This week we check out recent API vulnerabilities in India’s statewide patient portal, at the mobile operator Airtel, and in Kaspersky Internet Security products. In addition, the results of Radware Web App Security survey are out.
Vulnerability: India’s ORS patient portal
A broken object level authorization (aka IDOR) vulnerability in India’s nationwide patient portal, Online Registration System (ORS), was leaking sensitive personal and medical information of millions of patients.
Avinaish Jain found the bug in the portal allowing attackers access the personal details of any patient in any hospital across the whole India. All the attackers had to do was to change the appointment ID linked to one user in the request to get the details of another user. The API implementation was not doing object-level authorization checks and was simply trusting the caller and returning data for any record requested.
This is another example why BOLA/IDOR is also number one in OWASP API Security Top 10.
In another separate vulnerability, the attackers could also get anyone’s phone number through a password reset call. The API call was leaking this sensitive personal data in the call request. This one can be classified as API3:2019 — Excessive data exposure.
Vulnerability: Airtel
Ehraz Ahmed has found another API vulnerability, this time with Airtel, the 3rd largest mobile operator in India.
An exposed test API was leaking personal information of users. The attackers could call the vulnerable API to retrieve user details like name, gender, email, date of birth, address, subscription info, IMEI number, and so forth. IMEI number allows to uniquely identify any mobile device and get extensive information about it.
This can be considered a classic example of OWASP API9:2019 — Improper assets management. Vendors spend time and effort protecting their production APIs and forget about test instances or legacy versions that are not nearly as protected and yet give access to the same production data.
Vulnerability: Kaspersky Internet Security
In-browser security can be tricky. Kaspersky Internet Security products had vulnerabilities leaking API keys for communications with the backend.
Wladimir Palant’s very detailed post shows how rogue websites could hijack the key, disable ad blocking and tracking protection, and even crash the whole antivirus or get information about the user and system, such as Kaspersky user ID.
Kaspersky’s design choices (for example not relying on browser extensions only but also injecting scripts into pages) leave them unable to properly secure and protect their product APIs.
The article can serve as a great case study on the importance of understanding your runtime architecture and its ability to store secrets.
Industry report: State of Web App Security
Radware has published their report “The State of Web Application Security”. The report includes a lot of useful statistics including:
- Organizational
- Architecture (lots of Kubernetes)
- DevSecOps
- Common attacks and response times
- Challenges
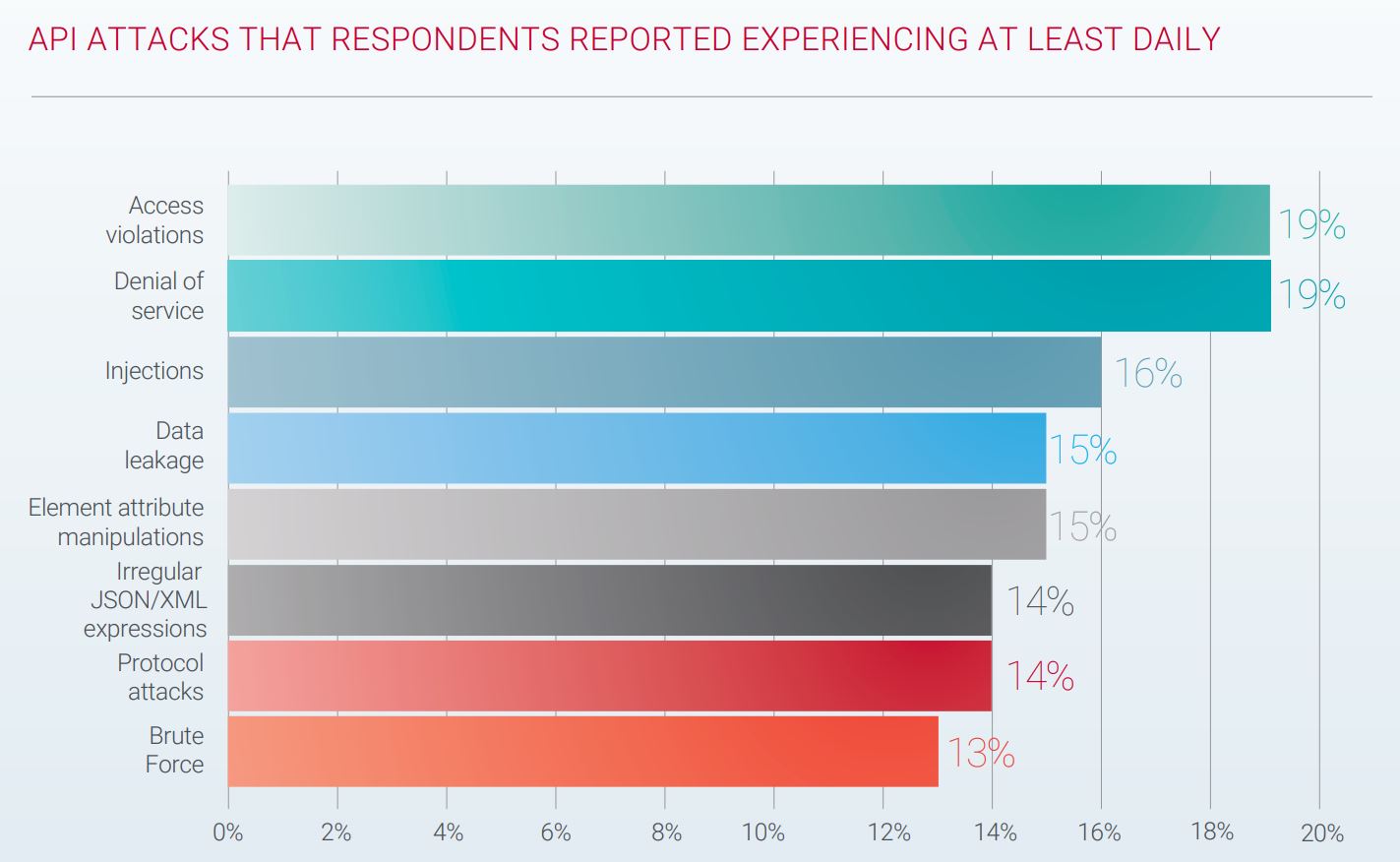
For example, see the following chart on API attacks stats:
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy