This week, we take a look at how out-of-date library compromises login to Twitter, how simple parameter switch gave access to over 150 million JustDial user accounts, and how holes in API security can lead a business to give out uncontrolled freebies. In addition, there is an update on Google’s decision to change the access to their Nest smarthome platform and why this has happened.
Vulnerability: TwitterKit for iOS API SDK
Appicaptor has revealed that applications using the TwitterKit for iOS library to access Twitter API are vulnerable to man-in-the-middle attacks. Both Twitter access and Login with Twitter scenarios are vulnerable because the API does not properly validate the TLS certificate for api.twitter.com.
The issue stems from good intentions colliding with imperfect implementation. For added security, TwitterKit for iOS implemented public key pinning of trusted root certificate authorities. However, because of their implementation of the public key pinning method, a leaf certificate is not properly verified in certificate pinning. The SDK checks for signatures but not domain names.
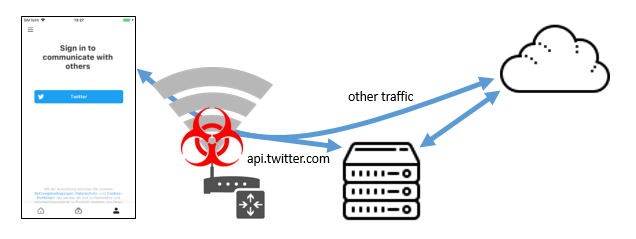
Because of the missing domain name verification, any valid certificate chain containing a certificate with a public key hash of that list is accepted by the app. An attacker with a valid certificate for his own domain, issued by one of these CAs, can use this certificate for man-in-the-middle-attacks against apps communicating via the Twitter Kit for iOS with
api.twitter.com. As the implementation does not check the position inside the chain, the matching public key could also be in the middle of the chain, such as in case of an intermediate certificate.
TwitterKit for iOS is no longer supported and thus will not be fixed, so developers should immediately switch using alternative APIs in their apps.
Certificate pinning is a great way to improve mobile application API security. However, it needs to be carefully designed. Ensure that you use standard SDKs and mobile OS libraries for certificate verification and do not re-invent the wheel.
Vulnerability: JustDial
Almost 156 million accounts were exposed because of a flawed API at JustDial, a local search service in India, a security researcher has found.
Attackers could enter the victim’s phone number in the username parameter in a call to the JustDial Register API to gain access to the user account.
The system would then return an access token, system ID (SID) and user ID (UID). Using the SID, the hacker can access the victim’s Jd pay account and other accounts, whereas the UID would allow posting on the victim’s social profile.
This seems to be an example of API1: Broken Object-Level Authorization in OWASP API Top 10.
This is the second large-scale JustDial vulnerability this year.
Vulnerability: Voi E-Scooter
A security researcher has found an API vulnerability that allowed adding $100K of free credit to a Voi e-scooter account.
Voi has several partner companies that can offer promo codes for free rides. While the Voi app UI properly verifies the information to create accounts and to add coupons, the API behind it doesn’t. By bypassing the UI and invoking the API directly, the researcher was able to create an account without having to verify email address and add payment methods, and then to add unlimited amount of promo codes to his account.
Lessons learned: do not implement security only on the UI, extend it to your APIs as well.
Governance: Google redoing Nest API access
An interesting case study of API security governance by Stacey Higginbotham.
Google had to kill their “Works with Nest” program and redefine API access to Nest devices to save themselves and users from smarthome security breaches, and to maintain control of their platform.
Initial Nest APIs allowed direct communications with any other smart devices and services. This not only kept Google from controlling the ecosystem. It also allowed rogue devices and services to gain more access than the end-user expected to grant.
Google now killed the old “Works with Nest” API access program. Instead of it, this week, they announced the more controlled way that Nest API access will be provided via “Works with Google Assistant” program for the broad consumer audience. There is also going to be Direct Access for Individuals program for enthusiasts.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy