and, finally, views from Dana Epp on the new OWASP API Security Top 10. We also have news of not one but two events coming up in June.
Report: Attackers are exploiting APIs faster than previously
First up this week, we have an article from Help Net Security discussing how attackers exploit API vulnerabilities faster than previously thought. The research comes from Wallarm, who analyzed 350,000 vulnerability disclosures to find 650 API-specific vulnerabilities. From there, they narrowed this to 115 published exploits associated with these vulnerabilities, with the results shown in summary form below:
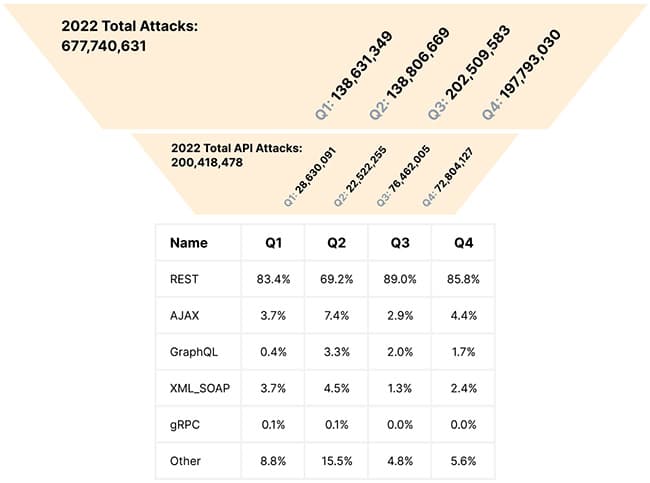
The report concludes that based on their data from 2022, APIs are increasingly under attack with the following trends in particular:
- Attack growth: the report indicated an increase of 197% in attacks on APIs under observation.
- CVE growth: the number of Common Vulnerabilities and Exposures (CVE) involved has grown by 78% in this time, i.e., the attacks are using a growing number of attack vectors and exploit types.
- Worsening time-to-exploit: the most concerning point is that the time-to-exploit is becoming significantly shorter, making it harder for defenders to protect their APIs. The report quotes a reduction from 58 days to practically zero or less currently, and notes that zero-day exploits exist for nearly two months before their CVE is published.
The report concludes that the number of API threats tripled in 2022, and in many cases, exploits exist before the vulnerability is even published. A further note of caution warns on the prevalence of injection attacks being the primary attack vector used by attackers and that attacks are more frequently targeting the DevOps and cloud-native platforms.
Guide: DVGA walkthrough
How-to guides are a perennial favorite with our readers and this week, we have a great one courtesy of Edward Lichtner (@EdwardLichtner) as he takes us through the Damn Vulnerable GraphQL Application (DVGA) application. Edward wrote the guide primarily as part of his documentation as he worked through the DVGA exercises but has kindly made this available to the community. It is a thorough write-up worth reading in detail if you want to learn more about GraphQL and how to attack it.
As a tl;dr the guide covers the following tools:
- Altair, which is a GraphQL client
- graphql-introspection nmap script
- graphw00f, which is a GraphQL server fingerprinting tool
- InQL, which is a set of Burp extensions for GraphQL
- Sqlmap, which is the ubiquitous SQL injection tool
The guide covers the following topics: fingerprinting the server, denial-of-service attacks (including batch query attacks, deep recursion query attacks, resource-intensive query attacks, field duplication attacks, alias-based attacks, and circular fragment attacks), information disclosure (GraphQL introspection, GraphQL interface, GraphQL field suggestions and Server side request forgery (SSRF)), injection (SQL, OS command, stored XSS, logging and HTML), authorization bypass (GraphQL interface protection bypass, GraphQL query deny list bypass and GraphQL JWT token forge), and several other miscellaneous topics.
In conclusion, Edward recommends the “Black Hat GraphQL” book from Nick Aleks (@Nick_Aleks) and Dolev Farhi (@dolevfarhi), featured here last week. This is a comprehensive guide, and I thank Edward for contributing to the community. Keep your eyes open for more guides from Edward in the near future.
Article: Twitter API outage blocks access
It feels like we cover Twitter and its API travails every other issue (here and here), and today we have another story making the news — this time, an API outage blocking access to users. In this case, it appears that a relatively minor change to an API backend caused a major outage, affecting their APIs and mobile and web applications. The outage was reported globally, with users encountering various error messages relating to API access. Twitter support acknowledged the outage on their Twitter feed, and Elon Musk later admitted that a “small API change had massive ramifications” and would “ultimately need a complete rewrite.”
This outage comes shortly after Twitter announced plans to shut down its free access tier. Needless to say, re-engineering an API at the scale of Twitter’s will incur some measure of instability; it would be no surprise if this were to re-occur.
Article: Upcoming changes to OWASP API Security Top 10
Finally, in this week’s news is coverage from Dana Epp on the upcoming recently announced changes to the OWASP API Security Top 10. To quote Dana — “while a lot has stayed the same, a lot has changed.” This topic will be covered in a lot more detail in upcoming weeks (and months !) so I will summarise briefly only.
Two flaw categories drop off the Top 10 list, namely API8:2019 – Injection and API10:2019 – Insufficient Logging & Monitoring. In the case of injection flaws, this does not indicate any reduction in this attack vector but indicates that API-specific attacks have risen to prominence. In fact, as recently as issue 200, we have reported on a command injection vulnerability. Insufficient Logging and Monitoring is an evergreen topic for software security and best practice guidance should be employed for API development.
There are three new additions to the Top 10: firstly, API7:2023 – Server Side Request Forgery reflects the rise in attacks leveraged against APIs forcing them to redirect to URLs outside of the APIs control. Secondly, API08: Lack of Protection from Automated Threats reflects the rise in prominence of bot or automated attacks against APIs. Finally, API10: Unsafe Consumption of APIs addresses the dangers of placing implicit trust in 3rd party APIs.
Keep reading to get up to date with our detailed coverage (see the next article !) of the new Top 10 and, most importantly, how you can defend yourself against these new vectors. Thanks as ever for the article Dana.
Event: apidays Interface 2023
I will be speaking at the upcoming apidays Interface 2023 online event on the topic of – you guessed it – the recent changes to the OWASP API Security Top 10 recently announced. I’ll focus on the new flaw categories introduced, particularly looking at real-world examples of these flaws resulting in vulnerabilities.
Join me (and several of our other frequent contributors to the newsletter) on the 28th and 29th June 2023, as we cover everything relating to APIs, including security.
Event: 42Crunch at Infosecurity 2023
Infosecurity 2023 takes place from the 20th to the 22nd of June 2023 at the ExCel center in London, and 42Crunch will be in attendance at booth #M85. Join me and my colleagues during the week for a coffee and chat, or attend one of our events, namely:
- 10-minute lightning talks on the hour at the booth on topics pertaining to API security.
- my 90-minute deep-dive workshop on API Security Done Right – Best Practices for Secure API Development at 10 am on 21st June.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy
