This week, we check out the recent API vulnerabilities at F5 and Facebook, there’s a new tool to locate regular expressions vulnerable to Denial-of-Service (DoS) attacks, and we have the recording of Ford’s recent talk on their API security policies and lessons learned.
Vulnerability: F5 iControl REST API
This one appears to be the most significant enterprise API-based attack in 2021 so far.
F5 BIG-IP and BIG-IQ systems are popular with enterprises. They expose iControl REST endpoints for remote administration. The API is extremely powerful, for example, it allows to run arbitrary bash commands and install additional components.
F5 found that the APIs were vulnerable and has released their fixes, but it takes time for the companies using the products to update their deployments. Unfortunately, it doesn’t take much time for the bad guys to reverse-engineer the patches and launch their attacks.
Initially, it was believed that attackers still need to find a way to get a user authentication cookie, but lately it has turned out that authentication can be bypassed entirely. You can see the timeline, details, links to proofs-of-concept scripts, screenshots, and so on in this NCC Group post.
Lessons learned:
- Having an API that runs arbitrary commands under the
rootaccount is extremely dangerous. API scope and privileges must be strictly defined and limited to the bare minimum as much as possible.
Vulnerability: Facebook GraphQL API
Moving on to something less critical: Baibhav Anand found a vulnerability in Facebook’s GraphQL API that allowed a non-member to find out if someone was a member in a private Facebook group or not.
Quoting from Anand:
“A Non-member can determine if someone is the member of a private group or not via CometHovercardQueryRendererQuery graphQL mutation. Doc_ID: 4997502340291357. By changing the actorID with the victim’s actorID and groupID with the group we want to test and in the response if it shows “WeakEntityReference” than he/she is not the member of the group. However, if it shows “StrongEntityReference” than he/she is the member of the group.”
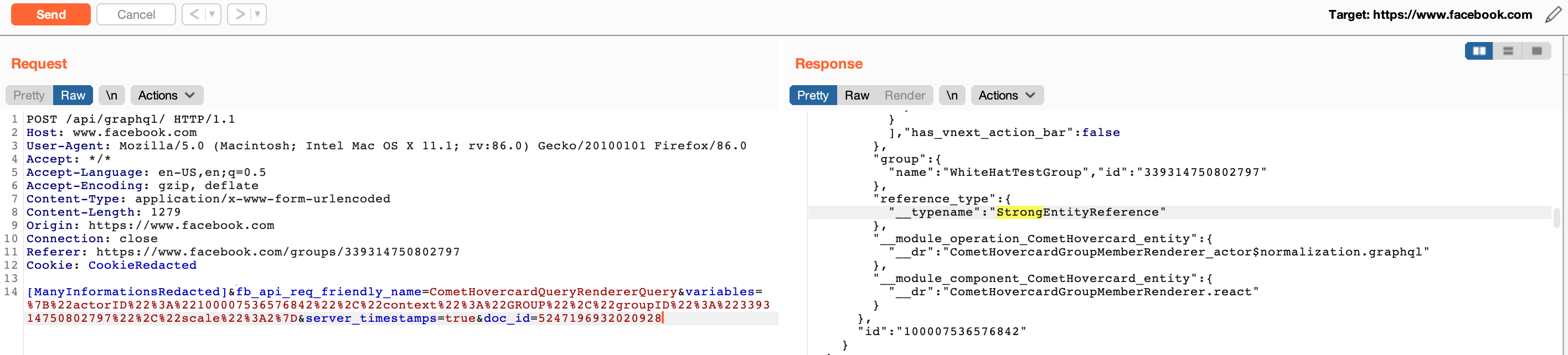
Facebook quickly fixed the vulnerability after it was reported. Lessons learned here:
- Authorization is important. Don’t trust parameters in API calls, always verify that the caller has the rights to perform the operation on the objects.
- Make sure that your responses do not leak information about the existence or state of objects if these are confidential.
We have previously covered vulnerabilities in Facebook’s GraphQL API, for example, in our issue 102.
Tools: Regexploit
Regular expressions (regex) are a great way to define expected formats of string parameters and payloads. In fact, this is the route that JSON schema and the OpenAPI Specification (OAS) expect you to take.
However, not all regular expressions are created equal. It is quite easy to create a potentially resource-hungry regex that can be exploited for a DoS attack. The attacker sends a string that requires so much resources to verify against the regex that the system can become unresponsive.
Doyensec has released an open-source tool called Regexploit that can locate and report such vulnerable regexes. In fact, they successfully used the tool to locate and report the vulnerability in many open-source projects. They list more than a dozen of such reports.
For more details, check the GitHub repository of the project.
Video: Ford Motor Company API security story
Rolling out API security across a large enterprise is not easy.
Darren Shelcusky, Manager of Vehicle & Connectivity Cybersecurity at Ford Motor Company, recently gave a webinar talking about their experience. Needless to say that Ford is a global enterprise, with thousands of APIs and engineers working on them, and that in the world of connected cars API security is critical.
Check out the recording of the webinar below to learn how Ford is tackling the problem and scaling their approach, what worked, and what did not.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy