This week, we check out the recent API-related vulnerabilities at Twitter and Grandstream Networks, the newly added support for mutual TLS (mTLS) in AWS API Gateway, and the API security episode in the Application Security Podcast.
Vulnerability: Twitter
A misconfiguration in the Twitter developer portal caused browsers to cache API keys, account access tokens, and account secrets.
It is highly unlikely that the vulnerability has been exploited. Not only would attackers have to had known about the vulnerability, they would also have needed physical access to the computers of their victims. That being said, this flaw could potentially had leaked these secrets on shared computers.
To avoid issues like this one, make sure you never cache any sensitive data on client-side.
Vulnerability: Grandstream Networks
Grandstream Networks is a global provider for IP video and voice services as well as WiFi and related services and equipment, and they operate in over 150 countries around the world.
The about 5 million Grandstream devices and services are managed in their GWN.Cloud management platform. Researchers from Pen Test Partners took a look at the platform and found vulnerabilities in the APIs behind it.
The web UI used an API to change device and network settings. When a user applied changes, the web UI invoked a POST operation where the networkIds field in the JSON payload contained the ID of the network to be configured:
POST /app/user/save HTTP/1.1
Host: www.gwn.cloud
Connection: close
Content-Length: 72
Accept: application/json, text/plain, */*
Origin: https://www.gwn.cloud
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.157 Safari/537.36
Content-Type: application/json;charset=UTF-8
Referer: https://www.gwn.cloud/account/users
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: SESSION=7672dd7d-58a7-47f2-8bbc-3534108e4987
{"email":"egw@mailinator.com",
"roleId":2,"
networkIds":[
16089
],The problem was that this API never checked if the user was actually the owner of the network or in any way authorized to give access to it. Anyone could change settings of any network managed in through the Grandstream portal.
To make matters worse, the IDs were also sequential integers, making it possible to enumerate through them, and change settings and retrieve information, such as:
- View and change WiFi passwords
- Switch off all devices
- Get information on access points
- Get information on WiFi clients (computer or phone name)
- Get SSH passwords of all devices
- Get system logs
- Enable URL access log (all URLs clients have visited)
This is a classic example of the Broken Object-Level Authorization (BOLA / IDOR) vulnerability, which is the number one in OWASP API Security Top 10). To avoid it:
- Ensure that you perform authorization checks on object access.
- Avoid sequential identifiers.
Tools: mutual TLS support in AWS API Gateway
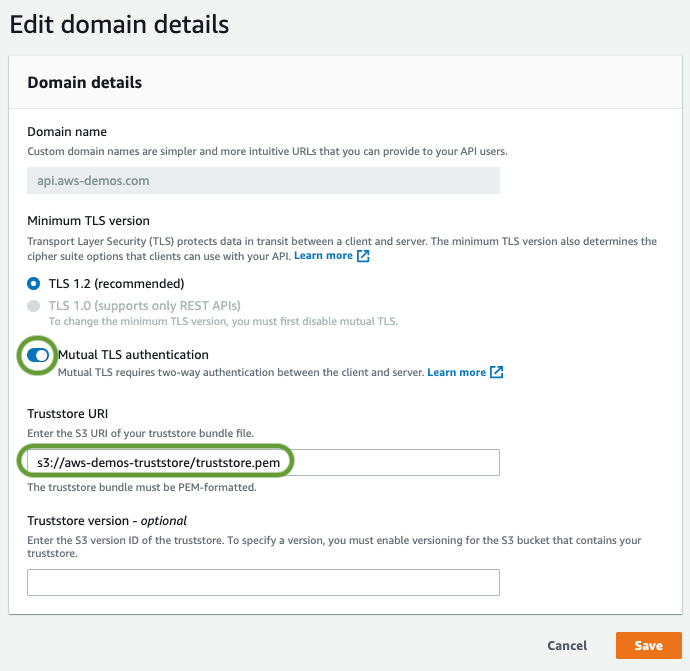
Amazon has finally added mutual certificate authentication option (mutual TLS) to AWS API Gateway .
If your API is hosted in AWS and you use custom domain endpoints, you can upload your certificates and have API clients authenticate that way. You can still continue to use JWT and other mechanisms in addition to mTLS.
Podcast: API security at the AppSec Podcast
If you are not a subscriber of the Application Security Podcast, you should definitely check it out. Every week, the hosts Chris Romeo and Robert Hurlbut have a guest and discuss a specific area of application security.
I took part in their latest episode and we had a lovely discussion of API Security, what makes it different from web application security, top threats, most effective counter-measures, and lots of real life stories.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy