This week, we have the recently reported API vulnerability in Duffel’s Paginator, a new API fuzzer from Microsoft Research, an upcoming JWT security webinar, and a recorded talk on approaches to API authentication.
Vulnerability: Paginator
Peter Stöckli from Alphabot Security has posted a write-up on the API vulnerability he found in Duffel’s Paginator (CVE-2020-15150).
Duffel is a UK-based startup in that offers a flight searching and booking platform that other businesses can build their sites on. They maintain an Elixir-based open-source project called Paginator. This component helps them and other products implement pagination in API calls. Instead of retrieving all values, API consumers can retrieve only a subset of them. A “cursor” value points the place where they left off before:
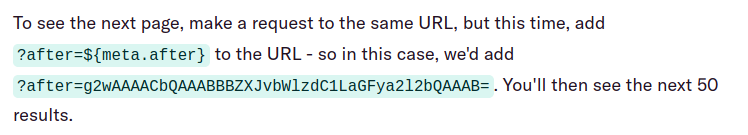
This cursor value is not a random string but a Base64-encoded binary serialized Erlang external term format (ETF). ETFs can be pretty much anything, from a simple string to a complete executable function. In Duffel’s case, Paginator blindly trusted the API input, allowing Stöckli to execute arbitrary code on the target system, such as starting xcalc and printing out the stacktrace.
A prime example of the OWASP API8:2019 — Injection vulnerability. Lessons learned here:
- Be very careful when using external components that expose APIs.
- API inputs cannot be trusted: instead of coming from your own components, API calls might originate from an attacker.
- Beware of using interpreters on strings that originate from API input.
- Always strictly define API parameters and payloads, including string patterns, and enforce them.
Tools: RESTLer
Microsoft Research has made their API fuzzing project, RESTLer, opensource.
Just like the other two REST API fuzzers that we have covered before, RESTLer takes the OpenAPI contract file as the API definition it bases the generated tests on. However, the subsequent scenario is very different:
- RESTLer tries to automatically infer multi-step scenarios. For example, it looks for outputs from one operation that work as inputs for another one, or incompatible operation sequences that always fail. It then executes those scenarios while trying various parameters within allowed ranges, and reports the calls that resulted in errors.
- Dredd generates calls within the limitations of the defined OpenAPI contract and reports the responses that do not match the defined responses.
- 42Crunch API Contract Conformance Scan generates tests for both request and response validation. It sends purposefully invalid requests (wrong paths, operations, headers, parameters, payloads…) and reports if they do not get rejected. Just like Dredd, it also reports responses that do not match the contract.
Read the details on how RESTLer works from the original research paper. This whitepaper showcases some real-life results of RESTLer locating bugs in GitLab APIs.
Webinar: How to Best Leverage JWTs for API Security
Next Thursday, December 10, at 8 AM (PST) Isabelle Mauny and I, Dmitry Sotnikov, are hosting a webinar on JWT and API security. We cover common JWT attacks, security best practices, and technology that can be used to protect your APIs against them.
For more details and to sign up for the webinar, click here.
Video: Serving the right recipe for API authentication
Philippe De Ryck has posted the slides and the recording from his recent talk “Serving the right recipe for API authentication” at the Belgian Visual Studio User Group (Visug).
There are many ways how API authentication can be implemented, and your own scenario will determine which is the right one for you. De Ryck covers the main options used in the industry today, how they work, when and where they are applicable, as well as their pros and cons:
- Basic authentication
- Shared secret
- HMAC
- Asymmetric signatures
- Mutual TLS (mTLS)
- Cookies
- Tokens
- OAuth2
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy