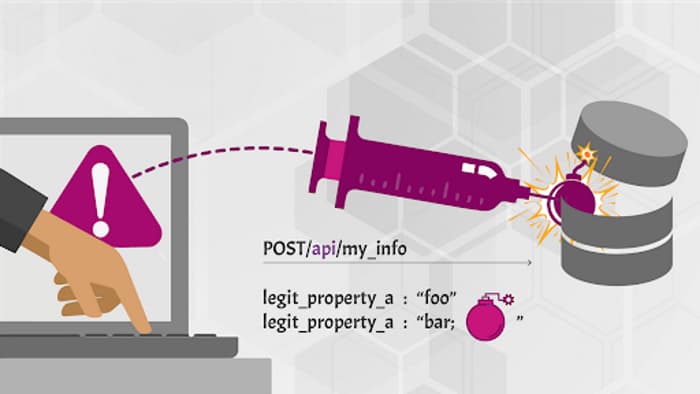
Attackers construct API calls that include SQL, NoSQL, LDAP, OS, or other commands that the API or the backend behind it blindly executes.
Use cases
- Attackers send malicious input to be forwarded to an internal interpreter:
- SQL
- NoSQL
- LDAP
- OS commands
- XML parsers
- Object-Relational Mapping (ORM)
How to prevent
- Never trust your API consumers, even if they are internal.
- Strictly define all input data, such as schemas, types, and string patterns, and enforce them at runtime.
- Validate, filter, and sanitize all incoming data.
- Define, limit, and enforce API outputs to prevent data leaks.
Full OWASP API Security Top 10 2023 list
Full OWASP API Security Top 10 2019 list