This week, Kubernetes API server was found vulnerable to the Billion laughs attack, NIST has opened their Zero Trust Architecture guidelines for commenting, and VS Code OpenAPI extension got an update with API Contract Security Audit built-in.
Vulnerabilities: Kubernetes
The Kubernetes API server is currently vulnerable to the so-called Billion laughs attack. This is the term typically used for XML expansion denial-of-service attacks. An XML sent through an API has a built-in recursion to overload XML parsers.
In case of Kubernetes, attackers can use an API to create a ConfigMap with the recursion in the YAML manifest like the one shown below:
apiVersion: v1
data:
a: &a ["web","web","web","web","web","web","web","web","web"]
b: &b [*a,*a,*a,*a,*a,*a,*a,*a,*a]
c: &c [*b,*b,*b,*b,*b,*b,*b,*b,*b]
d: &d [*c,*c,*c,*c,*c,*c,*c,*c,*c]
e: &e [*d,*d,*d,*d,*d,*d,*d,*d,*d]
f: &f [*e,*e,*e,*e,*e,*e,*e,*e,*e]
g: &g [*f,*f,*f,*f,*f,*f,*f,*f,*f]
h: &h [*g,*g,*g,*g,*g,*g,*g,*g,*g]
i: &i [*h,*h,*h,*h,*h,*h,*h,*h,*h]
kind: ConfigMap
metadata:
name: yaml-bomb
namespace: defaultWhen the API server attempts to expand the structure, it overloads the CPU and becomes unresponsive.
The patches for this vulnerability are coming in the next updates for Kubernetes. For now, it is recommended that you limit the access to the vulnerable API:
- Limit access to trusted accounts only
- Review user roles and their membership
- Consider removing internet access
Standards: NIST Zero Trust Architecture
US National Institute of Standards and Technology (NIST) has published their Zero Trust Architecture: Draft NIST SP 800-207.
Proliferation of microservices along with mobile, IoT, cloud, and hybrid applications has reduced the effectiveness of edge protection. All these trends made Zero Trust approach to API security extremely relevant.
Quoting from the document:
A Zero Trust Architecture (ZTA) strategy is one where there is no implicit trust granted to systems based on their physical or network location (i.e., local area networks vs. the Internet). Access to data resources is granted when the resource is required, and authentication (both user and device) is performed before the connection is established. ZTA is a response to enterprise network trends that include remote users and cloud-based assets that are not located within an enterprise-owned network boundary. ZTA focuses on protecting resources, not network segments, as the network location is no longer seen as the prime component to the security posture of the resource. This document contains an abstract definition of ZTA and gives general deployment models and use cases where ZTA could improve an enterprise’s overall IT security posture.
The document is open for public commenting until November 22, 2019.
Tools: API Contract Security Audit in VS Code
OpenAPI / Swagger Editor is a popular extension for Visual Studio Code. Thousands of developers use it when developing REST APIs. It provides API navigation, code-snippets, and linting. In this week’s update, it can now also provide static analysis of the API definition through API Contract Security Audit.
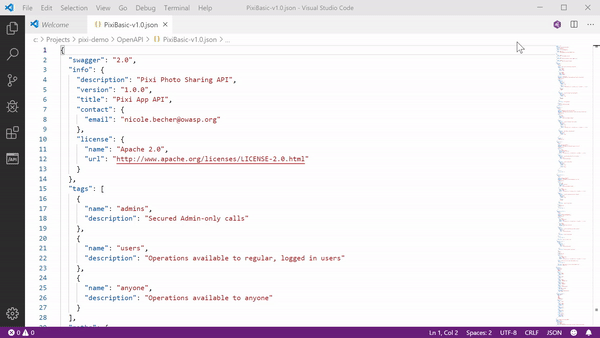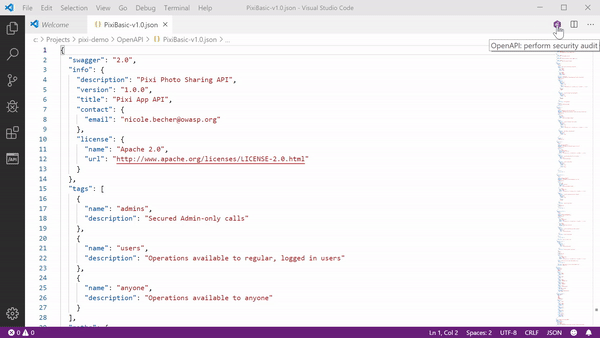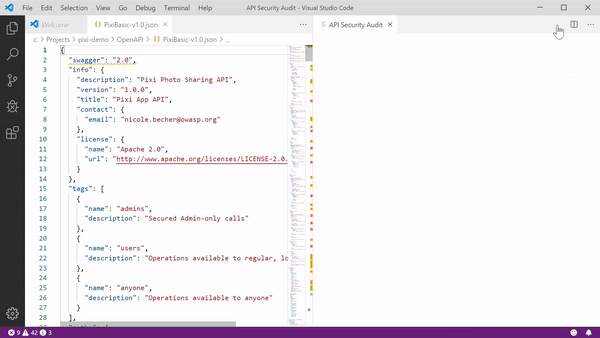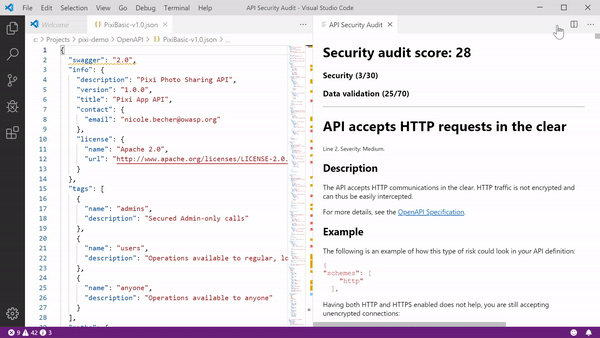
The functionality uses a remote API security verification service from 42Crunch. When you open an API contract in VS Code and click the Security Audit button, the extension runs over 200 various checks on the API and its security. These includes checks for best practices in authentication, authorization, transport, and data inputs and outputs.
The analysis is static, so it does not make any calls to the actual API endpoint.
The reports also provide information on the possible exploit scenarios of the security risks and recommended ways to mitigate them.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy