This week, we have news of a critical API vulnerability that allowed a researcher to demonstrate a proof of concept attack allowing remote vehicle takeover. We have articles on three reasons why QA teams should learn API hacking and the new changes GitHub has made to API versioning to future-proof client code. Finally, we have a great walkthrough of the OWASP API Security Top 10 using the vAPI vulnerable application.
Vulnerability: Critical API vulnerability allows remote control of Hyundai and Genesis vehicles
First up is the excellent research from Sam Curry into an API vulnerability affecting the Hyundai and Genesis vehicle range. Curry created a proof of concept detailing the exploit and described the steps in detail on this Twitter thread. Most worryingly, the proof of concept demonstrated how the vehicle engine could be controlled remotely. Fortunately, the researcher responsibly disclosed the vulnerability, and the manufacturers resolved the issue before the details were publicized.
I covered this vulnerability in detail in 42Crunch’s webinar on the breaches in H2 2022 in December. The root causes of the vulnerability are twofold: a lack of input sanitization and poorly constructed email validation regular expressions. The researcher discovered that once he had a valid registration on the web portal of the vehicle, he was able to tweak the registration email address (by adding control characters), which would issue a JWT using this “fake” email. So simply by knowing a user’s email, an attacker could spoof a login and gain a token that would allow full vehicle access.
The screenshot below demonstrates the creation of a token with a tweaked email:
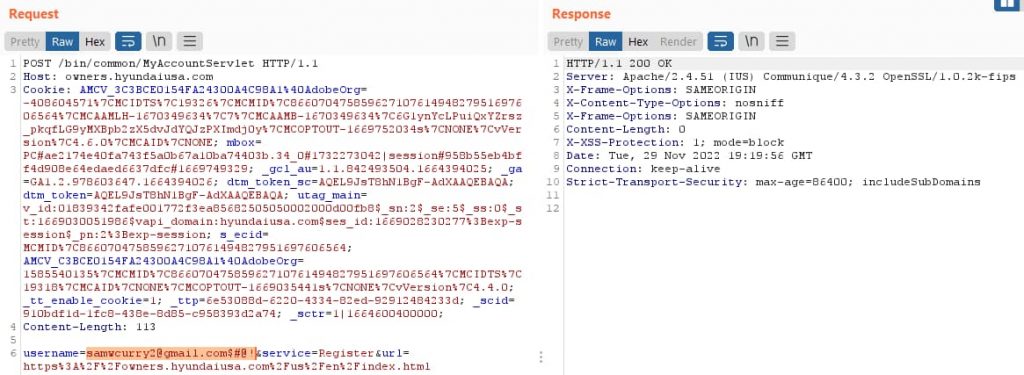
The key takeaways here are:
- Never trust user input: in this case, an attacker could provide a “tweaked” email address that was not sanitized adequately.
- Use hardened/trusted regular expressions: the email validation methods accepted clearly invalid email addresses.
- Segment your access control: in this case, the management portal issued a “super token” which allowed engine control. For such high-risk methods, use an out-of-band mechanism or a higher-privilege token.
Article: Three reasons QA teams should learn API hacking
A regular contributor to the newsletter Dana Epp (@DanaEpp), recently published another excellent blog. This time he shares his thoughts on the value of quality assurance (QA) teams learning the basics of API hacking and using an offensive mindset.
As shift-left is embraced and developers are increasingly empowered to test their own software, many of the more elementary security flaws can be detected early in the lifecycle. Unfortunately, many of the more complex business logic security vulnerabilities require expert skills, and the best-placed team to do such testing is the venerable QA team. However, typically, these teams do not have the perspective of an attacker, namely an offensive mindset. Epp suggests three top reasons a QA team should develop such skills, namely:
- You’ll deliver more value: from a personal career development perspective learning diverse skills such as API hacking is only going to stand you in good stead for future opportunities. The shortage of skilled security professionals is likely to persist, and having experience in this field is a big plus on your resume.
- Becoming the villain turns you into the hero: often, the QA or test team is seen as a blocker to timely software delivery. However, the only thing worse than a delayed delivery is a delivery with a glaring security flaw. As the last line of defense in the testing chain, you could save the day for your developers and company.
- Security is everyone’s responsibility: although something of a cliche, that does not invalidate the truth in the fact that security is everyone’s responsibility, or at least one should not assume somebody else might be responsible. You might very well be that person, so make sure you test like it is!
In my experience of working with testers across various industries, I can only echo these thoughts, particularly the first point. I always used to know who the most security-savvy testers were and ensured they were on my projects.
How do QA teams get started developing an offensive mindset and learning to hack? For openers, Epp has an excellent guide on API hacking resources, which I’d start with, and my suggestions would be as follows:
- Learn how real-world hacks take place (please encourage your QA times to subscribe to this newsletter).
- Start learning the tools (Postman, Burp Suite, etc) with some deliberately vulnerable apps.
- Learn some hands-on skills and perhaps become certified — the API Penetration Testing course from Corey Ball comes highly recommended.
Happy hacking!
Article: GitHub unveils next generation API versioning
API versioning is important for your API strategy to ensure that you can update your API to add new features, but at the same time, ensure that you do not break existing clients and integrations due to breaking changes. Typically organizations have relied on basic numeric sequencing (i.e. a v1, v2, v3 instance of an API), but this approach lacks granularity, particularly when the provider wants to make a breaking change. GitHub has recently introduced a change to its versioning strategy, which is now based on a date-based versioning scheme.
It works as follows — if no version is specified, the latest version will be used. A client can use the X-GitHub-Api-Version header to force a specific API version. GitHub guarantees that the previous version of an API will be available for a minimum of 24 months.
Why does API versioning matter to API security? On the positive side, having a formal system of API versioning means there is less likelihood of shadow or zombie APIs since there is a formalized process around the governance of APIs. On the negative side, a more fluid versioning system such as that adopted by GitHub means there are likely to be many more versions of APIs in production, which all need to be tracked and monitored for security issues.
It will be interesting to see how the industry adapts to GitHub’s new strategy — I can see both good and bad in it.
Guide: OWASP API Security Top 10 walkthrough
Finally this week, we have a great walkthrough of the OWASP API Security Top 10 from Grant Ongers (@rewtd) using the excellent vAPI vulnerable API application. The guide uses vAPI running in Docker and demonstrates each of the Top 10 using Postman and ZAP as the base tools.
It’s a very written walkthrough with plenty of detailed screenshots showing the attack setup and the stages of the exploit. Not only that, but he also provides great explanations of the underlying API issues.
Thanks to Grant for contributing this excellent learning resource to the community.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy