The Open Web Application Security Project (OWASP) is a non-profit, collaborative online community behind the OWASP Top 10. They produce articles, methodologies, documentation, tools, and technologies to improve application security.
Since 2003, OWASP Top 10 project has been the authoritative list of information prevalent to web application vulnerabilities and the ways to mitigate them. However, the rise of the APIs has — and is — changing security landscape so fundamentally that a new approach is needed. As a result, in 2019, OWASP started an effort to create a version of their Top 10 dedicated specifically to API security. The first OWASP API Security Top 10 list was released on 31 December 2019 and the second was released in June 2023.
Web application security vs API security
While REST APIs have many similarities with web applications there are also fundamental differences.
In traditional web applications, data processing is done on the server side, and the resulting web page is then sent to client browsers simply to be rendered. Because of this, the entry points to the network architecture of the business were relatively few and straightforward to protect by setting up a web-application firewall (WAF) in front of the application server.
Modern API-based applications are very different. More and more, the UI uses APIs to send and receive the data from the backend servers to provide the functions of the application. It is now the clients that do the rendering and maintain the state.
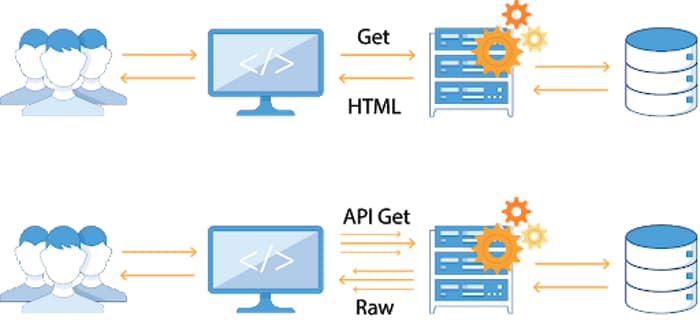
Add to that the microservices architectures with individual application components becoming APIs, and you get a much different world with significantly expanded attack surface. Now, the entry point to the network architecture is the plethora of APIs that call to the backend or in east-west direction in the network.
With so many entry points often widespread in the network architecture, putting a firewall in front of a server is no longer enough to ensure all entry points are protected. In addition, a traditional WAF-based solution has no means to distinguish hacking API calls from legitimate API traffic.
By nature, APIs expose application logic and sensitive data such as Personally Identifiable Information (PII) and because of this have increasingly become a target for attackers. APIs provide a contract, but they do not themselves contain adequate measures to ensure that the contract is upheld, posing a serious security risk to the backend services the APIs connect to.
All this means that API security needs its own brand of security that focuses on strategies and solutions to understand and mitigate the unique vulnerabilities and security risks of APIs.
OWASP API Top 10 project
The changes in the industry mentioned above have resulted in OWASP launching a separate project dedicated purely on API security. Now, the OWASP API Security Top 10 project focuses specifically on the top ten vulnerabilities in API security.
The new project recognizes two things:
- The crucial role that APIs play in application architecture today and therefore also in application security
- The emergence of API-specific issues that need to be on the security radar.
OWASP API security resources
Here are some additional resources and information on the OWASP API Security Top 10:
- If you need a quick and easy checklist to print out and hang on the wall, look no further than our OWASP API Security Top 10 cheat sheet
- Recordings of our webinars on OWASP API Security Top 10 are available on our YouTube channel
- To download the full PDF version of the OWASP API Security Top 10 and learn more about the project, check the project homepage
- If you want to participate in the project, you can contribute your changes to the GitHub repository of the project.
OWASP API Security Top 10 Vulnerabilities Listings