It is all about vulnerable APIs this week. We are looking at the ones in Plenty of Fish dating app, Sony’s SonyLIV services, and Microsoft SharePoint. Also, there is a big leak of Facebook users’ phone numbers presumably harvested via APIs.
Vulnerability: Plenty of Fish
Dating apps contain highly personal information and thus are a target of hacking. We have already covered dating app API vulnerabilities in our issues 18, 44, and 45.
This time, there is a leaky API in Canadian Plenty of Fish app. The service is quite popular with about 100 million registered users.
Although the application itself allows users to hide their personal information, the API behind it does not. API calls return sensitive personal information including: first name, zip code, income level, parents’ marital status, and number of siblings.
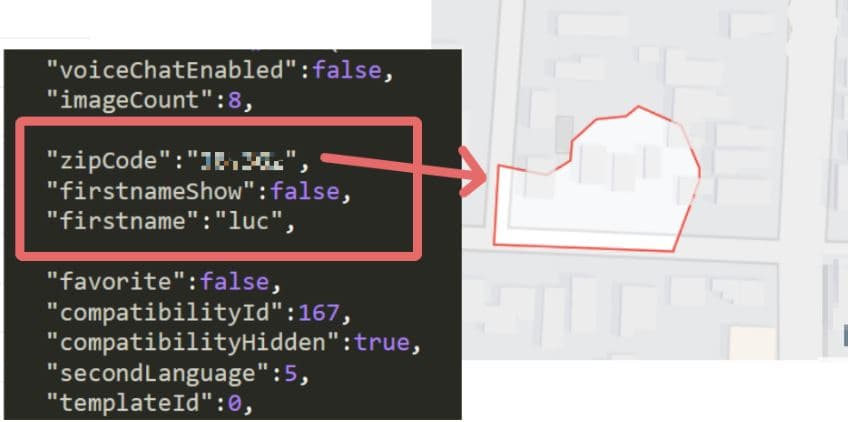
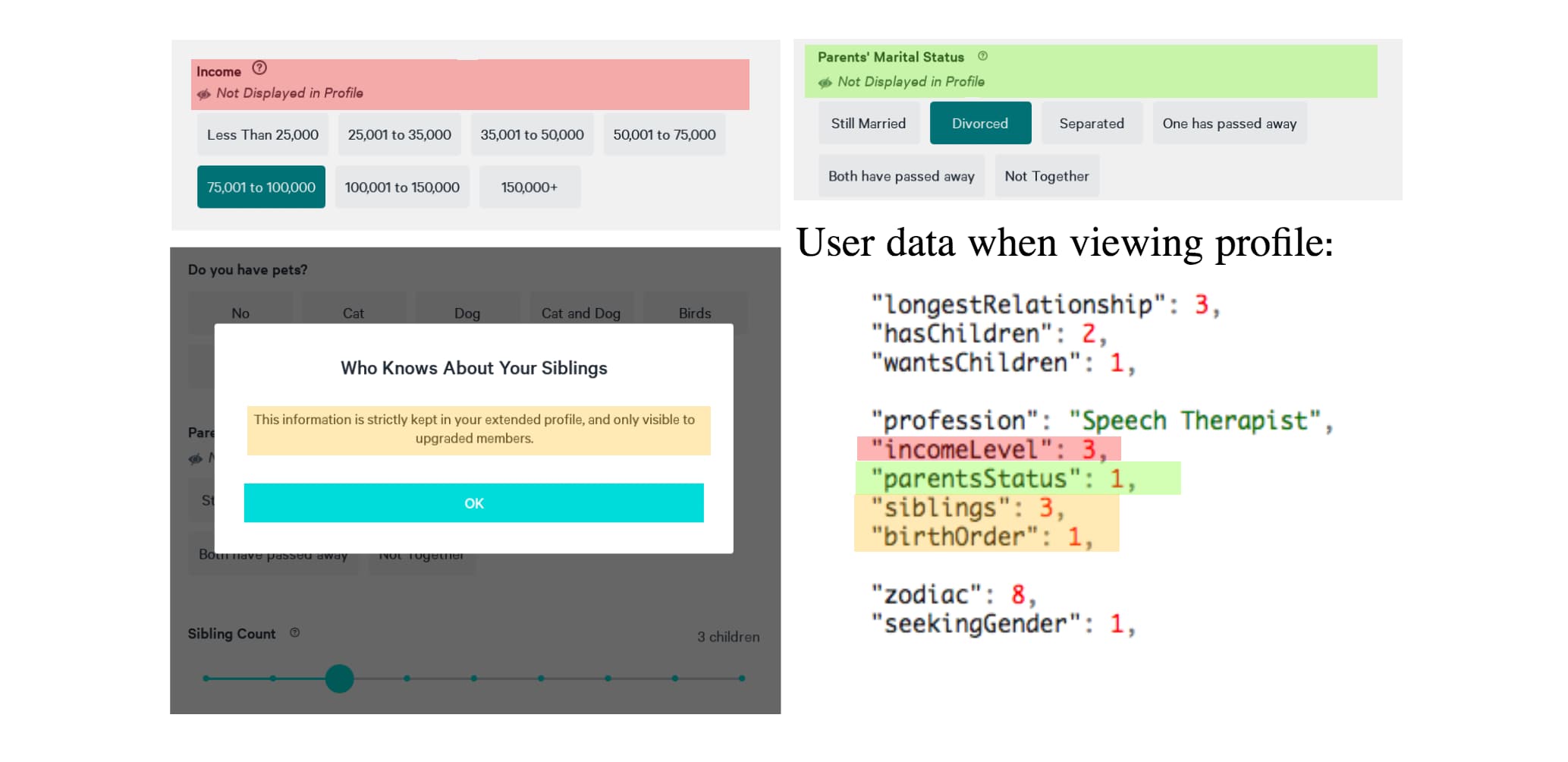
In OWASP API Security classification, this is an example of API3:2019 — Excessive data exposure.
If you are an API provider, you need to avoid client-side data filtering and protection. Treat your APIs as your user interface. Only return the data that is fine for users to see.
Vulnerability: SonyLIV
SonyLIV is a popular internet television channel and subscription service operated by Sony Pictures Networks in India and Pakistan. Their app has more than 100 mln installs on Google Play Store.
Just like recently reported Droom issue, SonyLIV has an API vulnerability in their social login implementation. When logging in with Google Authenticator, Ehraz Ahmed found that he could log into another user’s account. To do that, he just had to put the other user’s email address in the corresponding parameter field.
OAuth 2.0 is a frequently used delegated access mechanism. However, frequently its use gives vendors a false sense of security. When poorly implemented, it can still leave your systems wide open. Use standard off the shelf implementation whenever possible or seriously audit your implementation for completeness and security best practices.
Vulnerability: Microsoft SharePoint
Microsoft released a patch to SharePoint API vulnerability.
The API was vulnerable in versions 2010 SP2, 2013 SP1, 2016 & 2019. Crafted API response allowed attackers to read arbitrary files on the server.
Unfortunately, public details on the actual vulnerability are scarce. From the looks of it, it appears to be some kind of data validation issues.
Make sure that you thoroughly define and enforce data schemas, patterns, and ranges of all your API payloads.
Data Harvesting: Facebook
Phone numbers of 267 million of Facebook users have been shared in a hacker online forum.
Presumably, these have been harvested via Facebook APIs which until 2018 gave access to that data.
If you are an API provider:
- Do not expose more data than absolutely needed
- Limit access to sensitive personal data
- Prevent data enumeration
- Have logging, monitoring, and alerting in place
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy