This week, we have news of a vulnerability affecting the OAuth2 implementation on the Booking.com website. We have a report from Approov on their research into financial apps in the Google Play store and another great article from Dana Epp on API security checklists. Finally, we cover an interview with Matias Madou on the need for people-driven security.
Vulnerability: API flaw in Booking.com could affect other sites
Recent research featured in IT Security Guru revealed an API flaw in the Booking.com platform relating to implementing the Open Authorization (OAuth) social-login functionality. Booking.com’s teams immediately investigated the findings, resolved the vulnerability, and thanked the researchers, encouraging others in the global security community to participate in their bug bounty program.
The technical details of the vulnerability are somewhat limited, with the report indicating that a vulnerability existed in the Facebook social login using OAuth2. Commonly web developers use social logins as an expediency to prevent users from having to create a bespoke username and password credential pair. Whilst convenient from an end-user point of view, a poorly implemented OAuth2 implementation can significantly impact users. As the report suggests, it was possible that this misconfiguration could have allowed for large-scale account takeover (ATO) on customers’ accounts and server compromise, allowing bad actors to manipulate platform users to gain complete control over their accounts. In addition, it would have been possible to steal Personal Identifiable Information (PII) and other sensitive user data stored internally by the sites; or perform any action on behalf of the user.
This a timely reminder to API developers that whilst OAuth2 (or other standard mechanisms) should be used as far as possible, their complexity can result in insecure implementations with significant consequences.
Report: Financial apps in Google Play store leaking sensitive API data
Next, we have an eye-opening report from newsletter regular Approov on their research into financial apps on the Google Play store. The key takeaway was that ninety-two percent of financial apps hosted on the Google Play App Store contain extractable data such as API keys. Of those leaky apps, nearly a quarter spilled “extremely sensitive” data, such as authentication keys used for payments and monetary account transfers. The research is based on the “top 200” financial services apps from the Google Play App Store in the United States, United Kingdom, France, and Germany.
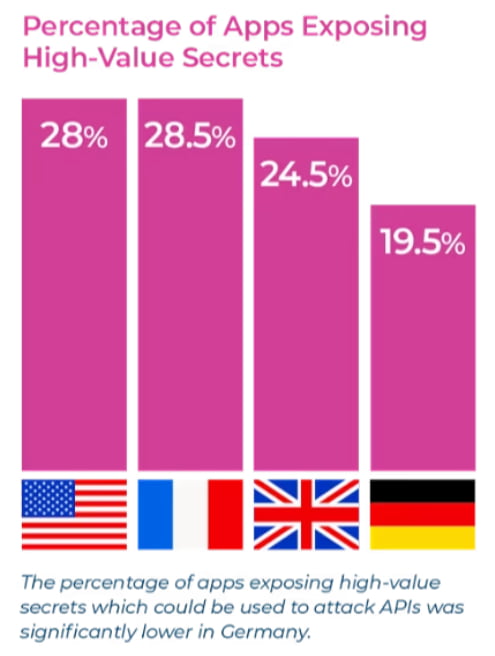
Approov uses a five-point framework to identify mobile application attack surfaces leading to secret leakage. These are:
- User credentials
- Application integrity
- Device integrity
- API channel integrity
- Service vulnerabilities
According to Approov, most apps surveyed had very poor defenses against attacks targeting the device environment, and even fewer were well protected against machine-in-the-middle (MitM) attacks. Such attacks allow adversaries to insert themselves in the communication channel between the device and API service and effectively subvert otherwise secure communication channels.
In conclusion, Approov makes the following three top recommendations for improving secret and API key security, namely:
- Protect secrets: never embed secrets in code, as they can almost always be reverse-engineered.
- Use runtime protection: using a runtime protection environment can prevent tampering with the device of the communications channel.
- Manage secrets using a secure cloud service: Use a cloud service to deliver secrets to the device on an on-demand basis only if the device is deemed secure.
Some very useful advice for mobile app developers; thanks to the team at Approov for their contribution.
Article: API security testing checklist
By now, most readers will be familiar with the fine work Dana Epp is doing in the community with his thought-provoking articles, and this week is no different. This time it’s an API security checklist (based on the fine Shieldify list) but with a mapping to the MITRE Common Attack Pattern Enumeration and Classification (CAPEC). By creating this mapping, it allows teams to understand how to assess findings based on the attack type, how the exploits work, how they can be detected, and the skill levels needed to conduct the attack.
I won’t reproduce the full list here, but I recommend security practitioners take a good list through Dana’s list and the original list.
My favorite tip from this article was the pointer to the Domains of Attack viewer from MITRE — this allows visualization of the top-level domains, then the meta domains, then the standard attack patterns, and finally, the detailed attack patterns. The viewer also has an excellent filter capability to filter on likelihood, scope, severity, and technical impact.
Article: People-driven remediation is key to strong API security
Finally, this week, we feature an interview with Matias Madou, Secure Code Warrior CTO, on why people-driven remediation is the key to strong API security.
Madou warns against pursuing every latest and greatest security tool since this can distract development teams whose time would be better spent understanding the basics of secure API development.
Webinar: Mastering Secure API Development with GitHub and 42Crunch
With over 100 million users and 330 million repositories, GitHub has become the de facto home of software development. GitHub has become so much more than purely a Git repository hosting platform. With features such as repository forking, pull requests, and, most notably, GitHub Actions is now a one-stop development platform. 42Crunch is the developer-first API security platform with plugins for VS Code and GitHub to automate the process of building secure APIs right in the developer’s natural environment.
Join Colin Domoney (Chief Technology Evangelist at 42Crunch) and Isabelle Mauny (Field CTO at 42Crunch) on June 13, 2023 at 9am PDT / 5pm BST, as they take a deep dive with live demos into how 42Crunch combines with GitHub to facilitate secure API development:
This practical demo will showcase the following:
- Discover OpenAPI definitions automatically within repositories.
- Audit OpenAPI definitions in GitHub Actions and view results alongside other code scanning tools all in a single view.
- Scan your API for security vulnerabilities directly within GitHub Actions.
- Deploy the 42Crunch API firewall within GitHub Actions.
- Protect your main branch by performing automated testing of APIs directly within the pull request process, allowing informed risk-based decisions for reviewers.
- Using the 42Crunch GitHub application to enrich the pull request annotations further, allowing better decision-making for the reviewer.
- Drive the entire process without ever leaving VS Code!
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy

