This week, we look at the recently patched API vulnerabilities in Microsoft Azure Stack and Azure Cloud infrastructure, and in Cisco TelePresence and RoomOS. In addition, there is a recorded conference talk on API pentesting, and Yelp has released an open-source tool for API fuzzing.
Vulnerability: Azure Cloud infrastructure
Ronen Shustin from Checkpoint Research has reported two API vulnerabilities in Azure Cloud infrastructure, and has written very detailed description on them. Microsoft has already fixed both vulnerabilities.
The first vulnerability was found in Azure Stack, Microsoft’s on-premise Azure environment for enterprise use. Researchers used Azure Stack APIs to get the names, IDs, hardware info, and other information on the virtual machines in the cluster. Then they found a way to make another unauthenticated API call to get screenshots from live virtual machines belonging to other tenants.
The second vulnerability was found in Azure App Service. One of its APIs lacked proper input validation before memory copy. This allowed the researchers to come up with a payload that gave them system admin rights.
API security is crucial to cloud services. If the API can access sensitive information that could open a door for further attacks, it must require authentication. And the importance of proper validation of input and output data cannot be stressed enough.
Vulnerability: Cisco TelePresence and RoomOS
Cisco has fixed an API vulnerability in their TelePresence and Webex Board, DX, and Room products.
Insufficient validation of user-supplied API parameters in a video endpoint API led to directory traversal vulnerability in Cisco TelePresence products and products using the RoomOS. If attackers had either an In-Room Control or administrator account, they could craft an API request that allowed them to read and write arbitrary files in the system.
Check out Cisco’s disclosure for full list of affected products and fixes product versions. We have covered previous issues in Cisco products in our newsletters 30, 42, 43, 46, 47, 51, 55, and 65.
Video: API fuzzing and pentesting
A recording of Frans Rosén’s keynote at BSides Ahmedabad is now available.
Rosén discusses the methodology of fuzzing and information disclosure: discovering API vulnerabilities through fuzzing, discovering endpoints or hidden backend microservices, bypassing internal security mechanisms, getting info from errors, forging JWT, and so forth.
Not the best camerawork, but good content and excellent speaker, so still good to check out.
Tools: Yelp Fuzz-Lightyear
Broken Object Level Authorization (BOLA) tops the OWASP API Security Top 10 list. Yelp has released a new open source tool called fuzz-lightyear.
This scanner helps locating BOLA (aka IDOR) vulnerabilities in your APIs. Because you can execute it from your CI/CD pipeline, it can potentially discover these at scale.
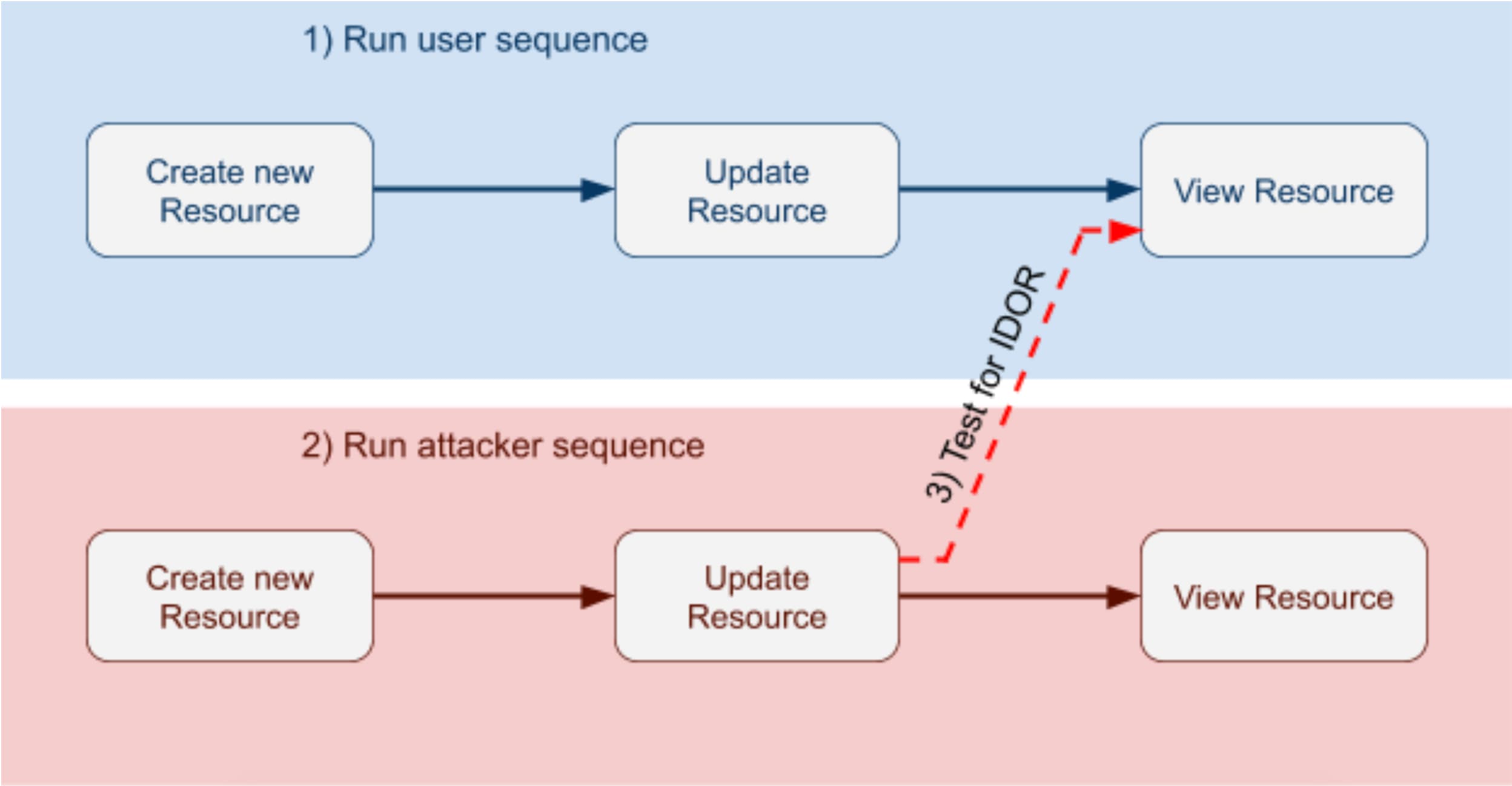
You can find the source code of the tool in this GitHub repository.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy