This week, we check out the API vulnerabilities in the Mercedes-Benz connected cars and the Russian inter-bank money transfer system. We also have the upcoming ASC 2020 conference next week, as well as a recording of IIoT Cybersecurity panel discussion from the recent IIoT World event.
Vulnerability: Mercedes-Benz car control
The conference Black Hat USA has posted the slides and the full research paper from the session “Security Research on Mercedes-Benz: From Hardware to Car Control” by Minrui Yan, Jiahao Li, and Guy Harpak. Too bad there’s no video recording.
Researchers got access to the backend intranet through the eSIM of a Mercedes-Benz E-Class connected car. To get connected, they had to reuse the APN settings, spoof IMEI numbers, and locate and reuse certificates. However, once they got through these hurdles and managed to established the connection, they found that the APIs themselves were not protected at all.
The researchers could issue commands to any cars of the same model in the same region (China in this case, so estimated 2 million connected cars), such as:
- Locking or unlocking doors
- Opening or closing the roof
- Switching lights on or off
- Making the car beep
- Starting or stopping the engine (limited)
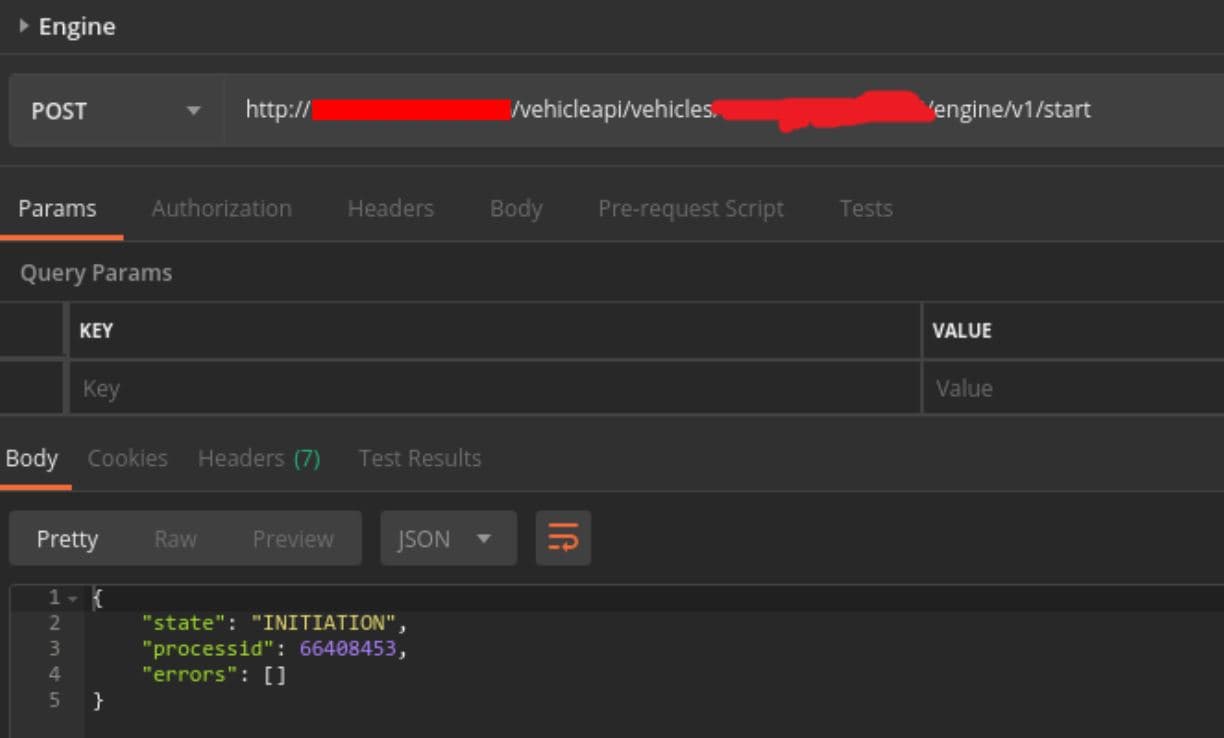
Quite a list of things, then. Lessons learned here:
- Never trust the API client: no matter how protected your client and network are, there is a chance that someone breaks through.
- Always implement both authentication (to prevent unauthorized access once attackers found your API) and authorization (to prevent IDOR/BOLA style scope expansion like in this case).
Vulnerability: Russian inter-bank transfer system
The Russian inter-bank money transfer system got hacked through the mobile app of one of the member banks.
Attackers located the vulnerable API by proxying the calls. They found that they could simply replace the source account ID parameter in money transfer calls and the backend would transfer the money, without checking whether the source account belonged to the person invoking the API.
So, how did the attackers get valid account IDs in the first place, then? To make things worse, there was another API endpoint that allowed attackers to enumerate accounts in the bank, creating a list of possible victims.
Unfortunately, the attack was identified only after the vulnerability had already been exploited, and Russian Central Bank had to send banks a warning about the attack. The story (unfortunately in Russian, so you might need Google Translate) does not contain the details on how many accounts got compromised or the total volume of funds stolen.
Storyline from a heist movie, this one. Lessons learned:
- API1:2019 — Broken object level authorization remains one of the most frequent and the most dangerous vulnerability. Implement resource-level authentication in your APIs, and prevent enumerations!
Conference: API Specification Conference
Next week, September 9—10, is API Specification Conference (ASC) 2020, the annual event by the OpenAPI Initiative (OAI). This year, it is all online, very reasonably priced (just $39, of which $10 goes to charity), and has lots of great content.
The conference is all about API standards: the OpenAPI Specification (OAS), RAML, Blueprint, gRPC, OData, JSON Schema, GraphQL, AsyncAPI, OAuth – and a great opportunity to meet the geniuses behind them.
This year, I found at least two security sessions on the agenda:
- “Did You Know You Could Use OpenAPI for Security?” by Isabelle Mauny, 42Crunch
- “Not your Uncle’s Auth: OAuth2.1 and Other Updates in Securing Your API” by Vittorio Bertocci, Auth0
Video: IIoT Cybersecurity Challenges
Industrial Internet of Things (IIoT) is a big driver of what is now called Industry 4.0. IIoT takes automation to the next level and allows industry to become agile and scalable at unprecedented levels.
The conference IIoT World has published the recording of the IIoT cybersecurity panel discussion recorded at the event this summer. Here’s the quick abstract:
The Industry 4.0 revolution brings with it a new operational risk for connected, smart manufacturers and digital supply networks: cyber. Industrial Cybersecurity should be an integral part of the strategy, design, and operations from the beginning of any new connected, Industry 4.0–driven initiative.
In light of Industry 4.0, our expert line up of panelists will examine visibility, control, and situational awareness in relation to your cyber security strategy – and their impact on the future of digital manufacturing.
This panel, originally presented at IIoT World Days on July 1, 2020, discusses:
- Top trends impacting today’s manufacturers security strategy
- What are the cyber security-specific technical issues associated with Industry4.0?
- What are the cyber security-specific training and education issues associated with Industry4.0?
The member of the panel were:
- Joe Weiss (Moderator), PE, CISM, CRISC, ISA Fellow, IEEE Senior Member, Managing Director ISA99; Applied Control Solutions, LLC
- Pamela Gupta, President, OutSecure, Inc.
- Dmitry Sotnikov, Chief Product Officer, 42Crunch
- Chuck Brooks, President, Brooks Consulting International
- Bryan Skene, CTO and VP of Product Development, Tempered
I loved participating in the panel discussion and would recommend it to anyone interested in the cyber security aspects of IoT.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy
