This week, we have a long-standing vulnerability on a public-facing internal API on Uber, which allowed attackers to spoof emails. In addition, there’s an article by NordicAPIs on the RapidAPI report into the rise on partner-facing APIs, IBM’s views on the API security risk posed by the growth in omnichannel APIs, and finally (another) awesome API security mega guide.
Vulnerability: Uber bug allows attackers to spoof emails
This week, ThreatPost featured details of a vulnerability on a public-facing internal API on Uber allowing attackers to spoof emails so that they would appear to be from Uber.
Details of the vulnerability were disclosed by a Seekurity security researcher and bug-hunter Seif Elsallamy, who made efforts to disclose details to Uber both directly and by submitting it to HackerOne. However, Uber rejected Elsallamy’s submission out of scope, only it to be later discovered that the issue has previously been reported to Uber as far back as 2015! Elsallamy has since reported that the issue appears to have been finally fixed.
The vulnerability enabled attackers to use a public-facing internal API on Uber to do HTML injection and send emails on behalf of Uber. Users could be tricked into believing that the emails were genuine and potentially perform unsafe actions, such as disclosing financial details or sensitive personal information. Elsallamy showed an example of a proof-of-concept spoof email below:
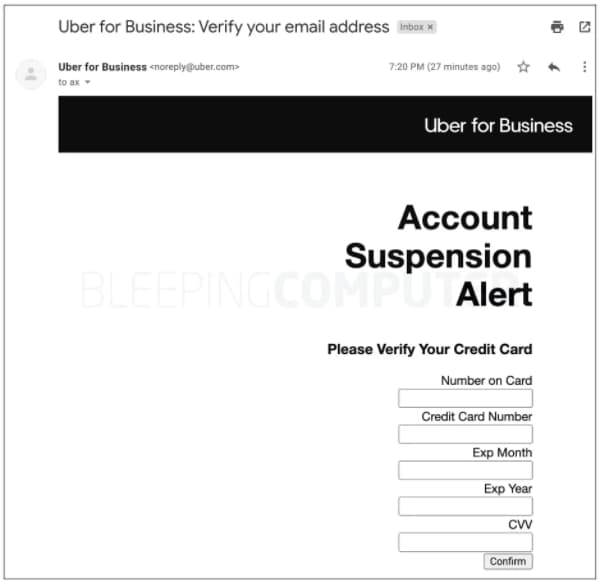
Uber has previously featured in this newsletter and suffered a large breach in 2016 that lead to the disclosure of 57 million user account details.
The key takeaways here are:
- Be aware that APIs intended for internal use only may be easily discovered (and exploited) if they are connected to a public-facing network.
- APIs can inadvertently expose previously latent vulnerabilities in downstream systems — in this case, a backend system was vulnerable to HTML injection.
- Security-savvy organizations should have a proactive (or at least responsive) manner for dealing with bug and vulnerability reports — here, the same issue had been reported already several time previously but had not been acted upon.
Article: Partner-facing APIs on the rise
NordicAPIs has featured an article on the rise of partner-facing APIs on the back of the recently released “State of APIs Developer Survey 2021 Report” from RapidAPI.
The report surveyed 2,200 developers and sampled their views on their experience with APIs, both from the perspective of internal tools to an increasing number of partner-facing APIs. The growth of such partner-facing APIs presents challenges to organizations: as the number of APIs grows, they become increasingly difficult to maintain, not to mention challenges relating to data privacy and security issues.
From a security perspective, two distinct challenges are highlighted:
- The primary API testing is focused on acceptance testing, functional testing, and integration testing, but no mention of security testing is made in the survey.
- The skills shortage in the software has been exacerbated by the Covid-19 pandemic, and nowhere is this more profound than in software security.
Many organizations are being driven towards enabling partner-facing public APIs whilst being aware that these APIs are not adequately tested from a security perspective, nor do their developers have the requisite experience to fully secure these APIs.
Article: Omnichannel API growth increases API risk
IBM SecurityIntelligence has featured an article on the rise of so-called omnichannel APIs and how these are exposing organizations to increased API risk. The well-documented growth of APIs is being driven by three main factors:
- Multi-device use: Users have multiple devices and APIs are required to provide features and functions on all of them.
- Microservices: The breakdown of the monolith architecture has led to distributed microservices, with APIs connecting them all.
- Move to the cloud: Ease of cloud deployment has also increased the rate of software deployment, including APIs.
The report highlights how an omnichannel business strategy is adding further fuel to the fire of API growth. An omnichannel customer experience attempts to ensure that the customer experience remains the same regardless of the medium used, be it a web portal, a desktop app, or a variety of mobile devices. To make this experience seamless, each platform must present a consistent view to the user — and APIs are the connecting fabric that enables this experience.
The article concludes with recommendations how to improve API security, many of which will come as no surprise to readers of this newsletter:
- Keep an API inventory: It’s impossible to secure what you can’t see.
- Practice secure coding: All software vulnerabilities have their origin in vulnerabilities in coding.
- Implement OAuth: Avoid issues with token secrecy and leaks by using a robust authorization protocol.
- Implement rate limiting and throttling: Prevent abuse of APIs by limiting the rate of attack.
- Use an API gateway: Use a gateway as a central point to enforce security policies.
- Use a service mesh: Leverage the mesh to enforce authentication, access control, and other security measures throughout your services.
- Adopt Zero Trust: Do not rely on traditional perimeters or trust boundaries.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy