This week, unprotected APIs have allowed hackers to compile to put on sale a list of 1.4 million of US doctors, and GitLab has published details on the API vulnerability they recently fixed. We also have a recording of a recent API security conference talk, and an announcement of an upcoming training on OAuth and OpenID Connect.
Vulnerability: findadoctor.com
In healthcare sector, it is not just leaks on patient information that can pose big problems, the details of practitioners could do with securing, too, like in the case of findadoctor.com.
This online service in the US does what the name says: find healthcare professionals near you. Hackers used insecure APIs behind the website qa.findadoctor.com to scrape information on 1.4 million doctors in the US. Naturally, they promptly put it on sale.
You might ask why this would be a problem, the service was already providing these details to users after all. While the information was indeed public on the site itself, the unprotected API allowed downloading all of it and making it available in a structured form. A nice little dataset to use for further attacks.
Lists like this are often exploited, for example, in phishing campaigns. In this particular case, email addresses were thankfully not included in the dataset, but could potentially be added using some heuristics or external sources. However, the phone numbers are there, so SMS phishing (smishing) is still very much possible.
Just like databases, even APIs sharing data from public domain need to be protected. To start with, establish reasonable rate limiting, authentication, and filtering by invocation source.
Vulnerability: GitLab
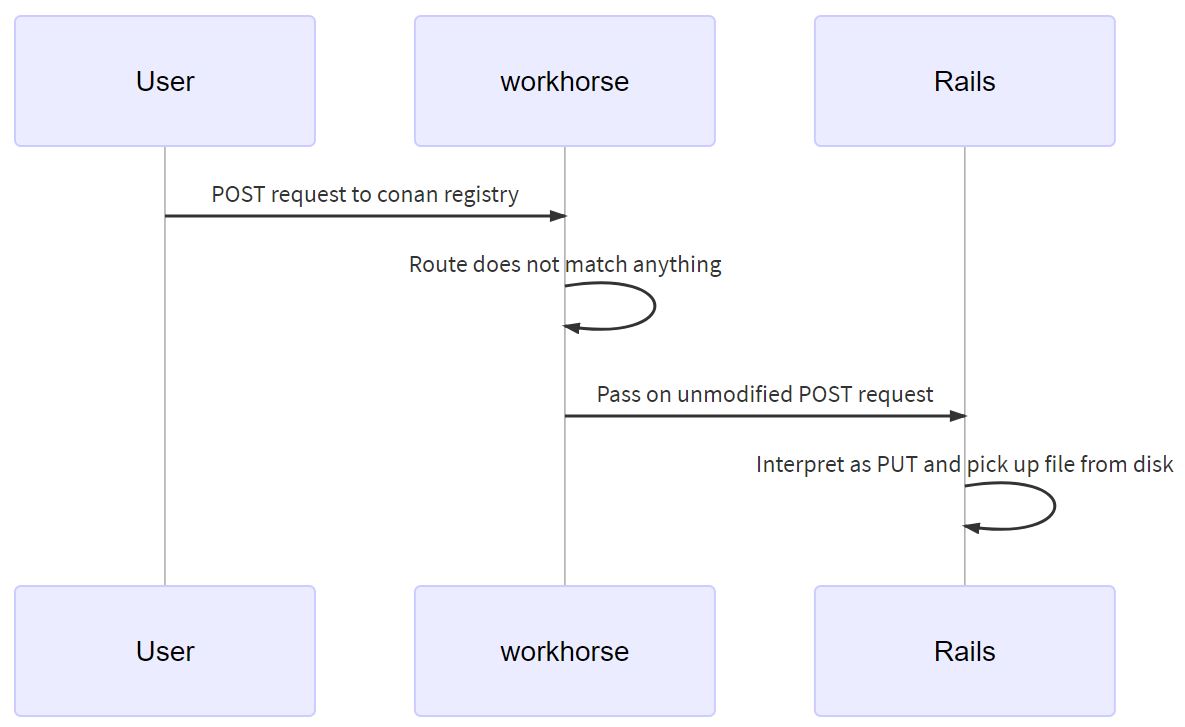
GitLab has posted more details on the root cause of their API vulnerability we covered in our previous newsletter.
In short, the vulnerability emerged out of file uploads and the differences in how the gitlab-workhorse and gitlab-rails components were treating and parsing PUT and POST requests.
Good lesson on how subtle inconsistencies in implementation of the same functionality in different parts of the stack can lead to vulnerabilities.
Conference talk: Attacking Secondary Contexts in Web Applications
Sam Curry has posted the slides and the video (see below) from his recent Kernelcon talk, “Attacking Secondary Contexts in Web Applications”.
Significant part of the presentation concentrates on turning a web application attack into an API attack, so definitely of interest for API security.
Online training: Mastering OAuth 2.0 and OpenID Connect
OAuth2 and OpenID Connect have become the cornerstones of modern API, web, and mobile security. Yet a lot of developers still find them quite confusing.
Now that in-person training is not an option, Philippe De Ryck is offering his course on this very topic online. The next course starts on May 11, 2020. Click here to find more details and to enroll.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy