This week, we have news of a report revealing that over 380 000 Kubernetes API servers are exposed on the internet due to possible misconfiguration, as well as details of a vulnerability allowing DOM XSS attacks in the popular Swagger-UI library. We also feature views from Google on the future of the API economy and conclude with a beginner’s guide to API keys usage and best practices.
Report: 380,000 Kubernetes API servers exposed on the internet
A report from internet security research firm ShadowServer reveals that as many as 380 000 Kubernetes API servers are exposed to the public internet. The researchers at ShadowServer scanned IP addresses by performing a GET request at the URI /version and recorded instances that returned a HTTP 200 status code. The researchers stress that whilst this response does not necessarily represent a vulnerability, such exposure to the internet is likely due to misconfiguration and is quite likely unintended.
The researchers probed over 454 000 API servers in total, the majority (84%) were found to be open. Most of these were in the United States and the location distribution is shown here:
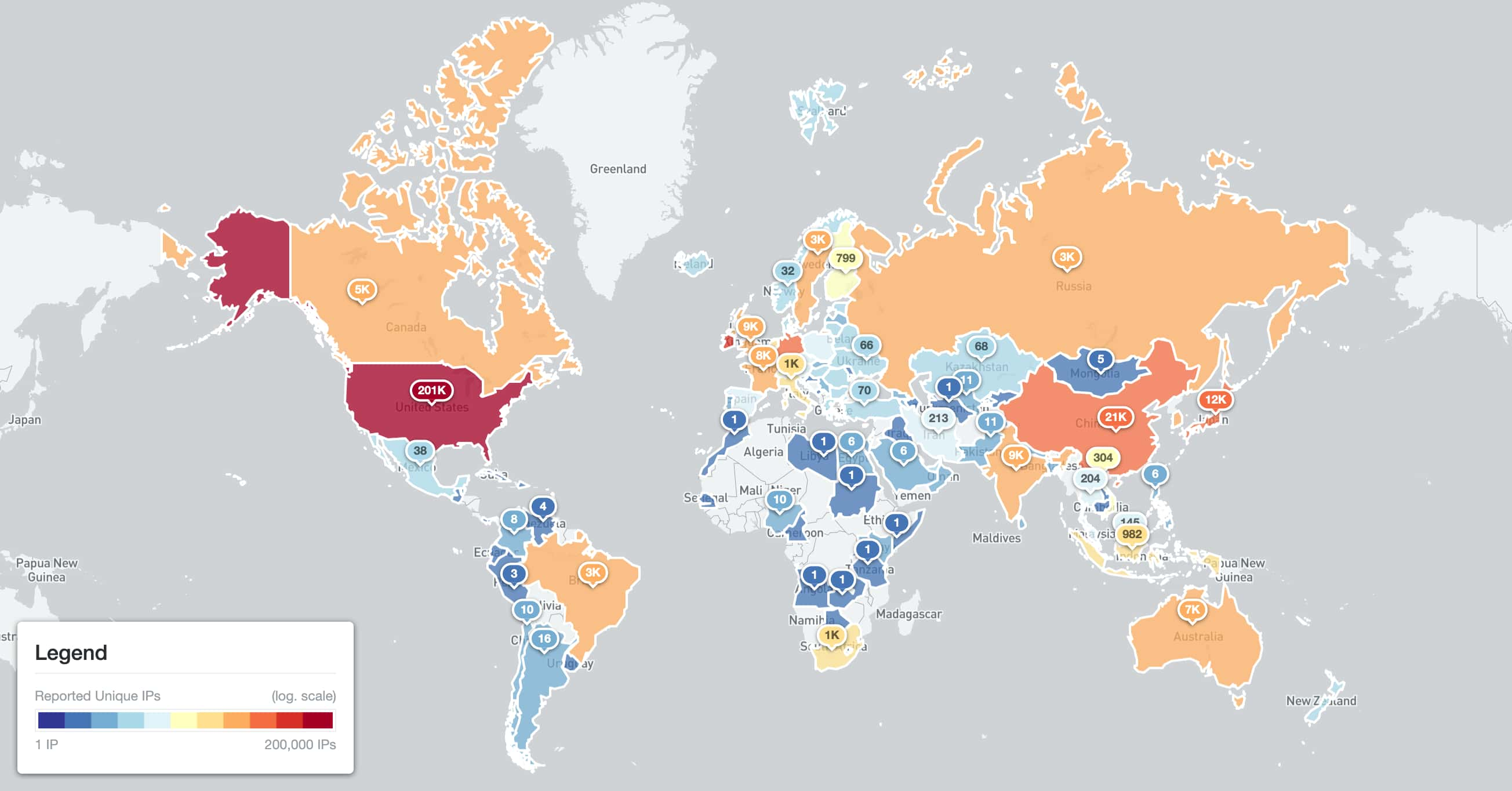
The researchers also performed an analysis of the Kubernetes API versions and OS platforms. Whilst most instances reported relatively recent (and supported) versions of Kubernetes, there were significant numbers of instances running on totally unsupported versions prior to version 1.16, going as far back as version 1.2. Unsurprisingly, the most popular OS platform was linux/amd64, accounting for over 99% of instances.
The report concludes with recommendations on mitigation, including using strong authentication for access or blocking access at the firewall level, or operating kube-proxy in IPVS (IP Virtual Server) mode.
As ever, the advice is to be wary of default settings.
Vulnerability: Swagger-UI library vulnerable to DOM XSS attacks
PortSwigger has revealed details of a DOM XSS vulnerability in the Swagger-UI open-source suite that could potentially lead to account takeover.
Swagger-UI is a popular user interface component by SmartBear Software, allowing developers to present a UI within their application that exposes details of the underlying APIs in an intuitive graphical manner. The security researchers revealed that over sixty instances including some large enterprises like GitLab and Microsoft were both investigating the issue, and a wide range of versions of Swagger-UI are affected. The recommendation is to upgrade to the most recent version of Swagger-UI, at the time of writing v4.11.1.
The root cause of the vulnerability was an outdated version of the DomPurify component, an XML sanitizer library. This allowed users to provide a URL to an API definition that could contain malicious content, resulting in a cross-site scripting (XSS) exploit. The researchers easily created a working exploit that resulted in the execution of JavaScript code in the victim’s browser, allowing account takeover.
Readers of this newsletter using the Swagger-UI are urged to check the versions they have deployed and update accordingly.
Article: Google’s seven trends for the future of the API economy
Google recently contributed views on seven trends for the future of the API economy. As organizations become increasingly competitive, they are increasingly leveraging APIs to accelerate their transformation. Google’s seven ideas are:
- API security takes center stage.
- Microservices APIs are gaining speed.
- Event-driven architecture (EDA) continues its big comeback.
- GraphQL will accelerate BFF (Backends for Frontends).
- It’s not one API gateway to rule them all anymore.
- Conversational APIs go mainstream.
- From shadow IT to strategic IT.
Of most interest to readers will are their views of API security: quoting Gartner, the authors cite the fact that APIs are now the primary attack surface for breaches in 2022.
The key takeaway for the authors is that the traditional fixed security perimeters are being eroded as organizations move toward a more distributed and open architecture. The prediction is that a zero-trust model based on encryption, identity, strong authentication, and authorization will be increasingly adopted.
Guide: Beginner’s guide to API keys usage and best practice
Finally this week, we have a guide from HackerNoon on API keys, their usage, and best practices targeted at beginners to API security.
The guide covers several key topics, such as authentication, authorization, access rights, scopes, securing API keys, and security safeguards. It also provides some basic, sensible best practices for API key handling:
- Create rate limits on API endpoints.
- Use attack-detection methods to detect unexpected behavior.
- Reject requests that are out of the norm.
- Perform API key rotation and revocation.
- Use JSON web tokens (JWTs) for authentication and authorization.
- Always monitor API access and usage.
An easy read on an important topic to API security.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy