This week, we examine an industry report uncovering critical API vulnerabilities in solar power devices, and a recent case of API directory traversal flaws affecting LG Smart TVs. We also look at common weaknesses in the APIs for password-reset services, and finally review insights from the latest Stack Overflow Developer Survey on what developers are saying about AI.
Vulnerability: Major API Flaws in Solar Power Systems
Many API incidents that we cover in this newsletter involve traditional clients like business apps and SaaS platforms using broken or vulnerable APIs. But APIs now underpin integrations and connectivity for everything from industrial power plants to smart home devices. As a result, API vulnerabilities are surfacing across more industries, though often in very similar ways.
Forescout’s report on solar power platforms is an eye-opening example. It uncovers multiple critical risks in industrial and home systems, many tied to API security. Part 2 of the report, “Growatt Vulnerability Details,” is particularly worth a read.
Many of the API vulnerabilities stem from missing object or resource-level authorization. In one example, a malicious user could remove ownership of a home device from a legitimate user, and allow the malicious user to take ownership and control of the device.
The flawed API accepts a device ID (devId) parameter without verifying whether the current (malicious) user is authorized for that device, a textbook case of Broken Object Level Authorization (BOLA).
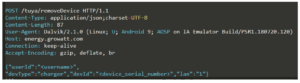
The report outlines multiple instances of BOLA/IDOR vulnerabilities in the Growatt solar power system. And as we’ve seen in our own research recently, BOLA is one of the most pervasive API flaws, showing up everywhere from India’s Government Tax portal to McDonald’s recruitment software, and in service robots used in hospitals and restaurants.
Other API vulnerabilities documented in the report include an XSS flaw, where an API accepts a malicious script injected into a request property (“name”), without proper validation. And another involves a vulnerable password-reset service, where the underlying API exposes the email address of registered users on the platform to unauthenticated users. Plenty of valuable API security lessons to be learned. Read the report.
Vulnerability: LG Smart TVs with Dumb API Bugs
Another novel API security incident, this time in LG Smart TVs. The TV supports an API to allow connected devices download files from a specific folder or directory on the TV system.
The API defined a query parameter ‘getFile’ to allow a connecting device to indicate which directory in the TV system to grab files from: /tmp/usb or /tmp/home.office.documentviewer. But the API failed to validate the value of the getFile parameter.
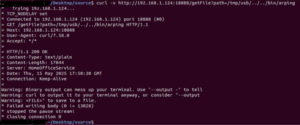
By failing to constrain the value, it gives an attacker space to attack the system through the API. A pattern that frequently works, and is well documented, is a directory traversal pattern: “../../”, which allows a hacker to trick an API into giving unauthorized access to sensitive directories and files, including credentials and access tokens that can lead to a full system takeover.
These are very common attacks against APIs that accept file paths and URLS as input. So again one to watch out for. Read the report.
Vulnerability: AI Agent platform Exposing ATO Risk
Researchers recently discovered a vulnerability in Flowise, a platform for building AI agents, that exposed users to account takeover (ATO).
The issue is related to the password reset API. Normally, these services validate requests by sending a reset link and temporary token to the user’s registered email address, ensuring only someone with access to that inbox can reset the password. But in this case, the API returned the reset token directly in the response payload. That meant an attacker could reset another user’s password without needing their email account.
The Flowise team has since fixed the issue by removing sensitive data like the token from the response. It’s a strong reminder that teams should carefully document and control API response data to avoid leaking sensitive information.
Password reset endpoints are a recurring weak spot. One of the Growatt solar power vulnerabilities mentioned earlier in this issue also involved a reset service, and we’ve covered similar cases in this newsletter: issue 275 “How to Avoid Password Reset Poisoning”, and issue 266 “Authorization Bug in Gitlab Password Reset API”. So these are services and APIs you should review closely for similar vulnerabilities. Read the article.
Article: Developer Survey Reveals AI Usage
The Stack Overflow team has released its 2025 Developer Survey, and it makes for an interesting and insightful read about developer trends and challenges.
Unsurprisingly, AI, and its discontents, features prominently in the survey this year. Some of the responses reveal both the opportunities and the downsides from using AI.
The highest percentage of developers report a lack of trust in AI’s accuracy, especially for complex or high-stakes tasks such as deploying software, monitoring systems, or conducting code reviews. AI tools are viewed more positively for learning or quick information retrieval, which probably aligns with most people’s AI experience.
The most consistent pain point emerging from the survey is that AI-generated output is rarely precise, and often requires rework. Debugging unfamiliar code produced by AI occupies a lot of time, undermining the efficiency gains developers hope for.
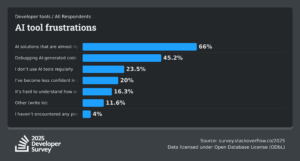
Some of these findings from professional developers match concerns about using AI in API security. While AI tools are helpful for routine tasks, critical processes still demand a human-in-the-loop to validate AI-generated outputs. Though this safeguard limits some of the key benefits AI promises: speed and scalability through full automation. Read the report
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy