This week, we have news of multiple API flaws and vulnerabilities: the parcel tracking portal at DPD that may have exposed customer data; an API vulnerability in the Apache Pulsar that allowed access data in different tenants; and an SQL injection vulnerability in Casdoor API. On the more positive side, we take a look at the emerging trends in the API industry.
Vulnerability: DPD parcel tracking flaw may have exposed customer data
The big news this week was the disclosure of a vulnerability in the parcel tracking portal of DPG Group, which may have exposed customer data.
The vulnerability was discovered by Pen Test Partners in September 2021, and they co-operated with DPD Group to assess and triage the vulnerability. DPD Group resolved the vulnerability in October 2021 and had requested that the details only be published in the new year to have time to conduct a full review.
The package tracking provides an API call that accepts a UK postcode together with a parcel tracking code to return a PNG image of the recipient’s address through an OpenStreetMap. The first stage of the exploit was that attackers could post a random parcel code to retrieve an image like the following:
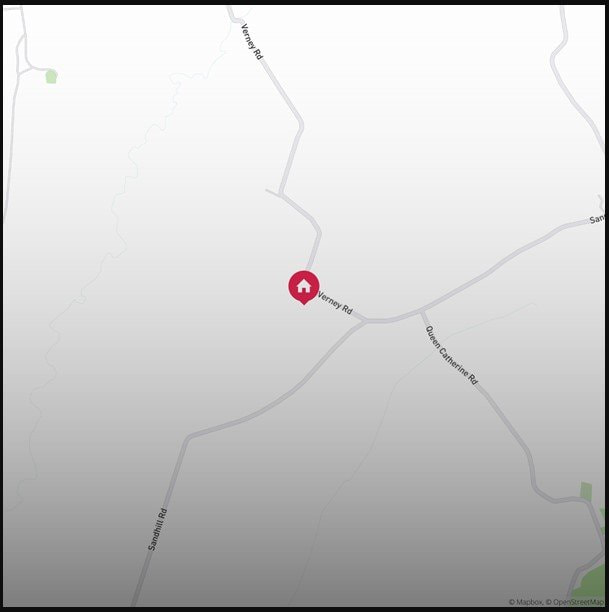
Using elementary analysis of the received map image, the researchers determined the exact postcode of the recipient. This postcode could then be supplied together with the parcel code to retrieve detailed delivery information, including PII information.
A successful attack would have been reliant on guessing an active, valid parcel code and would also have required manual steps to extrapolate the exact postcode and defeat the Captcha. However, given the valuable PII disclosed, DPD Group considered this attack to be serious, and they responded quickly to remediate it.
Lessons learned here include:
- Be wary of API3:2019 — Excessive data disclosure — for tracking purposes, there was no need to return the full PII record of the customer.
- A lack of rate limiting (API 4:2019 — Lack of resources and rate limiting) allowed automated attacks with random parcel numbers. Make sure to include protection against bot or scripted attacks.
Vulnerability: Apache Pulsar admin API vulnerability
The second vulnerability covered in this week’s edition comes courtesy of a flaw in the admin API of the popular Apache Pulsar platform.
The admin API required a client to submit a topic and a ledger ID associated with the provided topic. The API implementation did check the client authorization, but unfortunately it did not check the authorization for the ledger ID. This could have allowed an attacker to provide a ledger ID for data on other tenants, for which they were not authorized.
This issue affects Apache Pulsar version 2.8.0 and prior versions. If you are using an affected version, do upgrade to a version with the fix as soon as possible
This vulnerability is an example of API1:2019 — Broken object level authorization, perhaps also API5:2019 — Broken function level authorization.
Vulnerability: SQL injection vulnerability in Casdoor API
The third vulnerability this week is the vulnerability in the Casdoor single-sign-on platform. The vulnerability, tracked as CVE-2022-24124, was discovered by the security researcher @wuhan005, and it is detailed in a GitHub issue on the associated GitHub repository.
The researcher discovered that the endpoint /api/get-organizations was vulnerable to SQL injection by examining the underlying code:
session = session.And(fmt.Sprintf("%s like ?", util.SnakeString(field)), fmt.Sprintf("%%%s%%", value))
This is an example of an API8:2019 — Injection vulnerability — in this case, an SQL injection attack that celebrates its 20th anniversary this year!
Opinion: Emerging trends in the API industry
Finally this week, we have an excellent discussion between Bill Doerrfeld and Steve Rodda, CEO at Stoplight. Although they do cover a wide range of API topics, they emphasize the need for robust API security.
Doerrfeld and Rodda identify common security issues — familiar to readers of this newsletter — including:
- Failures relating to authorization
- Excessive data exposure
- Exposure of endpoints intended to be for private or internal use only
- Security misconfiguration
Rodda recommends: “good documentation, good design guides and good discipline around building something with a cross-functional nature will increase security and scalability”.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy