This week, we have news of the so-called “GhostToken” vulnerability affecting Google Cloud. We also have articles from Gartner on a report on zero trust not being a silver bullet, how authentication attacks threaten API security, and finally, why API security is everywhere except where you need it.
Vulnerability: GhostToken vulnerability in Google Cloud
This week, we have news of the so-called GhostToken vulnerability, which could allow attackers to target Google Cloud users via the application marketplace. According to the researchers at Astrix who discovered the vulnerability, it could have allowed attackers to access the target account’s Google Drive, Calendar, Photos, Google Docs, Google Maps, and other Google Cloud Platform services. The researchers reported their findings to Google in June 2022, Google accepted them in August 2022, and in April 2023, they released a global patch to address the issue. Researchers also recommended that Google Cloud users regularly verify the application installed on their instance using the application management page on the Google Cloud portal.
The root cause of the vulnerability relates to the manner in which Google Cloud manages the lifecycle of an application and, specifically, how the application’s associated OAuth2 tokens are managed. The Google Cloud provides a 30-day grace period from the time an application is scheduled for deletion until the time it is permanently deleted. This grace period is to allow administrators an opportunity to recover resources deleted in error. While in the pending deletion state, the application (and its associated resources such as OAuth2 tokens) are invisible to platform users. The researchers at Astrix discovered that if an application’s pending deletion was canceled within the 30-day window, then the application and all its associated resources would be restored. They tested this with an OAuth2 token and discovered that this token still provided access to its original resources.
They describe how this delete/pending deletion/cancel deletion loop can be used to effectively hide a rogue application from the application management page of a user’s Google Cloud portal, using the following attack flow:
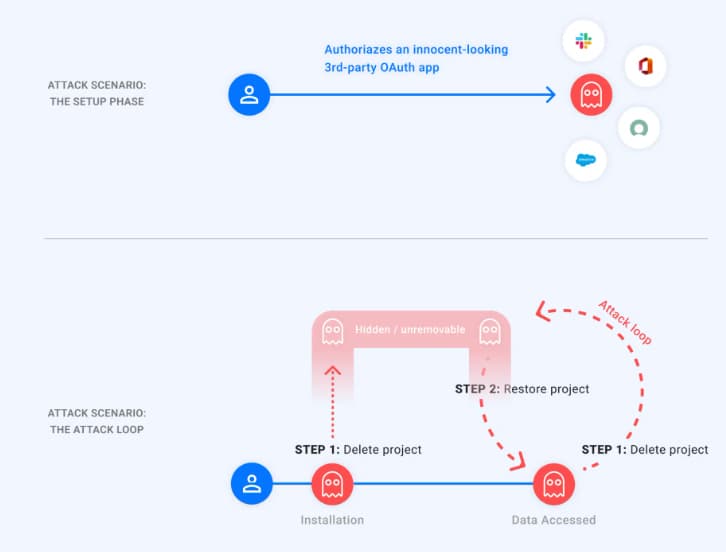
Using this technique, an attacker could effectively hide their application in perpetuity except for a short window every 30 days where they executed the restore / delete step. This would make it almost impossible for an attacker to detect the presence of a malicious application.
A timely reminder for administrators to regularly check for unused or unexpected access tokens on their platforms.
Article: Gartner’s views on zero trust
Next up, we have views from Gartner and other industry experts on the promises of zero trust, particularly its impact on API security. The article featured in Venture Beat cites findings from recent Gartner research, which indicates that while 97% of organizations have a zero trust initiative, only 10% of them will have a measurable program in place by 2026. While zero trust offers great promise to reducing overall cyber risk, the report is a timely reminder that it is not a silver bullet or simple cure-all, particularly with respect to API security.
According to Gartner, the greatest challenge with zero trust is that it is primarily an access control, which proves ineffective in protection attacks targeting other layers of the modern application surface. In particular, scaling zero trust to protect APIs is challenging, contributing to the scale of API breaches seen throughout 2023, including the T-Mobile and Twitter breaches (featured here and here in this newsletter).
The article highlights interesting differences in views between industry leaders on how best to protect APIs. For Forrester, organizations should move away from protecting APIs with traditional perimeter-based security approaches and embedding security into the API development lifecycle (certainly a view I share). However, others differ in opinion — Ted Miracco (CEO of Approov) suggests that this shift-left approach to API security fails to address the real-world challenges to API security, citing the fact that many breaches have occurred against APIs that were perfectly well authenticated. His approach is to ensure that APIs are continuously monitored against threats in real-time.
The report concludes that zero trust is an effective risk reduction control, but that additional controls (specifically continuous monitoring) are necessary for hardening the API security posture. For me, the best approach remains the shift-left and shield-right approach.
Article: Authentication attacks threaten API security
In the next article from Infosecurity Magazine, we take a deeper look at why authentication attacks threaten API security. Certainly, according to OWASP, broken authentication remains a significant challenge to API security in 2023.
There are a number of reasons contributing to poor API authentication, both on the API implementation and the client side. In the case of the implementation, this can range from simple flaws, such as forgetting to implement the authentication check in the code, to incorrectly handling and processing a JWT token (forgetting to verify the signature, for example). On this client side, authentication can be weakened by the use of weak passwords, or by insecure handling of tokens and keys.
There are a number of recommendations that can be implemented to harden API authentication, including:
- Generate complex passwords and keys: Enforce a password policy requiring a minimum length and complexity, and ensure that keys are sufficiently long and not predictable.
- Protect your password reset process: A common vector used by attackers is to brute force the password reset process. Enforce rate limiting or other out-of-band challenges on the password reset endpoints to thwart attempts to brute force them.
- Generate tokens correctly: JWT tokens are frequently generated incorrectly, including omitting a signature, or expiration date.
- Enforce token expiration: Ensure that tokens and keys have an expiration date and do not persist forever to minimize the impact of a lost or stolen token.
- Protect against token and key leakage: Use a password manager or vault to store keys so that they cannot be accessed by third parties.
- Enforce step-up authentication: When accessing sensitive endpoints, enforce an additional layer of security, such as using MFA or additional challenges.
- Ensure a robust revocation process exists: In the event of a compromise, ensure that you have a robust process to be able to revoke and then re-issue the affected keys or tokens.
Authentication is one of the most important API security vulnerabilities, but fortunately, one of the easier ones to mitigate by following relatively simple best practices.
Article: API security is everywhere, except where you need it
The final article this week comes from Security Boulevard and features the thoughts of Josh Thorngren on why API security is everywhere except where you need it.
The author believes API security is a broad topic but poorly defined, which tends to confuse the user when selecting an appropriate solution. For example, API security can range from using SAST tools for testing API code (I’ve previously discussed this approach and its shortcomings) to attempting to use network firewalls to protect APIs at runtime. Yet other vendors focus on the importance of managing your inventory as a route to reducing API security risk.
The author describes the approach taken by Mayhem, which automatically generates and executes attacks against your APIs (in a similar fashion to the 42Crunch API conformance scan). The advantage of performing this type of extensive testing before reaching production is to identify any vulnerabilities, weaknesses, and data leaks in your APIs. Additionally, this testing can identify performance and reliability concerns, as well as other anomalous.
The article concludes with some tips to improve API security including:
- Ensure that your authentication and authorization implementation is well designed and robustly implemented.
- Monitor API usage regularly and keep up-to-date on vulnerabilities.
- Use input validation to prevent attackers from being able to abuse your APIs against their design intent.
- Be proactive about API security right at design time, and understand the risks in the event of compromise.
Article: Why most API Security solutions have not delivered on the hype
Finally, this week, we feature the thoughts of my colleague Tom Chang on why API security solutions have not delivered on the hype.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy
