This week, we check out an API vulnerability in India’s coronavirus tracing app, a couple of write-ups on OAuth2 API attacks, and a recording of a talk on REST API penetration testing.
Vulnerability: India’s coronavirus tracing app
Elliot Alderson discovered API flaws in India’s COVID-19 tracking app, Aarogya Setu. In certain regions, the app is mandatory, and not having it installed can lead to fines or even jail time.
The app can tell users how many people who have tested positive for COVID-19, or who have self-assessed to feel unwell, are nearby within the radius of from 500 meters to 10 kilometres. Or at least that is the theory. In practice, attackers can make the app to show them more.
Alderson found a combination of factors that allowed malicious use of the API:
- He overcame the checks for device rooting as well as certificate pinning, and got direct access to the API behind the app.
- He could supply any latitude and longitude values to the API, and receive the data for a particular neighborhood.
- He could tweak the catchment area to whatever he wanted because the predefined radius values were only in the client app, not enforced in the API.
[UPDATE] One of the readers shared this counter-story publication debunking some of the claims in the original article. For example, looks like the app creators (at least as of right now) have implemented radius parameter validation on the API side. If an unexpected value is sent (e.g. 50 meters) the parameter defaults to 1 kilometre.
This means that an attacker could home in on someone and get the data for a specific address.
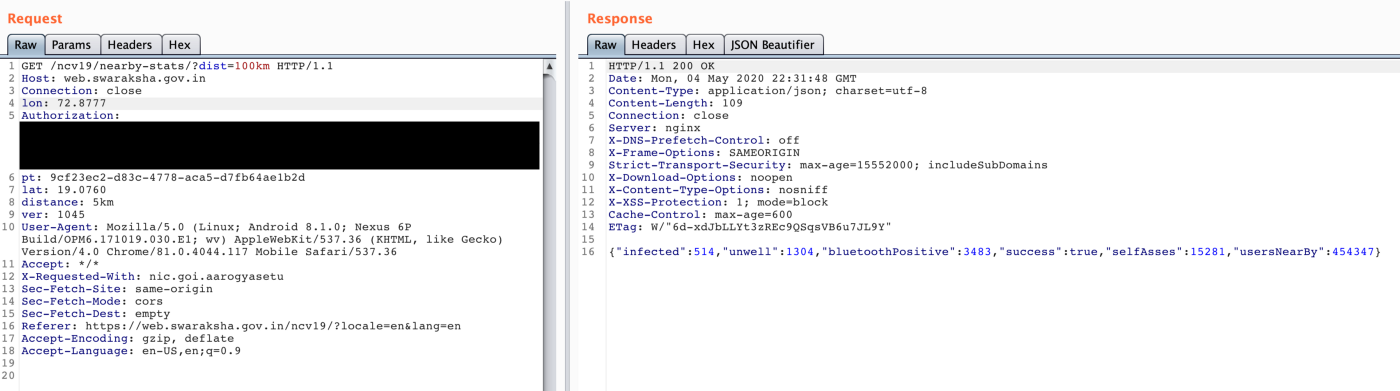
Bulk API calls were allowed, too. Thus, by invoking the API for a mesh of locations, the attacker can further triangulate the exact locations of infected people.
Not really something you’d like to see in an app that deals with such sensitive information and that you are forced to use.
[UPDATE2] Looks like there is some prevention from bulk calls now in place. According to Sunny Nehra: “I was using multiple calls.. all of a sudden got logged out after some calls and it did not let me login for some time with same phone number. I am trying to understand it better (though change of lat/long was quite much in my case) regarding server end filtering/restrictions”
Lessons learned here:
- Even seemingly anonymous data can become personal when combined with other data, especially geolocation.
- You cannot rely on your APIs being only invoked by your client app. Someone might (will!) figure out a way to get to them directly.
- Parameter ranges must be enforced on the API level, not just on the UI.
- Bulk API calls are a source of data leaks.
Attack scenarios: OAuth Mix-Up, Revisited
Dr. Daniel Fett has published a great detailed document on OAuth mix-up attack scenarios and ways to mitigate them. He covers, for example:
- Basic mix-up attack
- Mix-up attacks with OAuth metadata
- Mix-up attacks with Pushed Authorization Request (PAR) endpoint
- Integrity of the Authorization Request with PAR
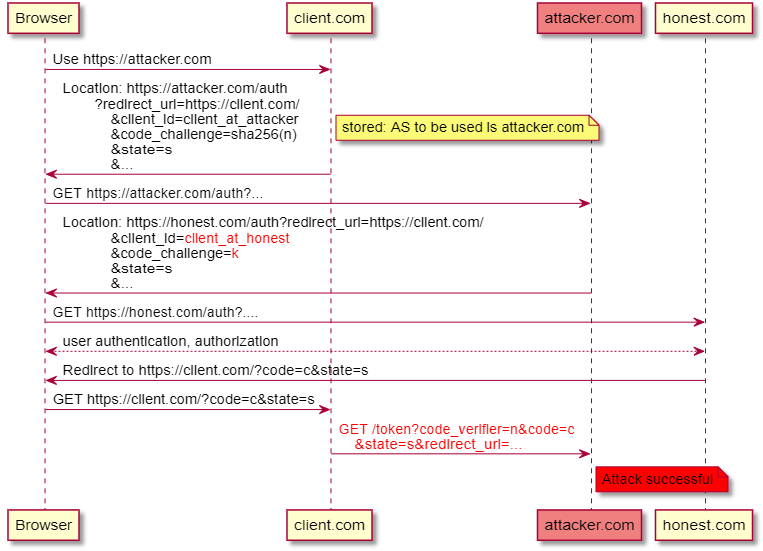
In a mix-up attack on OAuth authentication, an attacker convinces the OAuth client to send credentials (authorization code or access token) that it obtained from an “honest” authorization server to the attacker’s server:
Tips and tricks: Pentesting OAuth
And while we are in the world of OAuth, the blog A Bug’z Life has a post on the typical security flaws in OAuth implementations:
- Weak
redirect_uriconfiguration - Improper handling of state parameter
- Assignment of accounts based on email address
- Disclosure of secrets
Check it out to be reminded of and avoid the common pitfalls.
Video: API Hacking for the Actually Pretty Inexperienced hacker
On the latest episode of the OWASP DevSlop show, Katie Paxton-Fear gave a talk on REST API hacking. Her talk focused on the following vulnerabilities from the OWASP API Security Top 10 list:
- API1:2019 — Broken object level authorization
- API3:2019 — Excessive data exposure
- API5:2019 — Broken function level authorization.
The talk included a demonstration of each of the flaws and practical tips on how to find them. The source code of the demo app is also available.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy