This week, we have a vulnerability in the AWS API gateway that allows a potential cache-poisoning attack, disclosed at the recent BlackHat Europe conference, a guide on how to harden Kubernetes API access, a report from Forbes on the need to take API security more seriously, and predictions on what’s possibly on the next OWASP API security Top 10.
Vulnerability: AWS API gateway vulnerable to HTTP header-smuggling attack
At the recent BlackHat Europe security conference, web security researcher Daniel Thatcher disclosed vulnerabilities relating to the AWS API gateway that allowed HTTP header smuggling. Currently, AWS has not responded to this research nor offered a comment regarding the potential vulnerabilities in their API gateway.
PortSwigger sums up HTTP header smuggling as am attack vector well:
“HTTP request smuggling is a technique for interfering with the way a website processes sequences of HTTP requests that are received from one or more users. Request smuggling vulnerabilities are often critical in nature, allowing an attacker to bypass security controls, gain unauthorized access to sensitive data, and directly compromise other application users.”
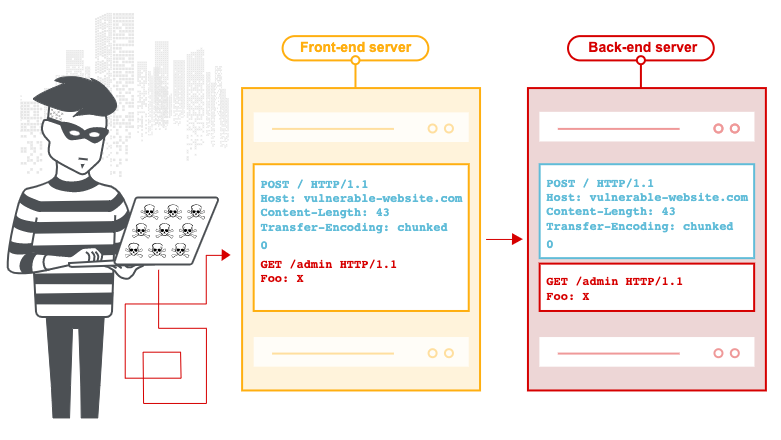
The actual attack that uncovered the vulnerability in AWS API gateway was very simple: Thatcher added X-Forwarded-For abcd: z to the header for HTTP requests, which bypassed the AWS IP address restriction policies in AWS API Gateway.
At its most serious, the vulnerability could allow an attacker to use HTTP header smuggling to sneak phony headers to the backend and launch a cache poisoning attack on the server. This in turn could allow the attacker to create their own API and return malicious content. Not the easiest one to exploit.
AWS has since fixed the vulnerability.
Guide: Kubernetes API Access Security Hardening
In any given Kubernetes deployment, the “control plane” is a component of critical importance in a Kubernetes instance, with the Kubernetes API being the gatekeeper to any and all operations that get executed within the instance. As such, the access to this API must be carefully controlled using strong authentication and authorization techniques.
Teleport has put together a concise guide in which they provide recipes and best practice guides for hardening and securing Kubernetes deployments. The article provides detailed guidance on the following core topics:
- Kubernetes API network access best practices
- Kubernetes API user account management best practices
- Kubernetes API access authentication best practices
- Kubernetes API access authorization best practices
- Securing access to Kubernetes Kubelet
- Additional security considerations for API access control
With any complex software system, administrators are encouraged to be fully aware of the default configuration and its security implications, and are well-advised to follow such a guide to implementing the quick wins to harden their installations. If you work with Kubernetes, or are interested in it, do take a look.
Report: Time to take API security more seriously
The importance of API security to our modern economy was highlighted this week in a feature by Forbes on why it’s time to take API security seriously. Perhaps for regular readers of this newsletter, the conclusions do not come as a surprise, but it is heartening to see this topic given prime-time coverage in the mainstream media.
Forbes concludes that IT leaders would do well to focus energies on the following key areas:
- Consider all APIs a threat.
- Keep an accurate, up-to-date inventory of APIs.
- Look inside the luggage.
- Get serious about DevSecOps.
Forbes’ conclusion is precise and to-the-point:
“the best defense is to raise awareness as broadly as possible in your organization so that everyone whose job relates to designing, building and deploying software understands this enemy.”
Opinion: Predicting the next OWASP API Security Top 10
Finally, a regular contributor to this newsletter, Jason Kent, provides some predictions on what a new OWASP API Security Top 10 might look like. The previous listing is from 2019, and two years can be a long time in tech, so it will be exciting to see how it eventually gets updated.
The key takeaway from Kent is the focus on shifting left in relation to API security. He predicts that both insecure design and data integrity failures will be added as new entries to the API Security Top 10. Unsurprisingly, identity and authentication failures and broken access control are likely to remain the two highest priority issues affecting API security.
If you are the betting kind, you could start considering your own opening antes.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy