This week, we take a look at how thousands of Android apps inadvertently exposed Google Firebase APIs, and how Arkansas Pandemic Unemployment Assistance (PUA) portal was leaking sensitive personal data. We also have a new pentesting tool for identifying data transformations used in APIs and apps, and a case study of four recent high-profile API breaches.
Vulnerability: Google Firebase
Google Firebase is a development platform for mobile apps. It claims to be used in over 1.5 million mobile apps to provide standard platform functions like authentication, cloud storage, messaging, and analytics.
Security researchers from Comparitech found unsecured API access to the Firebase cloud storage used by estimated 24,000 Android apps. The vulnerability is not really a vulnerability in Firebase itself, but how a lot of Android developers set up and use Firebase. It is also good to note that because Firebase is a cross-platform tool, the impact might not be limited to just Android.
Because the platform is cloud-based, there unfortunately is room for dire consequences if its security is configured poorly. The leaky deployments exposed REST APIs that allowed attackers to download end user data through GET requests, and even make changes to the data with PUT requests.
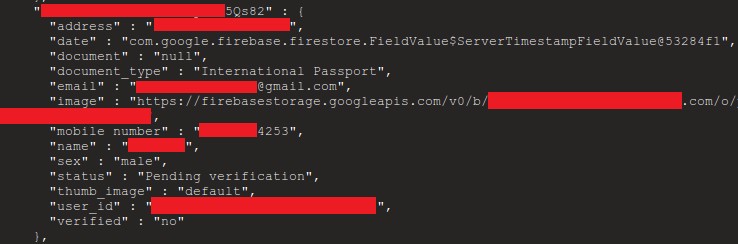
For app developers, the important lesson learned here is that whenever your app uses a cloud service, you as the developer are responsible for configuring the security for the access to that cloud service, in the most secure manner!
On the other had, service providers need to strive to make their systems secure by default and make insecure configurations impossible. At the very least, if there is a legitimate use case for such a configuration, the service providers should highlight the risks to users and deter their customers from such scenarios.
Vulnerability: Arkansas PUA portal
An unemployed computer programmer found an API vulnerability in the Arkansas PUA website when applying for assistance.
The portal had an unprotected API connecting to the backend. This exposed highly confidential personal information — including social security numbers and bank account numbers — of about 30,000 applicants who had used the portal. Definitely something you could do without when you are already in a tight spot.
What aggravates the case even further is the reaction from the state authorities. When notified about the issue, they took the site offline to fix it (great!), but also announced that they had asked FBI to go after the researcher who alerted them!
Tool: Transformations
Quite often, APIs and applications use encoding rather than encryption when storing and transmitting data. This approach is more security by obscurity, and attackers can get hold of the content as long as they know which algorithms were used in encoding. To catch this, penetration testers need to be able to fish out whether the system they test is indeed merely encoding values and how.
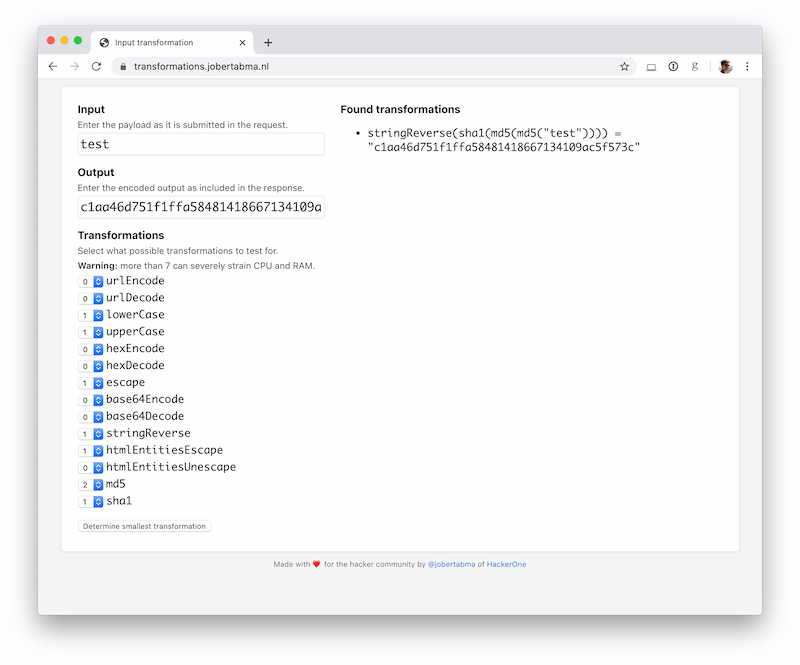
Jobert Abma has published a new open source tool, Transformations, for just that. You feed a known input-output pair into the tool and it tries various combinations of known encoding algorithms on the pair to see if it can find a match.
For example, when given the combination of the input test and the output c1aa46d751f1ffa58481418667134109ac5f573c, the tool reports it was produced with the combination stringReverse(sha1(md5(md5("test")))). Pretty neat!
Video: The Anatomy of Four API Breaches
Learning from someone else’s mistakes is the best way to learn. To this effect, 42Crunch has published a recording of a recent talk by their Field CTO, Isabelle Mauny. In it, she goes into the details of four recent high-profile API breaches: how they happened, what were the root causes, and what could have been done to prevent them.
Webinar: Top API Security Issues Found During POCs
And for those who want to learn more of Isabelle’s findings – she is giving another webinar next Tuesday, May 26. This time it will be based on the Security Audit results she has been doing at some of the largest enterprise customers.
Here’s the abstract:
Over the past 6 months, we have discovered many similarities across APIs from companies from very different industries. “This is an eye opener” is the most recurring comment from our prospects. We thought it would be worth sharing our findings in this webinar.
Through a mix of slides and demos, we will describe the top 5 issues our security audit reports, what they are and why they matter, including:
-
Potentials attacks linked to each issue
-
How they can be remediated
-
Example request/response and reports
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy