This week, we check out the vulnerabilities fixed in EU’s eIDAS (electronic IDentification, Authentication, and trust Services) system and Cisco routers, how Instagram is seeking to avoid the privacy controversies that Facebook itself has had, and interesting predictions from Gartner’s latest API report.
Vulnerability: EU eIDAS
EU has patched the reference implementation of the eIDAS system that the member states use for international transactions and signatures.
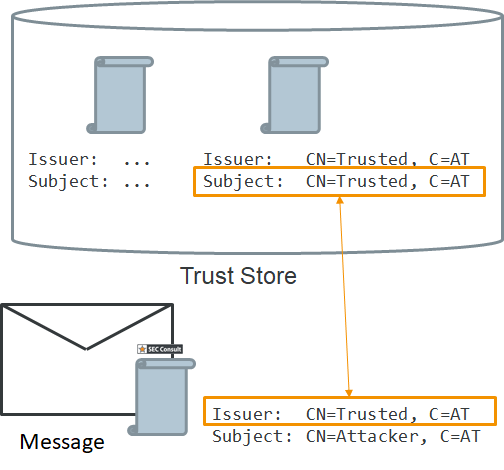
Sec Consul found a flaw in certificate checks that allowed anyone to forge their identity in the system. The certificate signatures of SAML responses were validated by simply matching the Distinguished Name (DN) of the certificate with the local trust store, not the public key of the issuer certificate. If attackers crafted a SAML response where the certificate DN matched one in trusted certificates, they could authenticate as anyone.
This is not the first time improper certificate verification is leading to a vulnerability. TwitterKit SDK had one just a few weeks ago. The best advice here would probably be to not reinvent the wheel and use popular established libraries and products.
Vulnerability: Cisco Routers
Cisco has fixed the REST API module for its routers running Cisco IOS XE software. An improper check in the REST API authentication could allow an unauthenticated access to the device.
Attackers could craft a malicious HTTP request and send it to the authentication service. This could cause the service to return the token-id of another, authenticated user that the attackers could then use to execute privileged actions through the REST API.
Unfortunately, Cisco did not provide further details, so it is hard to have specific lessons learned derived from the case.
API program changes: Instagram
Instagram is locking down its API as is moves to use the Facebook Graph API. To give users better transparency and control over their data, Instagram:
- Removes location from API data
- Separates profile and media access
- Gives users an UI where they can review all apps that have API access and set access levels for them
This is an interesting case of the vendor cleaning up an existing API to remove the data exposure not required by the business (and thus partly mitigating OWASP API3:2019 — Excessive data exposure), retrospectively adding scopes for granular data access, and making API access visible and controllable by the end users.
Something that many other vendors can learn from.
Analyst Forecast: Gartner
Gartner has published their report “API Strategy Maturity Model”. Among other interesting things, the analysts Mark O’Neill and Saniye Alaybeyi lay out the following noteworthy statistics:
- By 2021, exposed APIs will form a larger surface area for attacks than the UI in 90% of web-enabled applications. The increase will be significant from 40% in 2019.
- By 2023, over 50% of B2B transactions will be performed through real-time APIs versus traditional approaches.
Both the numbers highlight the increased importance of API security for businesses as the technology changes.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy