This week, we have news of another CSRF vulnerability affecting an API, this time in the F5 BIG-IP device. We also have an article from Dark Reading on the next generation of supply chain attacks, a quick guide on how to hack APIs, and finally, a very illuminating report from Google Cloud on API security research findings in 2022.
Vulnerability: CSRF vulnerability in F5 BIG-IP
Last week we featured a CSRF vulnerability in the Plesk server administration user interface, and this week we have a CSRF API vulnerability affecting the F5 BIG-IP device. Security researchers at Rapid7 discovered that the endpoint /iControl/iControlPortal.cgi lacks cross-site request forgery (CSRF) protection, nor does it require a correct Content-Type or other typical API protections. To exploit this weakness, an attacker lures a user (who has an authenticated session to an F5 BIG-IP device) to his website, from where the attacker can launch arbitrary API commands to the F5 backend API using the privileges of the target user.
Standard protections against CSRF attacks include the use of built-in CSRF protections in your framework, the use of the synchronizer token pattern or the double submit cookie pattern. All of these are covered in detail in the popular webinar with Jim Manico from earlier in the month.
The researcher has provided a GitHub repository showing several proof-of-concept exploits which are worth reviewing — CSRF is an old attack vector but still prevalent in the API-centric world.
Article: Next generation of supply chain attacks
Supply chain attacks are the new emerging threat du jour in DevSecOps land, and not without good cause. As the monolith is decomposed and software is assembled rather than written, so risk is inherited from the upstream supply chain. This excellent article from Dark Reading discusses the topic in much greater depth, including their thoughts on how APIs (and their keys) are one of the leading concerns in software supply chains.
Traditionally, supply chain risks are considered vulnerabilities in software dependencies passed downstream — the canonical example is vulnerabilities in open-source components aggregated into an end product. Recently this supply chain weakness has received focus at the highest level from none other than the U.S. President in an executive order.
Now, what does the modern supply chain look like? Typically modern software is constructed using hyperconnected systems, for example, 3rd party provider APIs, CI/CD systems, and various Cloud hosting services. These systems are all connected via APIs and, of course, their associated keys and tokens. This dramatic growth of the supply chain to include all interconnected services and dependencies creates challenges to security teams in firstly understanding their total attack surface and then addressing the impost important weaknesses. Remember, a chain is only as strong as its weakest link.
One of the easiest wins for reducing the blast radius of any attack against software supply chains is to reduce the scope of API keys and tokens, either by reducing their privileges, scope, and lifetime. The author highlights two recent examples of SaaS providers who have changed their API key and token scopes to minimize the impact of leakage, namely:
- Hubspot help eliminate potential risks associated with the use of API keys.
- GitHub introduced a fine-grained personal access token that offers enhanced security to developers and organization owners.
A timely guide to protecting API keys and tokens in your supply chains.
Guide: How to hack APIs
Guides on API hacking are always popular with readers of the newsletter, and this week, we feature another list of resources courtesy of INTIGRITI on Twitter. In summary, the following great resources are covered:
- Everything API Hacking on YouTube
- OWASP API Security Top 10 project
- Inon Shkedy’s 31 days API Security Tips
- OWASP crAPI project
Another great list of resources to be bookmarked.
Report: Google Cloud 2022 API security research report
Finally, this week we have an excellent report from Google Cloud on API security in 2022. Although it is behind a registration wall, I highly recommend this for anyone working in API security and wanting to understand current trends. The report contains a wealth of interesting statistics relating to API security; some of the highlights include the following:
- 62% of C-Suite executives reported they had experienced a security incident.
- API security threats come from misconfigured APIs (40%), and outdated APIs (35%).
- Concerningly, over three-quarters of organizations, delayed a product release due to a security incident.
- Only 40% of organizations had a complete API security strategy in place.
Most interesting to me was the validation of the shift-left approach toward API security, with the majority of respondents focusing on the proactive identification of security threats and the adoption of automation and orchestration:
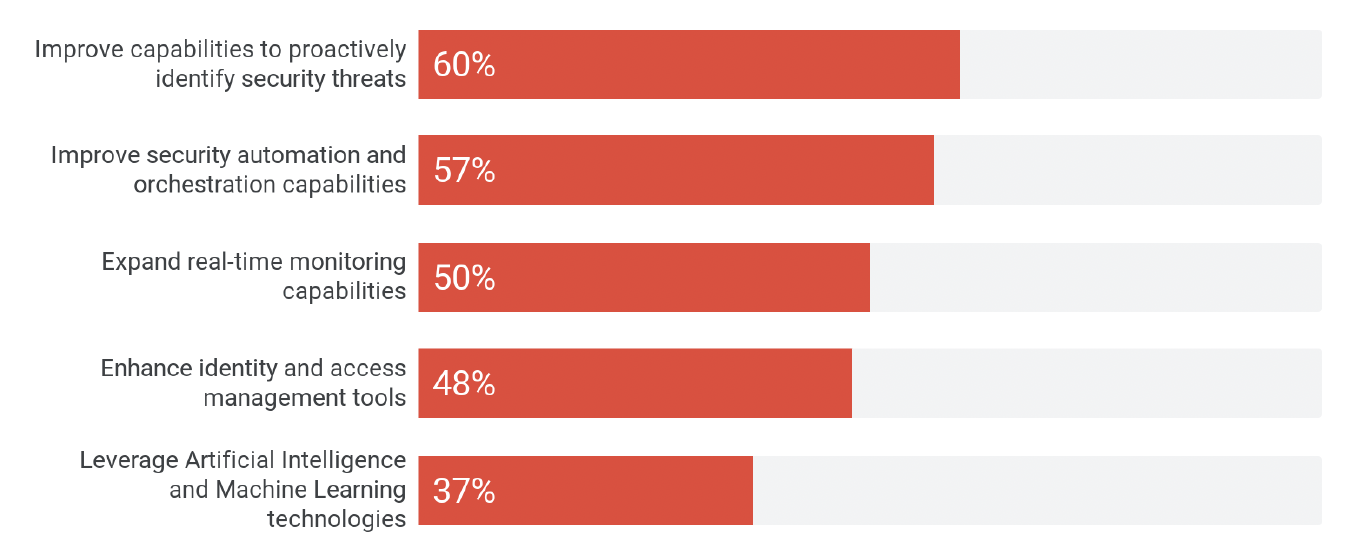
An interesting report sounding a generally optimistic note for API security.
Event: API Days Paris – December 14-16
As a loyal subscriber to the newsletter, 42Crunch is happy to invite you to apidays Paris 2022, APIs for the next ten years: Software, Society, Sovereignty, Sustainability, from December 14-16 2022.
Isabelle Mauny, our co-founder and Field CTO, will be joining other illustrious speakers next month at the event and presenting two sessions on:”The State of OpenAPI” & “Anatomy of Recent API Breaches with Lessons Learned.”
There will be 3,000 attendees (Developers, IT Managers, CTOs, CIOs, VP Engineers, Architects, PMs, etc.), and the 200+ speaker lineup includes:
- Mark O’Neill, VP Analyst, Chief of Research for Software Engineering at Gartner
- Mike Amundsen, Author at amundsen Inc.
- Gilles Babinet, Co-Chairman at Conseil National du Numérique and Digital Champion pour la France à la Commission Européenne
Because apidays loves our community, they are offering us 30 free tickets (value of up to €799 each) with code “GUESTOF42CRUNCH” at checkout through this link. First come, first served, and we hope to see you there!
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy
