This week, we ponder when is an API vulnerability a vulnerability, and check out Gartner’s new report and OWASP’s new API security project.
Vulnerability: Cisco Webex and Zoom
Definitions of API vulnerabilities can vary: what someone considers a vulnerability may be design to someone else. This is exactly the case with this week’s vulnerability.
Cequence researchers think that the APIs of Cisco Webex and Zoom are vulnerable. Attackers can enumerate the alphanumeric meeting IDs through API calls. If the host has not set a password, the attackers can access the meeting simply with a valid ID and snoop on the meetings.
The vendors claim this is by design to improve the user experience and optional, and thus not a real vulnerability. However, the meeting passwords are now on by default with both vendors, so at least users have to opt in on this one.
It is not clear from the article whether the vendors are using other techniques to prevent the attack. Obvious low hanging fruits would be:
- Low rate limits on the API calls to join meetings. There is no reason why someone would need to try more than one meeting ID in a second and more than a few per minute / hour / day.
- Automated client lockouts when enumeration is detected.
- Hard to guess and enumerate meeting IDs: longer and randomly generated.
Analysts: Gartner
Gartner has released their latest report on API security: “API Security: What You Need to Do to Protect Your APIs” by Dionisio Zumerle, Jeremy D’Hoinne, and Mark O’Neill.
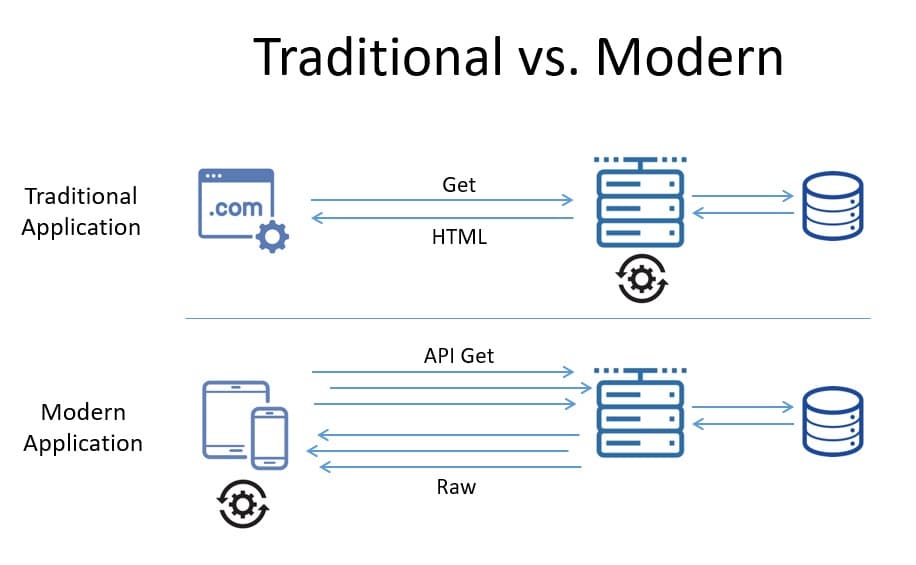
API breaches are continuing to occur frequently. With API proliferation and each API being an additional and potentially unique attack vector, traditional application security solutions alone are not sufficient to offer effective protection.
Microservices, mobile clients, and hybrid deployments also make single-point “gateway”-style protection rarely effective.
The report talks about:
- Approaches and technology to discover APIs and the vulnerabilities in them before attackers do
- DevSecOps approach to API security
- Distributed enforcement model.
A must read for anyone in API security.
Why OWASP API Security Top 10
OWASP Top 10 was first published in 2003 and has become a popular resource for web application security.
Later this year, OWASP is releasing its first ever OWASP Top 10 list for API Security.
In his article “Why You Need to Think About API Security”, one of the project leaders, Erez Yalon:
- Explains why API-based apps today are fundamentally different than the traditional apps
- Lists some API-specific security risks
- Introduces the OWASP API Security Top 10 Project.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy