This week we look at the recent API vulnerabilities in Amazon Ring’s Neighbors app and the Droom vehicle marketplace, articles on API security and WebSockets, an opinion piece on the most exploited API vulnerabilities, and a couple of recorded webinars.
Vulnerability: Amazon Ring
Gizmodo reports that Amazon Ring’s crime-alert app, Neighbors, exposes too much data through API calls. The coordinates included in the posted videos are so detailed that the locations of cameras and the users are exposed with extremely accurate precision.
The Gizmodo journalists could even use the API to enumerate the cameras programmatically and build a detailed maps of Ring users by city.
This is not the first time we have featured vulnerabilities is Amazon Ring. In issue 21, we had the plaintext nature of the audio and video streams, and in issue 57, the unencrypted connection during the first setup. This time, we are dealing with the OWASP API3:2019 — Excessive data exposure.
Another reminder to API developers:
- Do not provide more information than what your application is going to display.
- Prevent mass extraction of data through your APIs.
Vulnerability: Droom
India’s largest online vehicle marketplace, Droom, had a vulnerable OAuth2 implementation when logging in with a Facebook account.
Sayaan Alam discovered that he could simply replace the email address in the OAuth2 POST call and log into someone else’s account, with full access to their personal information and even banking details.
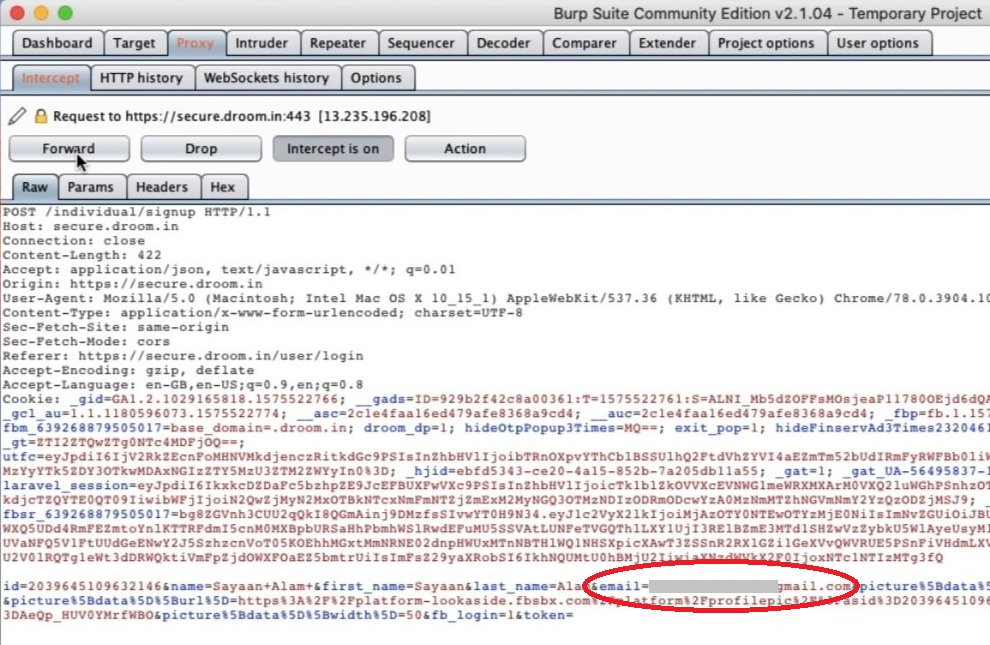
OAuth2 implementation can be tricky. Just because you use OAuth2 does not make your API automatically secure. Make sure that you either implement it according to the latest security guidelines, or use popular proven off-the-shelf implementations.
Testing: WebSocket API security
If you deal with security testing of WebSocket APIs, check out these useful articles by Shuaib Oladigbolu:
- Basics and tooling
- An example of locating IDOR in websockets
Opinion: Most exploited API vulnerabilities
Jon Wallace lists API vulnerabilities that he sees hackers attacking most frequently. Most of the characteristics of these APIs have easily find a parallel from the OWASP API Security Top 10 list:
- They are not authenticated (API2:2019)
- They use insecure URLs (API5:2019, API7:2019)
- They return too much data (API3:2019)
- They allow SQL injections or remote command execution (API8:2019)
- They lack extra layers of protection (API3:2019, API7:2019)
Webinar Recordings
42Crunch has published recordings of the two recent API Security webinars:
- Real-life examples of OWASP API Security Top 10 (plus, Q&A follow-up)
- Positive Security for APIs: What it is and why you need it! (and Q&A)
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy