This week, we have a very popular API testing checklist aimed at pen-testers, a comprehensive guide to tips & tricks, and resources related to API security and API pen-testing. We also have an article from Cisco on using CVSS to tackle API security, and finally, a 10-year journey in API security vulnerabilities with Ivan Novikov.
Guide: API testing checklist
The excellent checklist from Latish Danawale on API testing was very popular this week with our Twitter followers, and for good reason: it’s filled with invaluable nuggets and gems based on his wealth of experience. The guide perhaps geared more towards API pen-testers, but it’s well worth a skim read for anyone working with APIs to get a perspective on adversaries’ tactics (and talents).
For me, some of the standouts included:
-
“Older APIs versions tend to be more vulnerable and lack security mechanisms” — Always try and discover older API endpoints (like going for
/v1) which may not be as well protected as more recent versions. For defenders, always make sure older, less secure versions of APIs are deprecated and removed from production. - “Mass Assignment is a real thing” — By utilizing object-relational-mappers (ORMs), it is easy for developers to assign request input data to the database layer. However, this can lead to mass assignment vulnerabilities where attackers can overwrite supposedly private data fields.
- “Even if the ID is GUID or non-numeric, try to send a numeric value” — It’s possible that the authorization mechanism tests for both non-numeric and numeric IDs, try both just in case.
- “Mobile Certificate Pinning?” — Older versions of mobile apps may lack certificate pinning, making it a lot easier to reverse engineer the backend APIs.
- “APIs tend to leak PII by design” — Backend often returns overly verbose JSON data and relies on the frontend to mask this data. Unfortunately, this is easy for an attacker to intercept in the browser.
- “GitHub Dorks for Finding API Keys, Tokens and Passwords” — Finally, the author lists a number of “GitHub dorks” to use to try discover API credentials accidentally stored online.
Guide: Resources for API security testing
Next up this week, we have another great resource for API security testers, this time from Momen Eldawakhly who brings us his API Security Empire. Again targeted at API security pen-testers, Eldawakhly focuses firstly on reconnaissance, and then on specific attack techniques against REST, SOAP, and GraphQL APIs.
The mind-map for REST APIs is incredibly detailed and thorough, focusing on each of the OWASP API Security Top 10 in turn. As an example of the wealth of information in this mind-map, here’s a snippet from the section on broken user authentication:
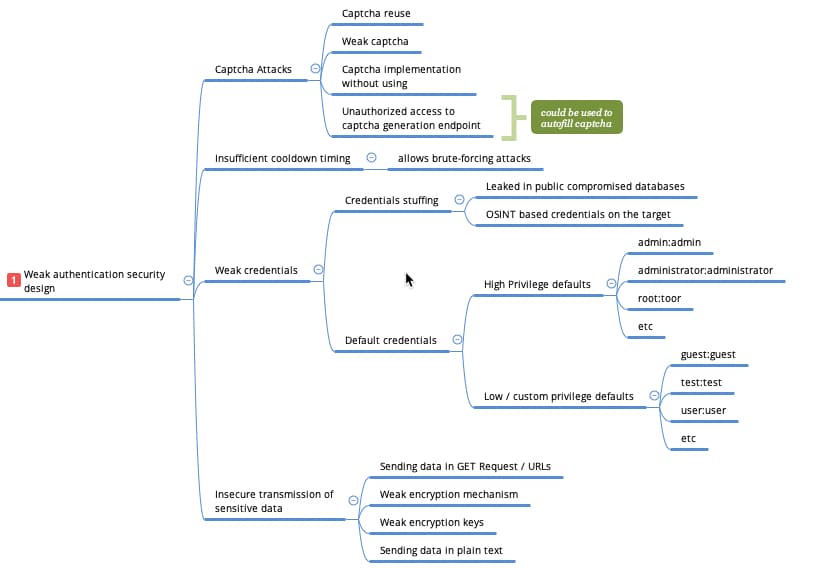
Another great resource for API testers.
Article: Tackling API security with CVSS
Changing topics entirely, next up is a post from the Cisco research team on how to use the Common Vulnerability Scoring System (CVSS) to score API vulnerabilities based on their likelihood of impact. CVSS is popular in the IT security industry as it claims to offer a standard, well-understood scoring system for vulnerabilities to allow organizations to prioritize remediation efforts.
A CVSS is calculated using three elements:
- Baseline, which comprises of the attack vector, attack complexity, required privileges, user interaction, scope, and the impact on confidentiality, integrity and availability (the CIA analysis).
- Temporal, which comprises of exploit code maturity, remediation level, and report confidence.
- Environment factors, specific factors which may affect the baseline scoring, such as vulnerable host platforms.
The author highlights a new Cisco platform (Panoptica) designed to identify APIs through a service mesh or Kubernetes deployments and then to add risk context to these APIs. Having a single view of APIs ranked by CVSS score allows teams to tackle the biggest issues first. Unfortunately, little detail is provided on the actual methodology used to provide this risk context.
Article: Ten years of API security vulnerabilities
Finally, this week, we have perspectives from API security veteran Ivan Novikov , covering his ten-year journey in API security vulnerabilities. The report covers over 10,000 CVEs, BugBounty reports, exploits, and data from Novikov’s personal research over this period.
The key takeaways from the article are:
- Five API exploits happen every day: Readers of this newsletter will not be surprised that’s the first on the list. Exploits have been steadily increasing over the last decade, and since 2020 they have averaged to over five per day.
- The use of non-web APIs is rising: Although REST APIs dominate API traffic, there is an increasing share from non-web APIs, such as BAPI, Android, and iOS, to name but a few.
- CVSS score is ~6.0 since 1998: Segueing nicely from the previous article on CVSS, on average API vulnerabilities score 6.0 on the CVSS scale (from 0.0 to 10.0), so classed as high risk.
Novikov makes two additional observations. Firstly, that the threat to APIs is likely higher than indicated by the CVSS score alone — measuring by exploitability alone, the CVSS score is likely nearer to 9, meaning super high risk. Secondly, the findings indicate that nearly half of organizations are using legacy API protocols — using more modern and inherently more secure protocols can reduce your API risk.
Webinar: Review of API Breaches in H1 2022: Episode two — Remediation and Prevention
Last month, I presented a webinar on a dozen API breaches covered in this newsletter so far this year, and in August, I’ll be hosting the second part of this popular webinar.
In this webinar, I’ll be getting into practical guidance on how to prevent and remediate some of these types of breaches. In particular, we’ll focus on the following topics:
- Applying defensive coding practices to secure APIs.
- Practical demonstration of how 42Crunch can detect and protect APIs from such vulnerabilities.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy
