This week, we look into some recent API vulnerability reports on YouTube and Amazon’s Ring Neighbors app, there is a new proposed addition to the OAuth standard, and Google has developed an API proxy extension for Chrome.
Vulnerability: YouTube
David Schütz found a clever way to get (limited) access to private YouTube videos via a vulnerable API.
Schütz noticed that Google Ads allows users to generate a video thumbnail for a given point in time:
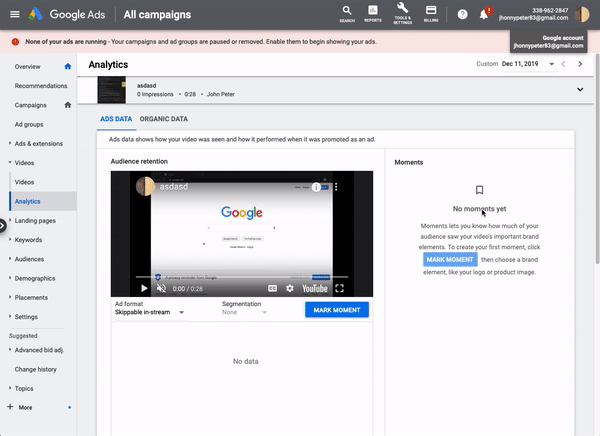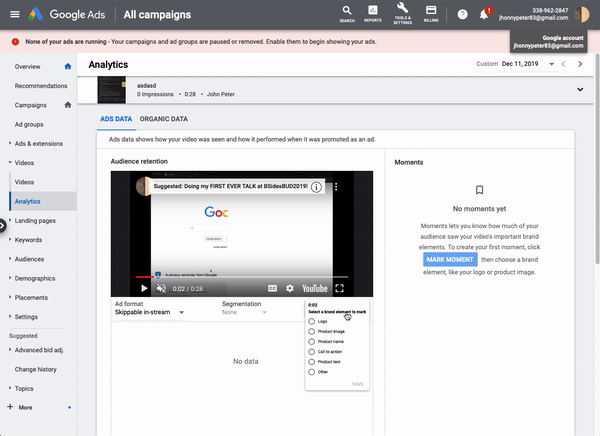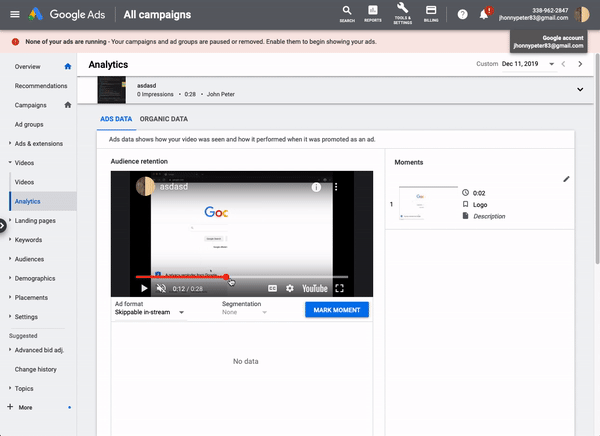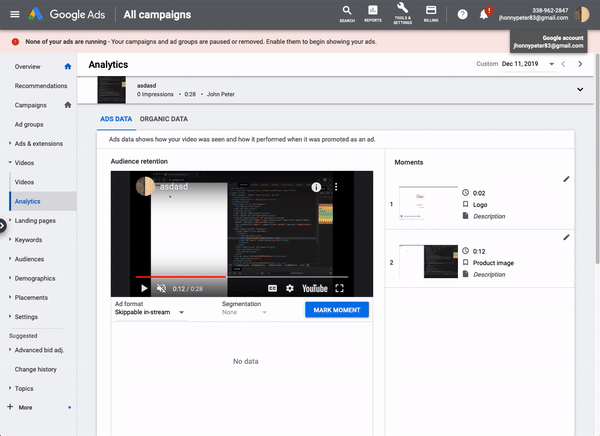
Schütz looked at the underlying API call and found that the payload had two parameters:
- The ID of the video
- The timestamp where to extract the frame
POST /aw_video/_/rpc/VideoMomentService/GetThumbnails HTTP/1.1
Host: ads.google.com
User-Agent: Internet-Explorer-6
Cookie: [redacted]
__ar={"1":"kCTeqs1F4ME","2":"12240","3":"387719230"}It turned out that this API call made the API return a Base64-encoded image of the frame in question. The API didn’t perform any authorization checks, so attackers could supply an ID of someone else’s private video and get the frame from that video.
This would have allowed them to steal the video content one frame at a time using a script to iterate multiple calls. Here’s a video demonstrating the proof-of-concept attack:
No sound was retrieved, and obviously, the attacker would have needed to know the ID of the private video beforehand, so there were some limitations as to how readily this could have been exploited. Nevertheless, this still is a Broken Object-Level Authorization vulnerability (BOLA/IDOR), and Google did award Schütz $5,000 for the report. The vulnerability has since been fixed.
Lessons learned in this one:
- APIs shared between different services can be vulnerable to attacks because the teams working on each service may be using different security and data models and may overly trust the caller.
- Authorization is critical to API security. Any time you have an API call with a resource identifier as a parameter, implement access rights checks!
Vulnerability: Amazon Ring Neighbors
Amazon’s Ring camera has a companion app called Neighbors. The app allows users to anonymously share footage that they deem suspicious.
While the data was supposed to be anonymous, in reality, the API has turned out to be extremely leaky. As shown in the picture below, it provides the exact geographic coordinates and the address of the sharer:
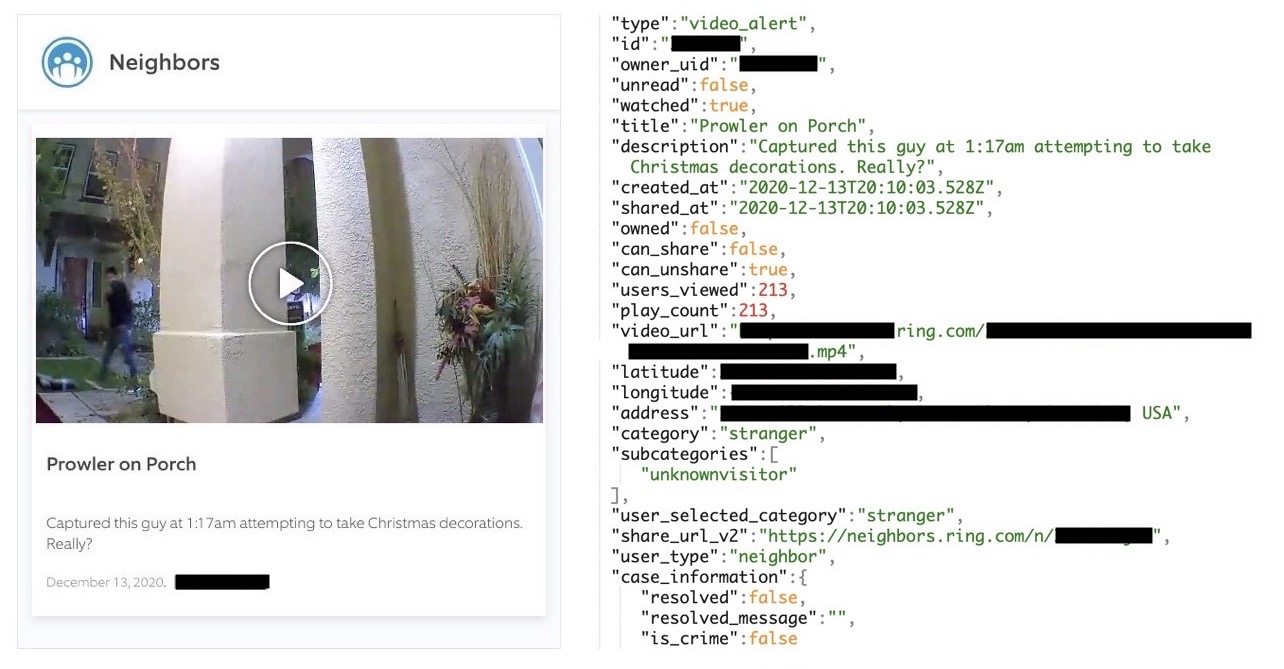
Even worse, the posts had sequential IDs that could be enumerated. Thus, attackers could retrieve the addresses of many camera owners.
Lessons learned:
- This is a classical OWASP API:3 Excessive data exposure vulnerability.
- Treat your APIs as your user interface. Data that users are not supposed to see should not be returned by your APIs either.
- Avoid sequential IDs — generate random ones instead.
We have previously covered vulnerabilities in the Neighbors app in our issue 62 and vulnerabilities in Amazon Ring itself in issues 57 and 21.
Standards: OAuth 2.0 Authorization Server Issuer Identifier in Authorization Response
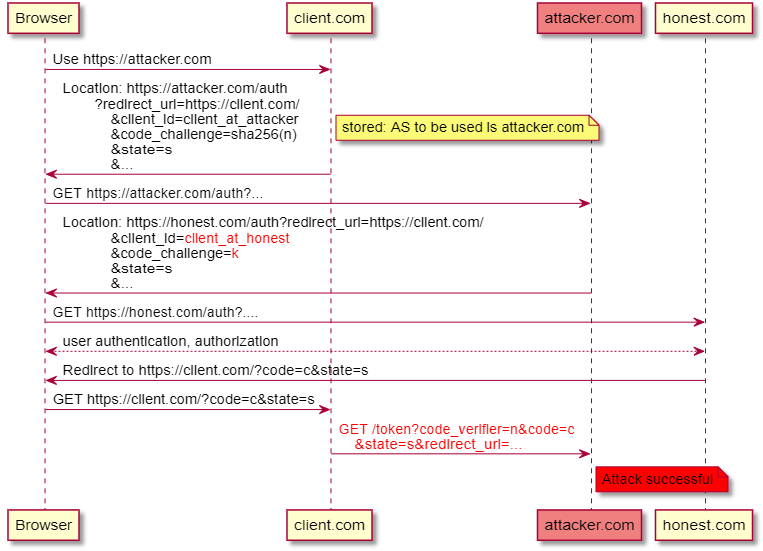
We discussed OAuth 2.0 Mix-Up attacks in issue 83. In a mix-up attack on OAuth authentication, an attacker convinces the OAuth client to send credentials (authorization code or access token) that the client obtained from an “honest” authorization server to the attacker’s server:
Now, the IETF OAuth Working Group has formally published a standard proposal by Karsten Meyer zu Selhausen and Daniel Fett on using the iss parameter for OAuth Authorization Responses to prevent such attacks.
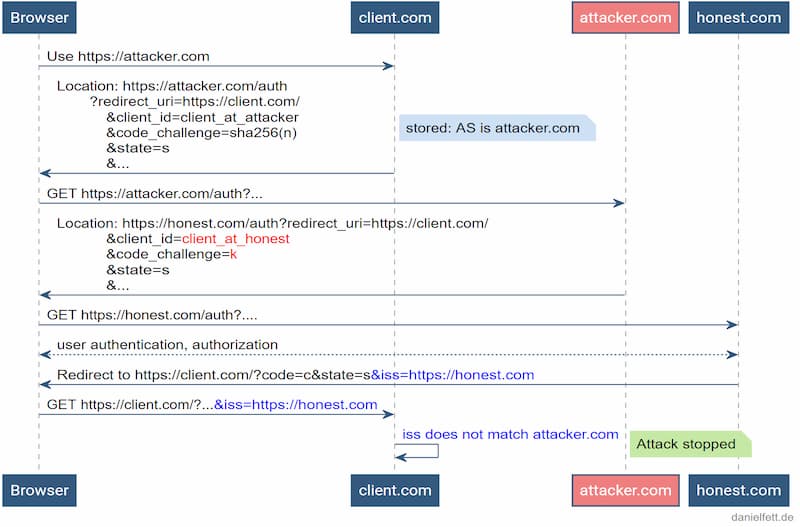
This is a draft (expiring July 10, 2021), and the working group welcomes feedback on it.
Tools: Tamper Dev
Proxy tools, like Burp and Zap, have long been popular among penetration testers. They allow intercepting calls between a web application and the underlying APIs and then replaying these calls while tweaking the parameters to find possible vulnerabilities.
A team at Google has gone a step further and released a Chrome extension that does just that. Tamper Dev allows you to intercept and edit HTTP/HTTPS requests and responses as they happen, right within your browser, without the need for an external proxy.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy