This week, we have a report from Imperva indicating that vulnerable APIs may be costing as much as $75 billion annually with the largest organizations being at the highest risk. We also have coverage of the new API security platform from Google, views from Curity on API-driven backends for frontends for increased API security, and finally a comprehensive beginners guide to the OWASP API security Top 10 from Tyk.
Report: Vulnerable APIs costing $75 billion
Last week we featured coverage of the recent from Imperva in partnership with the Marsh McLennan Global Cyber Risk Analytics Center which indicated that one in thirteen incidents originated with insecure APIs. This week we look at the financial impact of vulnerable APIs courtesy of VentureBeat. The headline figures estimate the range of possible financial impact as follows:
- Average annual API-related U.S. cyber loss — USD 12-23 billion
- Average annual API-related total global cyber loss — USD 41-75 billion
- Average annual API-related global insured cyber loss — USD 205-376 million
Although any research estimating the hypothetical cost of breaches has a large margin of error, these figures are quite sobering. For me, the most important takeaway is that such losses are entirely avoidable by investing adequately in API security solutions and protection. As the authors conclude: API-related losses could decrease significantly even as their API adoption continues to increase.
Lebin Cheng, vice president of API Security, Imperva provided further comment on the reasons why companies are failing to protect their APIs: Many organizations are failing to protect their APIs because it requires equal participation from the security and development teams. A successful API security initiative requires a balanced approach focused on people, processes, and technology. Of these, it is the people aspect that is hardest to get right — on the one hand, security needs to avoid negatively impacting developer productivity, whilst developers need to take responsibility for the security of their code.
The full report is available from the Imperva website.
Article: Google launches new API security platform
On the topic of API security tooling and solutions comes the news that Google has announced a new product called Advanced API Security which is currently in preview mode. The product is built on top of their popular Apigee API gateway and focuses on two key API security areas: identifying API proxy misconfiguration and protecting against bot-based attacks. The new product is aimed specifically at Google’s financial services customers — currently, four out of five US banks use Apigee.
In this newsletter, we frequently cover the rising instances of bot attacks against APIs and it comes as no surprise that bot protection is to be incorporated into Apigee. Although not much technical detail is provided on the underlying technology the bot protection will assess unusual traffic patterns from a single IP address to identify possible attacks, and in particular to focus on HTTP 200 OK responses since these indicate a successful bot transaction.
Of all the OWASP API Security Top 10 vulnerabilities API7:2019 — Security misconfiguration is possibly one of the easiest to prevent using automated inspection of API servers and gateways to identify common security misconfigurations. This is the other focus area for the Advanced API Security product and although details are scant at this stage it appears the product will scan APIs and traffic to identify information disclosure or leakage, typically PII or healthcare data.
As per the first article, many API-based attacks are preventable using appropriate security tooling — this offering from Google undoubtedly improves the API security posture for their users.
Article: API-driven backends for frontends for increased API security
Next, we have an excellent technical article from Gary Archer at Curity on the topic of API-driven backends for frontends for increased API security. The article gives an excellent discussion on how to secure modern web applications based on the single-page application (SPA) model. Typically these comprise two backends — the first is a content-delivery-network (CDN) delivering static or server-rendered content, and the second is an API backend responsible for providing dynamic page content based on user operations.
The article describes robust and scalable approaches to provide API security based on OAuth2 and OpenID patterns. In the first diagram below the API backend is split into two components — the so-called backend-for-frontend is responsible for handling the initial authentication and returning an opaque token that can be embedded in a standard web cookie. The SPA can then make subsequent requests to the APIs by presenting the web cookie which is exchanged for a JWT to be validated by the API backend.
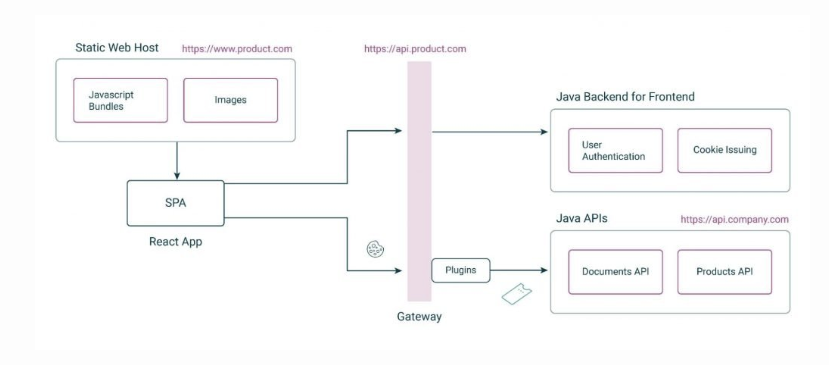
Curity describes their API-driven Backend for Frontend pattern to facilitate a scalable and compact solution based on standard components. As shown below an OAuth agent handles the initial authentication, and in subsequent requests, an OAuth proxy is responsible for exchanging the web cookies into JWTs that are presented to the API backend.
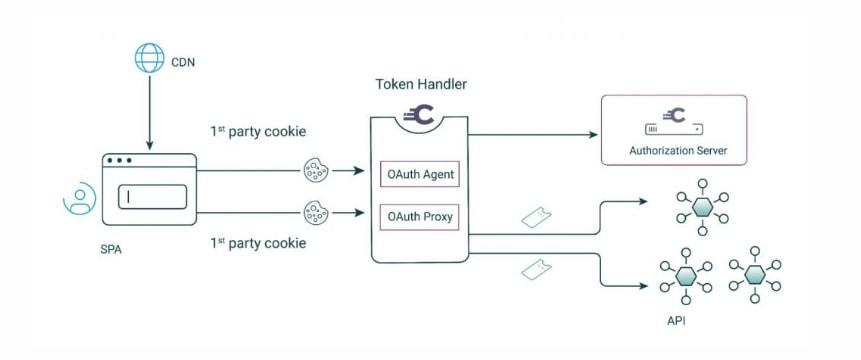
Once again a great read from Curity — use the API-driven Backend for Frontend to manage the issue of secure cookies and helps to separate web and API concerns.
Article: Introduction to OWASP API security Top 10
Finally this week we have another contribution to the body of knowledge on the OWASP API Security Top 10, this time from the team at Tyk.
Tyk provides an unusual take on the Top 10, focusing on the OWASP Risk Rating Methodology to rate and rank the Top 10 vulnerabilities. This methodology evaluates risks against different criteria; threat agent, exploitability, weakness prevalence, weakness detectability, technical impact, and business impact. This interesting approach gives security teams a sense of the relative priority of vulnerabilities to allow focused remediation.
The article provides a really great deep dive into each of the Top 10, including the attack vector, the impact, and common defense approaches. Tyk also describes how API management solutions can address the vulnerabiltiy.
Webinar: Review of API Breaches in H1 2022: Episode two – Remediation and Prevention
Last month I presented a webinar on a dozen of the API breaches in this newsletter, and on the 21st July, I’ll be hosting the second part of this popular webinar.
In this webinar, I’ll be getting into practical guidance on preventing and remediating some of these breach types. In particular, we’ll focus on the following topics:
- Apply defensive coding practices to secure APIs from such vulnerabilities.
Practical demonstration of how 42Crunch can detect and protect from such vulnerabilities.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy
