This week, we have new research in APIs that reveals how they are increasingly used for account takeover, a look at a great new book on hacking APIs, an article on using Postman for OAuth 2.0 authorization code grants, and a guide on documenting APIs.
Article: APIs increasingly used for account takeover
New research covered by Security Boulevard reveals how APIs are increasingly favored by developers: they are becoming the development tool of choice, with data indicating that of the 21.1 billion application requests analyzed, nearly 70% of them were API-based.
Unfortunately, APIs are also the favorite attack vector for adversaries: correspondingly, the data indicated that 80% of blocked attacks were targeting APIs. In particular, the research revealed a 62% increase in account takeovers (ATO) using login APIs. Most notably, the attacks increasingly focused on account logins and registrations. Common examples were attacks against gift card sites, such as card and points theft, and semi-automated large-scale attacks against loan sites.
The report also revealed a 178% increase in API-based content scraping. Although apparently benign, large-scale content scraping can lead to revenue loss for the organizations that own that data. Typical examples of data scraping included inventory pricing, stock levels, market data, and social media data.
An interesting observation made in the article is that well-documented and discoverable APIs (either by virtue of OpenAPI definitions or GraphQL endpoints) can actually facilitate attacks. No longer do attackers have to enumerate API endpoints, but instead can easily leverage the definitions. However, this does not definitely mean that APIs should not be documented, but perhaps some consideration is needed on the intended (and unintended) audience and how exactly to reach them.
The article provides the following sound recommendations for improving API security:
- API discovery and inventory tracking: Ensure that your organization maintains an accurate inventory of APIs to avoid exposing unnecessary attack surface, and make sure all APIs have assigned owners.
- API risk assessment and remediation: Assess APIs for common weaknesses and drive remediating or mitigating vulnerabilities.
- Native, inline protection for attacks and vulnerability exploits: Use a defense-in-depth approach by leveraging API firewalls and gateways for inline protection.
Review: “Hacking APIs” by Corey Ball
My last few evenings have been spent reading “Hacking APIs” by Corey Ball, available now as early access form from NoStarch Press. I have no doubt this book is destined to become the industry handbook for API security aficionados in years to come, and would recommend this to readers of this newsletter regardless of experience.
The book tackles a broad topic primarily from the perspective of a pentester but makes few assumptions on prior knowledge. I certainly learned a great deal about API discovery, bug bounty programs, and disclosure. The chapters on how to evade standard controls and countermeasures were particularly interesting — for defenders, this should prove quite eye-opening indeed!
On a personal level, I found myself inspired to get a lot more hands-on with APIs, hopefully there is a disclosure with my name on it soon.
Thanks to Corey for the great work and contribution to the community. Highly recommended.
Guide: Using Postman for OAuth 2.0 authorization code grants
Following on from the popular best practice for API authentication and authorization featured last week, we have a quick guide on how to use Postman to implement the OAuth 2.0 authorization code grant flow.
The guide describes how to use Postman acting as a client to obtain an authorization code, and how then to use the code to gain access and refresh tokens. The popular Keycloak server acts as the authorization server in this example.
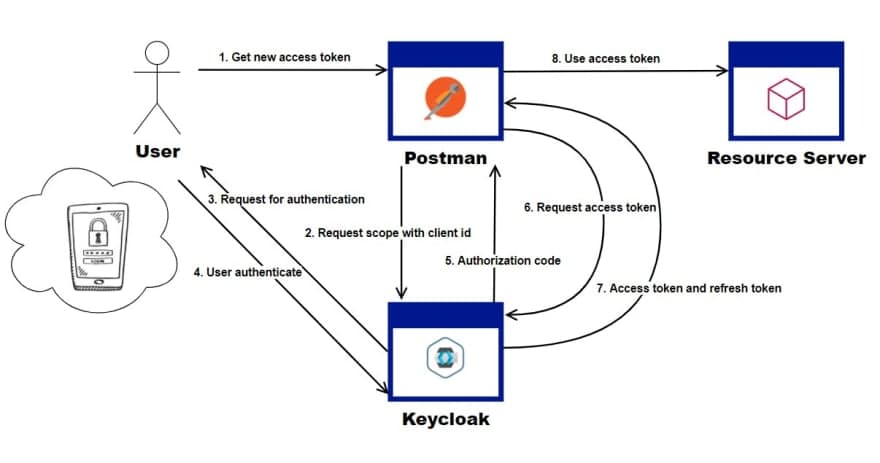
This is a great guide to help developers understand this important OAuth 2.0 flow in a very hands-on manner, and I look forward to the next article describing the PKCE extension to this flow.
Guide: Comprehensive guide to API documentation
Good API documentation is essential in enabling downstream API consumption by end users. Well-documented APIs also enable effective security implementations: for example, illustrative code samples and associated documentation can guide end-users to correctly implement authentication workflows.
I’ve found myself frequently referring to the excellent and comprehensive guide by Tom Johnson on a variety of API documentation topics. This is worth bookmarking for anyone engaged in writing or documenting APIs.
Webinar: Protection of your data from API to mobile application
Finally, a reminder that on Tuesday, 8 March at 11 AM (EST) / 4 PM (GMT), I am joined by David Stewart, CEO of Approov. We discuss an approach to how to provide shift-left API protection as well as runtime shielding that extends all the way to your mobile apps and the environments they run in.
In this webinar, we will present:
- The threat to APIs posed by mobile apps.
- How Approov shields mobile apps from cloning and modification and defends against manipulation of the client environment.
- How these checks can be seamlessly integrated into 42Crunch API Security Platform to provide visibility and protection all the way to the API backend by using a “security as code” approach.
- The benefits of the unified API protection offered by the joint 42Crunch/Approov solution.
- A demonstration of the integrated solution in action.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy