This week, we check out three recent API vulnerabilities or breaches and what we know about them, and take a deep dive into cross-origin resource sharing (CORS).
Vulnerability: Cisco
Cisco has released critical security updates to IOS XE Software run by many of its devices.
Two of the issues they have fixed are critical API vulnerabilities allowing privilege escalations of authenticated low permission-level users:
- Lack of input validation in one of the APIs allowed command injection:
“An attacker could exploit this vulnerability by sending a modified HTTP request to the affected device. An exploit could allow the attacker as a read-only user to execute CLI commands or configuration changes as if they were an administrative user.”
- Privileged authentication token leaking in API responses:
“The vulnerability is due to insufficient data protection of sensitive information. An attacker with read-only privileges could exploit this vulnerability by sending a crafted API call. A successful exploit could allow the attacker to obtain a privileged authentication token, which the attacker could use to elevate their privileges to the level of an administrative user on the affected device.”
Both attacks could have been prevented with proper input and output data validation:
- Always strictly define your API inputs and outputs.
- Be very specific: define data types, min and max limits, and strict patterns for strings, schemas for JSON.
- Enforce and test your data validation.
- Review your response payloads to ensure that you only return the bare minimum of data required, and that the responses don’t contain anything damaging, should rogue users make API calls.
We have covered previous API security issues in Cisco products in our newsletters 30, 42, 43, 46, 47, 51, 55, 65, 69, 80, and 96.
Vulnerability: Shopify
Shopify has had a data breach affecting “less than 200 merchants”, according to their own statement. The number of affected customers of these merchants is unknown, but large.
The details in the official statement are scant but TechCrunch got additional information from one of the merchants affected:
One merchant shared with TechCrunch a copy of Shopify’s email notification, which said the company first became aware of the breach on September 15, and that the two employees obtained data that was accessible using Shopify’s Orders API, which lets merchants process orders on behalf of their customers. The email also said that the last four digits of the customers’ payment card was taken in the incident.
Lessons learned here:
- There is no such thing as an internal API! All APIs need to have security in place even if they exist only inside your network, for internal applications and users.
- These “internal APIs” need to have all the regular security mechanisms to prevent abuse: authentication that lets in only authorized users and applications, authorization to prevent access to someone else’s data, rate limiting and monitoring to prevent bulk downloads, and so forth.
Vulnerability: BrandBQ
BrandBQ, a large online fashion retailer in Eastern Europe, has had a massive 1 terabyte data leak. As often happens, this was caused by an unsecured Elasticsearch server that was accessible from the internet. However, this particular incident also had an API aspect to it.
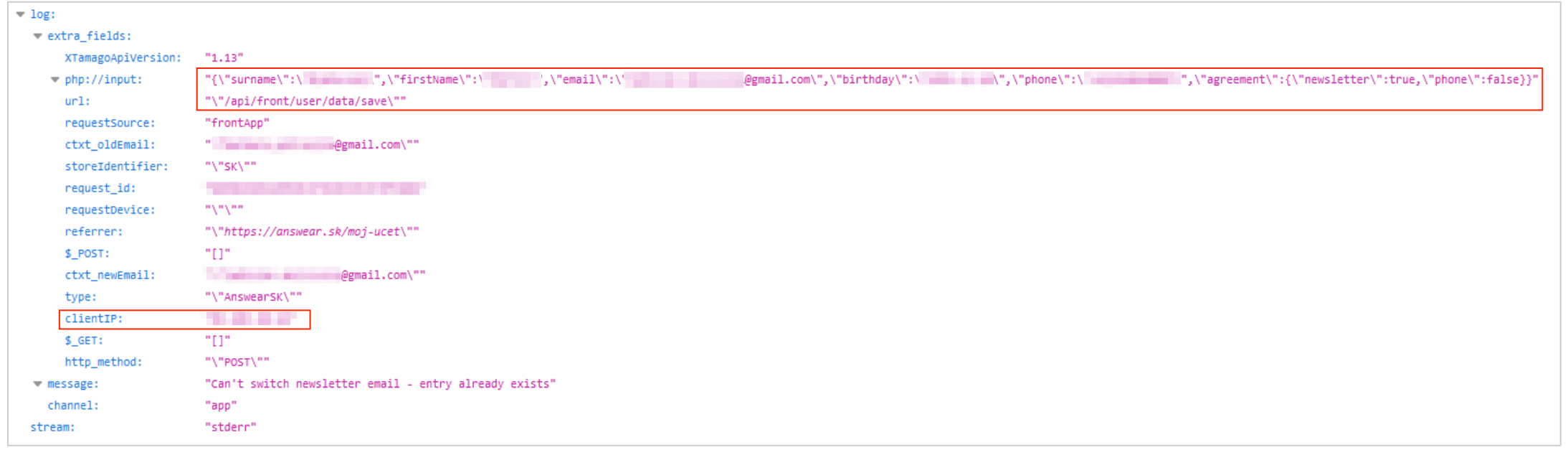
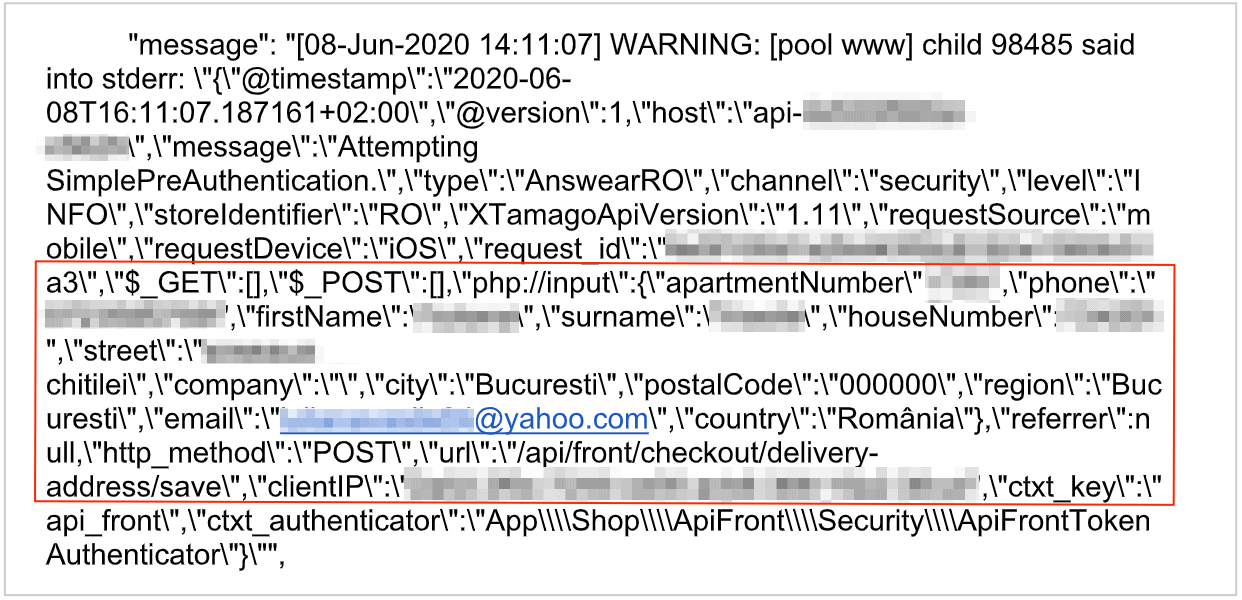
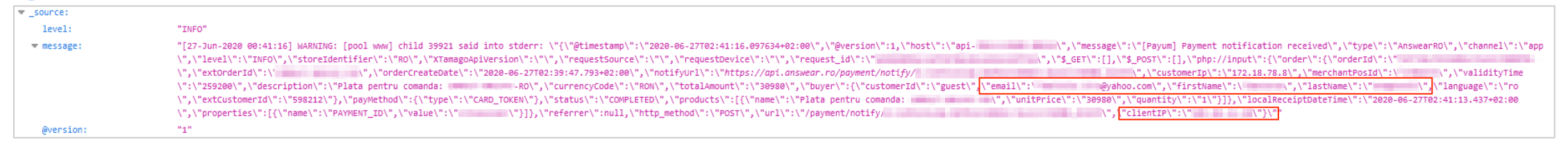
The server contained transaction logs of API calls from both the website and the mobile app of the company. These logs included unredacted personal data on customers, such as names, physical addresses, and email addresses, as well as information on their transactions. The following screenshots illustrate the issue perfectly:
- Website newsletter call:
- iOS app API calls:
- Payment record from an online purchase:
- Always secure your data storage and avoid exposing it directly on the internet!
- Treat logs as sensitive data.
- Avoid over-storing data:
- How long a history of actual transaction logs do you need, and for what reason?
- Can you store aggregated data instead?
- Always redact all sensitive fields!
Security guide: Cross-Origin Resource Sharing (CORS)
Cross-Origin Resource Sharing (CORS) is an important security mechanism that prevents web applications calling APIs that are not part of them.
As with any security mechanism, poor CORS configuration can give false sense of security while leaving gaps that can the attackers can take advantage of.
Ramandeep Kaur and Akash Shetty from IBM Security have published a fairly detailed guide to CORS security:
- What is CORS and how it works?
- What are the common CORS configuration gaps?
- How these gaps can be discovered and exploited?
Definitely worth a read for the dos and don’ts with CORS.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy