This week, we check out how Microsoft Teams could be breached with a single GIF image sent in a chat, and Auth0 by changing the case of a single character.
In other news, a report on security issues in smart home hubs has been published, and a new online training on OAuth2.0 and OpenID Connect is available.
Vulnerability: Microsoft Teams
Researchers from CyberArk found a serious vulnerability in Microsoft Teams that the vendor promptly fixed.
The attack vector was how Teams handled authentication to image resources and then allowed expansion to full API access. Here’s how the scenario went in a nutshell:
- Researches were able to take over two abandoned subdomains of
teams.microsoft.com. - The researchers used the subdomains to host a simple GIF file that they could then send to a target user. Just the victim seeing the GIF was enough to return an authentication cookie to the attackers.
- The researches then made an API call to exchange that cookie to an authentication token for the Teams APIs.
- With full API access, the researchers could scrape the victim’s chat history for messages and information. They could also use the APIs to spread the attack with messages to the victim’s colleagues.
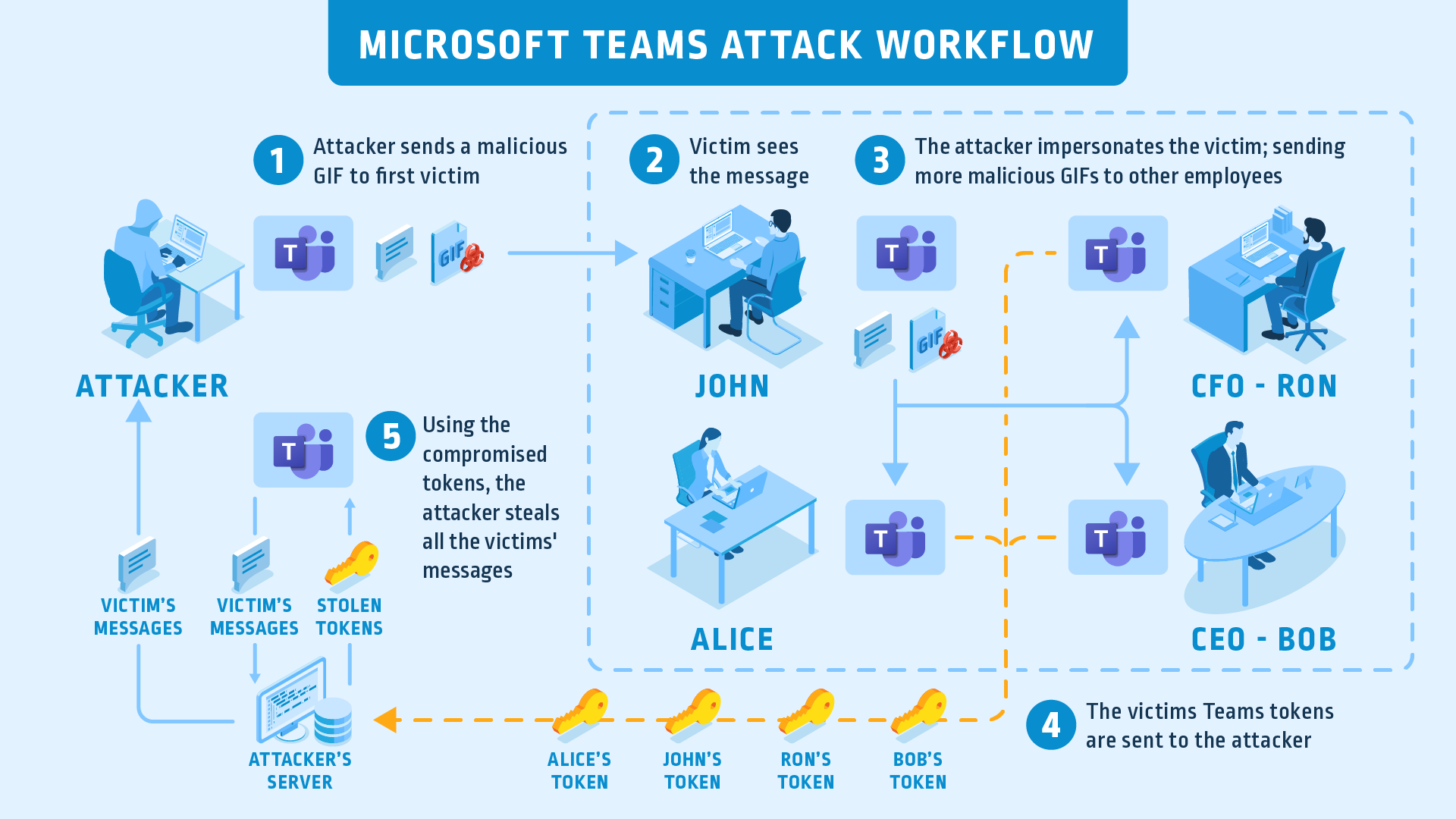
Now, since this attack did not require any interaction from the user, it could be scaled up easily without it being in anyway obvious. A co-worker suddenly spamming a GIF to everyone could raise suspicions quickly. However, a single GIF sent to a Teams group would provide the attacker authentication tokens of several users with no one batting an eye.
This is a brilliant illustration of the dangers of wildcards in URLs, token exchange, and the power that APIs can give to attackers once they get past authentication.
Vulnerability: Auth0
JSON Web Tokens (JWT) is the prevalent format of authentication tokens in modern APIs. One of the common attack vectors on JWT is forging a token and then setting the signature algorithm in the token header to alg:none. This makes poor JWT implementations blindly trust such a token and do not verify its signature. For more details on the JWT standard and JWT attack vectors, see this AppSec California session recording.
Modern tools and frameworks typically include out-of-the-box protection against this attack. However, Ben Knight found a flaw in how this protection was implemented in Auth0.
Auth0’s check for alg:none was case-sensitive. Thus attackers could go around it simply by sending alg:nonE instead. This tiny change was enough to get the check to pass and disable the signature verification, in turn allowing attackers to forge tokens.
Luckily, Auth0 has since fixed the issue. Lessons learned:
- Case-sensitive checks are dangerous
- Blacklisting (when you test for what should not happen) is more error-prone than whitelisting (when you only let through what is expecting)
Vulnerability: Fibaro, eQ‑3, and Elko smart home hubs
Researchers from ESET have disclosed API (and other) flaws in Fibaro Home Center Lite, Homematic Central Control Unit (CCU2), and eLAN-RF-003 smart home hubs that they found.
The list of vulnerabilities includes such classics as:
- Unencrypted HTTP calls
- Unsecured APIs
- Injections in URL parameters
These cases are not exactly new: they were found and reported to vendors 2 years ago. However, the details were responsibly only published now to protect the users of unpatched models.
Online training: Getting Started with OAuth and OpenID Connect
More opportunities to learn new things online: Curity has published a free online course, “Getting Started with OAuth and OpenID Connect“.
The course topics include:
- Introduction to OAuth
- OAuth vs OpenID Connect
- Tokens and APIs
- Server to Server Communication with OAuth
- Design tokens for your APIs
- Dynamic Clients and Metadata
- OAuth for Mobile Applications
- OAuth for Single Page Applications
Each lesson takes about 30 minutes, so they do not make a huge dent to your day, and you can slot them in when it bests suits you.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy