This week, we have articles on the rise of API attacks that target shadow APIs, how API attacks on on e-commerce sites leak PII, views from Trendmicro on the importance of API runtime security, and a guide on API penetration testing.
Article: API attacks target shadow APIs
First up this week is a report from DarkReading on recent research showing that approximately 5 billion (31%) malicious transactions targeted shadow APIs (unknown, unmanaged, and — most importantly — unprotected APIs).
The report ranks the top three threats to APIs, based on monitoring 20 billion API transactions in the first half of 2022:
- The top threat to APIs was epitomized by the 5 billion malicious requests observed targeted shadow APIs. These attacks varied greatly in nature: from highly volumetric bots trying to scrape sites for deals, to fraud using stolen credit card, to simple credential stuffing attacks.
- The next most prominent threat was API abuse, based on the 3.6 billion attacks blocked by the threat research team. API abuse is generally defined as attacks against properly coded and inventoried APIs, that is, APIs which are not typically considered vulnerable as per the OWASP API Security Top 10 list. The most common attack vector associated with abuse cases is the redemption of gift cards or the creation of fake accounts on dating and shopping applications.
- The third most prominent threat was a combination of three common API threats: credential stuffing, shadow APIs, and sensitive data exposure. By using these three vulnerabilities in combination, attackers could mount sophisticated attacks to exfiltrate data from APIs.
The report also highlighted the rise in account takeover (ATO) attacks. The researchers recorded 1.17 billion malicious login attacks against API endpoints. Also highlighted is the significant cost associated with a successful account takeover attack — in this case, approximately $193 million.
This an interesting report indicating the importance of both strengthening your APIs by secure design and coding, while also protecting them against abuse.
Article: PII leaking from e-commerce APIs
We frequently feature API security news from the financial services sector. By way of a change, this week, we have a great article from Trend Micro on the challenges to the e-commerce sector posed by unsecured APIs.
The report specifically draws attention to PII leaked through APIs, such as name, email, address, purchase history, and other shopping preferences. The report also highlights that this particular combination of sensitive information could allow attackers to launch very sophisticated fraud campaigns targeting consumers based on their preferences. Best lies have some truth mixed in them: it would be harder for the victims to spot these attacks as including correct details lends the air of validity to the ruse, making this highly attractive to attackers.
The report covers two specific scenarios for e-commerce providers, third-party logistics (3PL) and fourth-party logistics (4PL), as shown below:
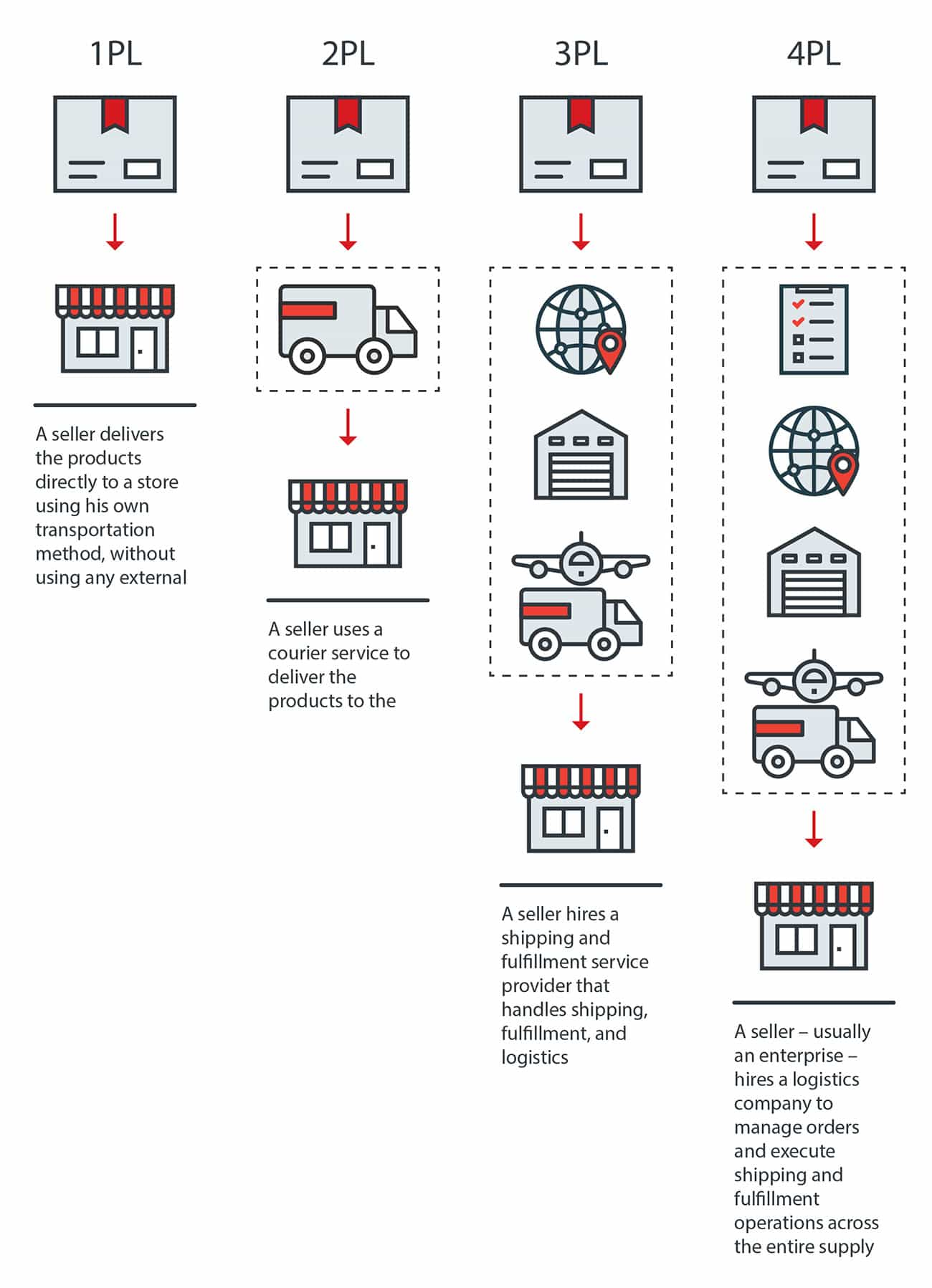
In the case of 3PL, the merchant uses a 3PL provider to handle the logistics of shipping the product from the merchant to the customer. In 4PL, the 4PL provider handles the entire supply chain. To create these sophisticated supply chains, the merchant must pass shipping and order information downstream to the logistics provider. Unfortunately, as the report reveals, this is often done in an insecure fashion, which can lead to leaked PII.
The report identifies several vulnerabilities that are common to supply chain API implementations, such as:
- Passing customer information in URLs as query parameters
- Allowing unauthenticated (guest) users to check other users’ order status using a unique URL
- Using session cookies that do not expire
All these can allow attackers to glean information on other users that can then be used for nefarious purposes.
To improve the security posture of e-commerce APIs, the report makes the following recommendations:
- Only transmit the bare minimum of data to downstream providers, to prevent excessive leakage.
- Use string encryption (such as TLS) to prevent information theft in transit.
- Use standard and robust authentication schemes, such as OAuth2.
- Implement object-level authorization checks at the code level to ensure finely-grained authorization control.
- Use multi-factor authentication methods where possible.
- Avoid using unknown browser extensions to prevent theft of PII and session cookies.
It looks like the e-commerce sector has many of the same challenges that are familiar from other sectors — be sure to follow the recommendations above.
Article: Five reasons you need API runtime security
Next, we have the thoughts of NordicAPIs on why API runtime security is important as part of an overall API security strategy. The article highlights the tremendous value of a strong shift-left API security initiative. However, this on its own is not enough: the author also stresses the importance of complementing this approach with a shield-right strategy.
In summary, the author provides five main reasons why API runtime security (shield-right) is important:
- API testing tools cannot detect all business logic flaws.
- Runtime security can protect API assets already in production, minimizing the risk of shadow or zombie APIs (circling back to our first piece this week).
- Shield-right provides immediate cover for internal APIs that end up re-purposed for public, external use.
- Third-party or COTS APIs cannot easily be modified to eliminate security flaws.
- Even a perfectly secure API can be abused ( again, as discussed in the first article).
In my opinion, the combination of a shift-left, shield-right strategy provides the best of both worlds.
Article: API penetration testing
Finally, we have a popular topic for readers of this newsletter, namely API penetration testing. This quick read calls out the differences between web application pentesting versus API pentesting — the author’s view is that they are significantly different. Organizations should employ specialist skills and techniques for API pentesting.
The author emphasizes the importance of correctly scoping the API pentest, taking into consideration the following:
- Deciding if a client is necessary to generate and send requests to the API, is a dedicated test fixture necessary or can an existing client be used?
- Understanding what API documentation exists and what can be provided.
- Understanding roles, authentication methods, and API design.
If you want to know more about API security penetration testing, it is worth watching the webinar I hosted on the topic last week with FORTBRIDGE.
Event: 42Crunch at API World 2022
API World is the world’s largest vendor-neutral API-specific conference, and this year it takes place in San Jose from the 25th to the 27th of October.
Join Isabelle Mauny (co-founder and Field CTO of 42Crunch) at the conference where she will be presenting on:
- API Security 101: Top API Vulnerabilities and How to Address Them
- How a Combined Shift-Left and Shield-Right Approach Delivers End-To-End API Security
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy
