This week, we check out the API aspects of the recent SolarWinds and PickPoint breaches. Also, we have a review on how to shift API security left with GitHub and 42Crunch and an introduction video on GraphQL security.
Breach: SolarWinds
The SolarWinds hacking reported this weekend was not API-related as such. It was a supply chain attack in which hackers (likely a state actor) managed to add their backdoor in one of the DLL files of SolarWind’s IT monitoring and management software, Orion. After a dormant period, the malicious code would contact the command and control center (C2) to get further instructions and execute them. This was in turn used against SolarWinds’ customers, including multiple US government agencies.
What did catch our eye was the API angle to the story:
“The C2 traffic to the malicious domains is designed to mimic normal SolarWinds API communications.“
The attackers made an effort to make their traffic look like normal SolarWinds API traffic. This allowed them to mask the activity and avoid getting detected by any anomaly detection systems, like machine learning or artificial intelligence.
Breach: PickPoint
Attackers opened 2,732 PickPoint package lockers across Moscow. These are lockers that customers can use to pick the goods that they buy online.

Because this was an actual successful attack rather than ethical research, the details are scant. However, what we know makes it look like an attack against APIs:
- In the videos posted on the internet, one can see that the lockers get opened one by one, rather than all at once.
- The attack was remote and happened across the city, with no attackers physically walking to the locker locations.
- PickPoint is API-driven, with parts of their APIs related to vendor integrations publicly documented.
Considering these factors, this looks very much like an enumeration and API1:2019 — Broken object-level authorization (BOLA/IDOR) attack against the APIs. Attackers likely found a way to authenticate against the API and then enumerate locker or package IDs on the API calls to open the corresponding lockers.
To avoid such vulnerabilities:
- Make enumeration hard, do not use sequential numbers.
- Use rate limiting and monitoring to prevent using scripted attacks.
- Implement authorization, not just authentication, to make sure that the caller has legitimate rights to the operation on that particular object.
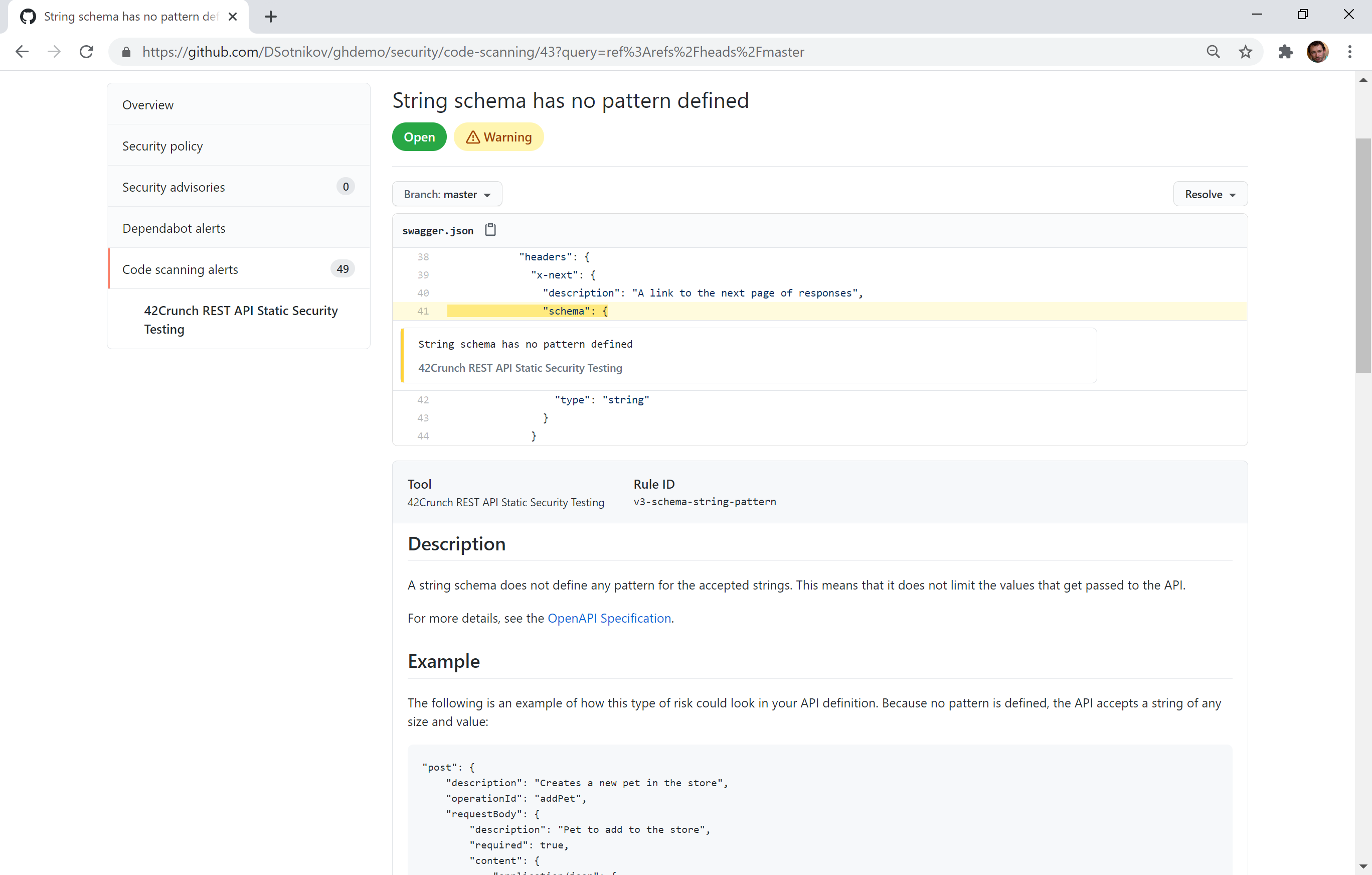
Review: API security with GitHub Code Scanning and the 42Crunch GitHub Action
Security issues are much cheaper to catch and fix early in the development cycle, and API security is not an exception.
Mitch Tulloch at TechGenix has posted a review on using GitHub Code Scanning and the GitHub Action from 42Crunch, REST API Static Security Testing, to locate and fix API code vulnerabilities before they reach production.
Video: Finding Your Next Bug: GraphQL
GraphQL APIs are still significantly less frequently used than REST APIs. However, GraphQL is getting traction, yet many developers are less aware of the potential security implications of GraphQL.
Katie Paxton-Fear has posted a new video tutorial that can be valuable as a quick introduction to GraphQL security. She covers, for example, the following topics:
- The basics of GraphQL
- Queries
- Mutations
- Fragments
- Metafields
- Introspection
- Tools
- Typical security bugs and how to find them
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy