This week, we have three API vulnerabilities: in Echelon sports equipment, Instagram, and Facebook Workspace, as well as an interview with Forrester’s key API security expert, Sandy Carielli.
Vulnerability: Echelon
In our previous newsletter, we discussed API vulnerabilities at Peloton. This week, the same researcher, Jan Masters from Pen Test Partners, has published his research on Peloton’s main competitor, Echelon. Turns out that Echelon’s APIs were much worse, leaking a lot of very sensitive personal information of their users.
Their GET /v1/user/user_id endpoint required authentication but had no authorization checks — a classical Broken Object-Level Authorization (BOLA/IDOR) vulnerability. As long as you had any account in the system, you could get the full details on any other user, such as their name, billing address, email, phone, age, gender, weight, birthday, equipment serial numbers, where they bought the equipment, subscription dates, workout stats and history… the list goes on.
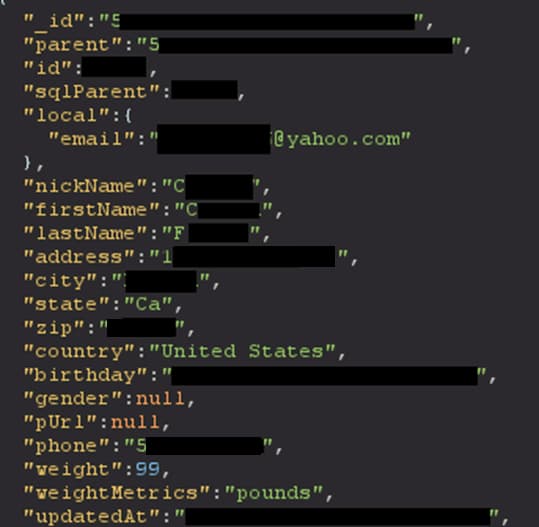
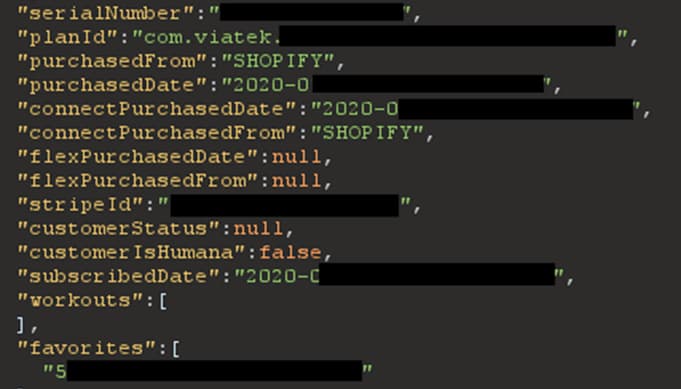
Other vulnerabilities included:
- Unprotected API endpoint
/leaderboardthat exposed information on users participating in a particular exercise class, with no authentication required - Users searchable by their email address — dangerous because attackers could find a user by email and then extract the details using the already-mentioned BOLA issue
- Metadata, such as the GPS coordinates, present in pictures uploaded by users
Although the issues eventually got fixed, these are huge exposures. APIs must be designed with security in mind:
- Does your system really need to collect and exchange so much personal data?
- Are all API endpoints protected with authentication?
- Do all record access calls check whether the caller is authorized to access the record?
Vulnerability: Instagram
Youssef Sammouda found an interesting Broken Functional-Level Authorization (BFLA) vulnerability in Instagram:
- Attackers create an application as the attack vector.
- The vector application prompts the victim user to grant it the Instagram Basic Display API level of access.
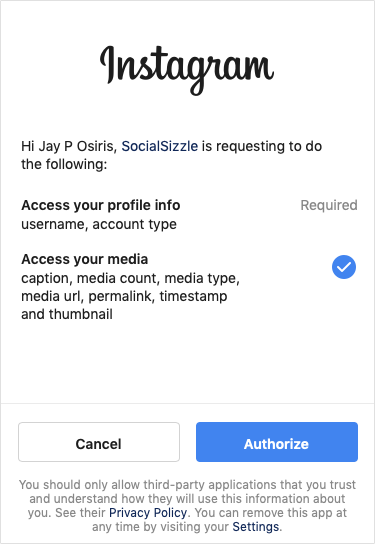
- The victim is likely to accept the request, because the only mandatory access is to username and account type, so the request looks innocuous enough.
- Instagram returns an access token to the vector application and thus to the attackers.
- In reality, the returned token grants access also to the powerful GraphQL endpoint
graph[.]instagram[.]com/graphql, which could, for example, allow attackers to take over the whole user account.
Instagram has since fixed this vulnerability. Lessons learned here: ensure security scope enforcement across all your APIs!
Vulnerability: Facebook Workspace
Facebook Workplace is a Facebook product for enterprises, sort of internal Facebook focused on communications and collaboration between employees in the organization.
Facebook Workplace can be configured to allow employees within the approved corporate email domains to self-signup into the Workplace organization. Marcos Ferreira found that the API behind the feature was vulnerable and allowed anyone invite themselves to the organization.
Ferreira investigated the API call behind the sign-up request and found the parameters it used:
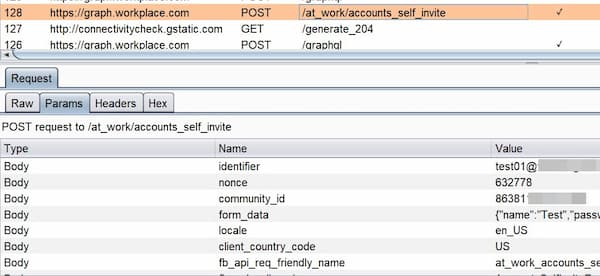
He found out that it was possible to modify the parameter community_id and to create an account to any organization that had enabled self-signup, because the email address was not properly validated. Email addresses outside the approved corporate email domains would receive a one-time passcode and could register to the organization exactly like those within the domains.
Ferreira received a hefty $27.5K reward for finding the vulnerability from Facebook, which naturally has taken the necessary steps to fix the issue.
Lessons learned in this one: APIs are your security boundary. Data validation needs to happen at the API level, not in web or mobile clients.
Video: Forrester’s Sandy Carielli on API security
Sandy Carielli is one of the leading Forrester analysts in the field of API security.
This week, at the (virtual) RSA Conference, she gave an interview to Matt Alderman, check out the recording below.
The topics of the interview ranged from the lessons learned from some of the recent API vulnerabilities and breaches, to common vulnerability patterns, and how API security spans the discovery, static, and dynamic testing of APIs, as well as their runtime protection.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy