This week, we check out the recently fixed vulnerability in Google Cloud Deployment Manager, and how to penetration test OAuth 2.0. On a higher level, we have Gartner’s classification of API security technology, and a recording of a panel discussion on API security.
Vulnerability: Google Cloud Deployment Manager
Google Cloud Deployment Manager is an infrastructure management service that makes it simple to create, deploy, and manage Google Cloud Platform resources. Ezequiel Pereira found an API vulnerability in Google Cloud Deployment Manager and collected his $31K prize from Google as result.
Pereira found a way to make it invoke Google internal APIs that he was not supposed to invoke:
- He could invoke non-production versions of the GCDM API called
dogfoodandstagingthat provided him internal information on the workings of the system. A classic example of API9:2019 — Improper assets management in the OWASP classification. - He used these API versions to figure out how to invoke the APIs of Google’s internal services, including Global Service Load Balancer (GSLB).
- He took the advantage of the authentication logic that made calls through the service account of the service if user authentication failed.
Beware of non-production versions of your APIs being accessible externally and having in turn access to production systems and data. Such non-production versions are as much “the real thing” as the production versions and require the same considerations. Also, be very careful how you design your authentication flow.
Resources: PenTester’s Guide to OAuth 2.0 Authorization Code Grant
Maxfield Chen has published an extremely detailed penetration testing guide for OAuth 2.0 Authorization Code Grant. This is by far the most popular way of using OAuth 2.0, which in turn is the de facto standard of web and API access control. Yet, OAuth can be extremely confusing and there are many ways how OAuth implementations can go wrong.
Chen does a good job quickly recapping the flow and its components. Most importantly, he then proceeds to the main exploit scenarios and covers testing steps for each of them:
- Insufficient URI validation
- Referrer header leaking code and state
- Access token stored in browser history
- Other access token leaks
- Client secret leaks
- Lack of state
- Insecure state
- Reused state
- Invalid state validation
- Reusable authorization codes
- Access token stored in JavaScript
- Implicit grant coercion
-
307redirect attack
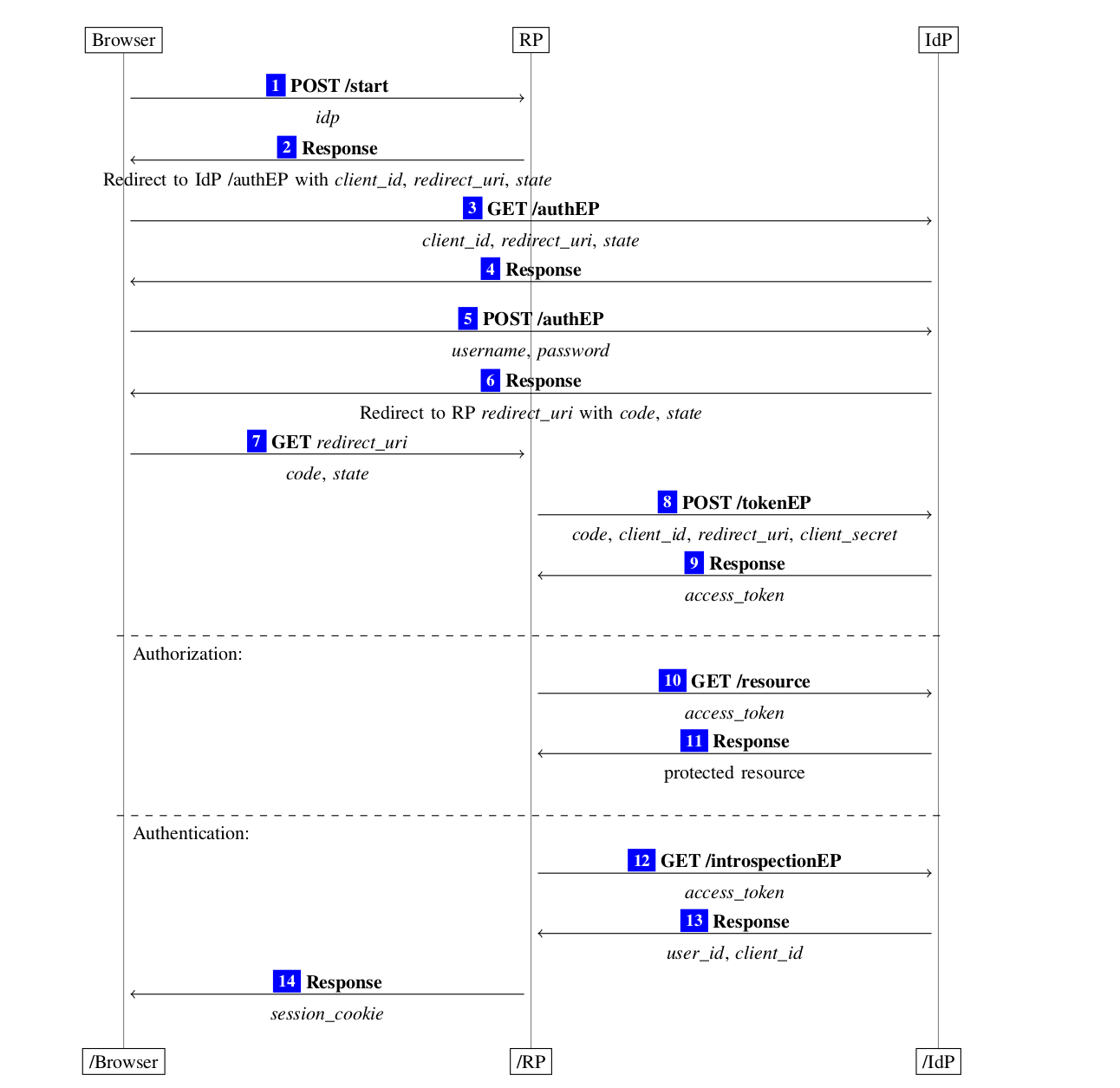
Definitely worth a closer look, if not as a pentester then as a reminder of what could go wrong.
Analysts: Gartner’s Solution Path for Forming an API Security Strategy
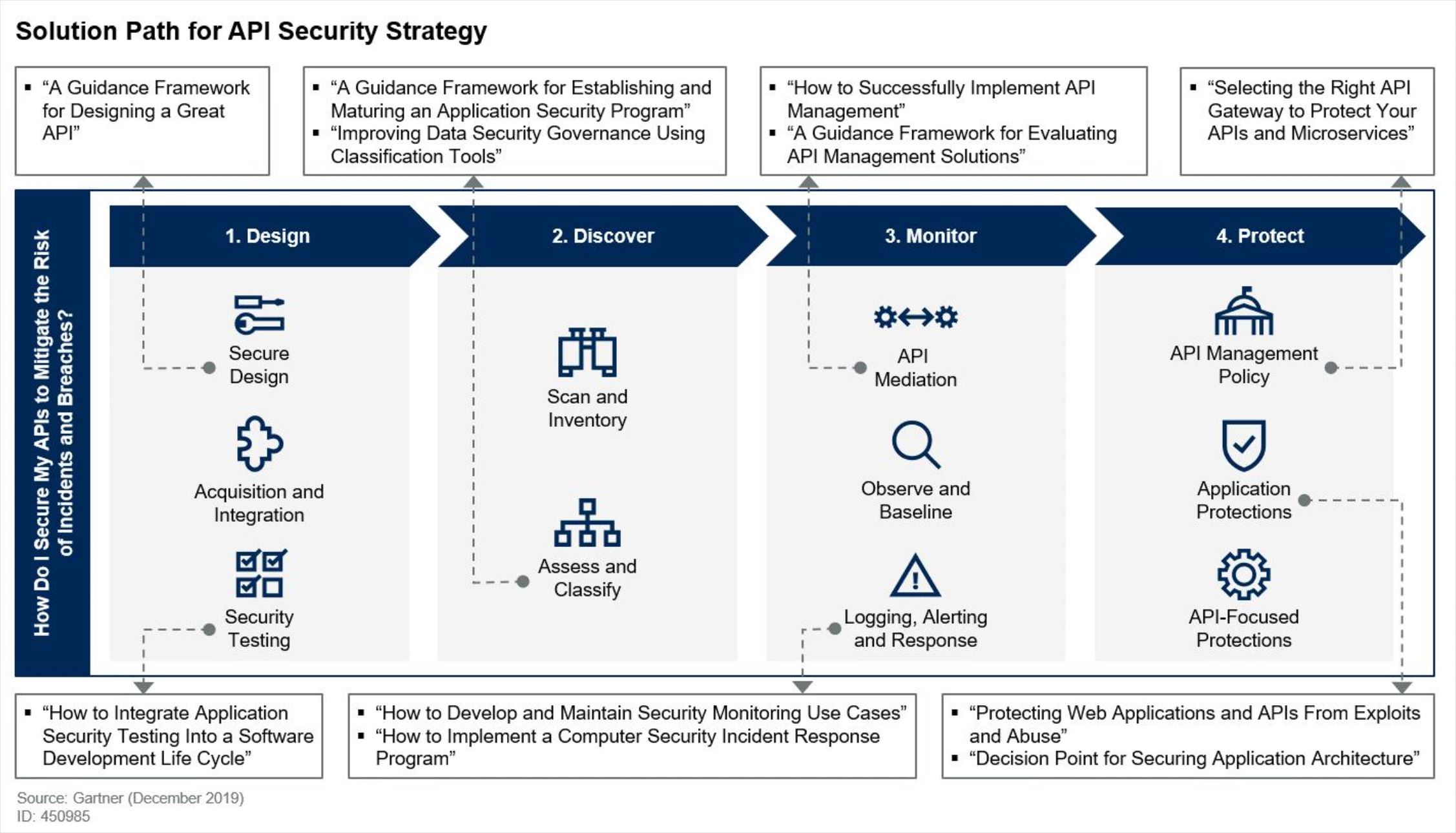
A few months ago, Gartner published their report “Solution Path for Forming an API Security Strategy” by Michael Isbitski, Frank Catucci, and Kirk Knoernschild. This report helps identify the different elements in the puzzle of the API security tooling.
The full report requires subscription, but Michael has just posted a quick summary:
API security continues to be top of mind for security practitioners as APIs underpin modern application design, data exchange and system integration. We published a research note towards the tail end of 2019 that provides guidance around API security strategy. There is no shortage of free and paid tooling in this space, but they address specific aspects of the overall API security puzzle. Secure design, testing, discovery, classification, monitoring, mediation and threat protection require a multi-pronged approach that cannot be satisfied with one technology, nor is it one size fits all for organizations. API security is also not just use of TLS to protect data in transit or access control to restrict who can access a given API. These are controls that improve security, but they should not be where your API security strategy begins and ends.
And there is a nice diagram to make a sense of the categories in which different API security tools fall. Obviously, some tools (like the API security platform by my employer, 42Crunch) can cover multiple categories:
Podcast: API Academy’s API Security Q&A Panel
The latest episode of API Academy is all about API security. Bill Oaks, Aran White, and Dmitry Sotnikov answer the frequently asked questions and cover a lot of API security ground in the discussion, such as:
- OWASP API Security Top 10
- Upcoming OpenAPI 3.1 release and why standards matter
- DevSecOps and API security
- Minimal steps for API security
- Why web application firewalls (WAFs) are failing for REST API security
- Machine learning / Artificial Intelligence vs defined API contracts and rules
- Schema validation
- Rate limits and quotas
- API responses: why they are also relevant and not just the requests
- IoT device authentication
- OAuth 2.1
- Containers
- Certificate management
- SAML vs REST
- Monitoring
- API key distribution
- API gateway and API firewall location
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy