This week, we have articles on the surge in API attacks as cybercriminals increasingly target financial services and new data on the silent threat of APIs. We have a retrospective on the recent Jumpcloud incident from an API perspective and a great guide on seven things about API security from Philippe de Ryck. We conclude with a look at the OAuth.Tools portal, and another guide from Dana Epp.
Article: API attacks surge as cybercriminals target financial service
In the first of our articles this week on the rise of API security risks, we cover a report from CSOOnline discussing the increase in attacks on APIs and web apps in the financial services industry. According to a report from Akamai, Q2 saw a 65% rise year on year in such attacks, with the majority directed at banks. The report covers over 340,000 servers in 4,000 locations and also reports a rise in Layer 3/4 DDoS attacks.
API security risks pose persistent threats to organizations across sectors, with the growing use of APIs giving attackers more ways to break authentication controls, exfiltrate data, or perform disruptive acts. Of the financial services targeted, banks faced the most attacks at 58%, with other industry segments (Fintechs and insurance) facing ever-growing challenges as the pace of digitization gains momentum.
One of the interesting statistics quoted in the report is their finding that Local File Inclusion (LFI) attacks are the top attack vector, accounting for 58% of attacks, with Cross-Site Scripting (XSS) and SQL Injection (SQLi) coming in second and third place. This data is not borne out by my own research, which reveals that broken authentication and secret leakage are the biggest threats to APIs.
The report concludes that financial services are increasingly integrating third-party risk management into their overall risk management policies to mitigate the risk from third parties.
Article: The silent threat of APIs
The next report on the threat from APIs comes from Richard Bird (CSO of Traceable AI), covering their report on the state of API security in 2023. The report covers findings from 1,629 respondents from over 100 countries and six major industries. The headline figures are startling: 74% of organizations have experienced three or more API-related breaches in the last two years. The expansion rate of connected organizations is also highlighted by the statistic that over 88% of organizations have over 2,500 cloud applications.
Bird’s key takeaway is that APIs contribute to increased unknown risk for organizations. Although organizations are conscious of the risk of APIs, over 40% of them reported that they only test a small fraction of their APIs for vulnerabilities. Without being able to measure API risk, it becomes challenging for organizations to detect and contain API risk.
The report highlights how APIs are driving the expansion of the attack surface, namely:
- Sheer volume of APIs: The volume of APIs continues to grow exponentially, and this is not restricted to public-facing APIs, as internal and 3rd party APIs are growing at similar rates.
- Diversity in API types: APIs are a long way from being a uniform attack surface since many protocols are in play and many more deployment and configuration options. This creates a growing and complex attack surface, with 58% of respondents claiming that APIs increase their attack surface.
- Varied perceptions about API risk: Despite the high prevalence of API-based incidents arising from poor security, many respondents sought to downplay the risk, with 8% feeling it was negligible.
- Unknown risk and the expanding attack surface: As highlighted earlier, the unknown attack surface makes it harder to contain and manage risk, with many organizations being unaware of their attack surface.
For Bird, the biggest risk to organizations and their connected digitization strategy arises from unknown (and hence) unquantified risk.
Article: What happened with the Jumpcloud incident
Recently, we covered an incident on the Jumpcloud platform where users were advised to rotate API keys “out of an abundance of caution,” and this week, we have a post-mortem report on the incident from TechRadar.
The first concern was the lack of transparency from JumpCloud in communications around the incident. The initial communication was a brief note to rotate API keys and an apology, but no further explanation was given, leading to speculation in the wider community. According to the report, the breach was a result of a spear-phishing campaign that was able to gain access to Jumpcloud’s internal infrastructure and target a subset of its customers. This left JumpCloud with no option but to force a reset of all customer API keys.
JumpCloud has since provided an update to customers, reporting that only a few customers and systems were impacted and that the threat had now been totally contained. The attack highlights an increasing trend where attackers are targeting cloud service providers due to the rich nature of the assets, including SSO, MFA, password management, and device management that these providers hold. As per this attack, often the easiest attacks are simply to steal API keys and use those to infiltrate downstream services.
Unfortunately, there is no silver bullet in minimizing the threat of stolen or leaked API keys and tokens. Typical guidance includes ensuring a robust exchange or revocation process exists, minimizing the lifetime of keys and tokens, and reducing the scope of tokens to reduce the impact of a lost or stolen token.
Guide: Seven things about API security
The next guide is destined to be a favorite with readers and features Dr. Philippe De Ryck discussing seven things about API security from a recent talk he gave. Philippe has kindly made the slides available, and anyone working in the realm of API security is advised to grab a copy and understand the content.
As a case study, Philippe uses the example of how not to do APIs from the Yunmai smart scale (one of our most popular breach reports). Philippe uses this case study to illustrate why developers so frequently make mistakes in implementing authorization and provides some easily consumable patterns for how to get it right the first time around.
Philippe’s slides then go on to cover his seven key things about APIs, namely:
- Centralize complex authorization logic – avoid so-called spaghetti code implementing authorization in various disconnected locations in the code base.
- Empower audibility – make the intent behind coding decisions explicit and obvious to aid effective code reviews.
- Avoid sensitive data exposure – be careful of your ORM and helper functions like .to_json().
- Avoid leaking information – avoid exposing the implementation internals of your API.
- Implement rate limiting – one of the simplest and easiest ways to prevent your APIs from being abused.
- Mitigate guessing attacks – make identifiers hard to guess using complexity and randomness.
- Protect against SSRF – use CORS to help protect against SSRF.
Another great resource from Philippe (be sure to check out his many other excellent free resources), and a big thanks to him for his contribution to the community.
Tools: OAuth.Tools goes beyond just JWTs
Useful API tools are always popular with our readers, and this week, we have news of the excellent OAuth.Tools from our friends at Curity.
Although ostensibly a JWT editing tool, it offers a wealth of other features that will be useful to anyone working with JWTs, OAuth, and OpenID Connect. The diagram below shows some of the key features, including examples of flows for popular OAuth flows and token management:
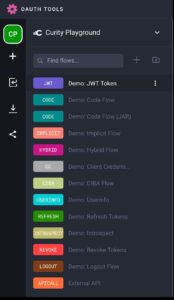
This is a really powerful tool, and I recommend bookmarking it if you are involved in wrangling JWTs, OAuth flows, and OpenID Connect. Thanks to Curity for making this available to the community.
Guide: Finding hidden API endpoints using path prediction
As has become a tradition of late, we finish this week with another guide from Dana Epp looking at how to find hidden API endpoints using path prediction.
Hidden API endpoints are entry points within an application’s API that are not documented or publicly announced for various reasons. They can possess vulnerabilities, and hence, understanding and locating them is a critical aspect of bolstering API security.
Path prediction is a technique that involves studying the URL structure, endpoint patterns, and other discernible indicators within the API documentation or code to guess potential hidden endpoints. Path prediction is a powerful technique for discovering undisclosed or weakly secured endpoints.
Dana highlights how developers focused on good REST design principles will tend to produce APIs with fairly predictable endpoints. From a red-team perspective, being able to predict API endpoints is a valuable skill.
Another fun read from Dana. Thanks for the contribution.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy