This week, we have news of an API vulnerability in the scheduling platform Easy!Appointments allowing unauthorized access. We also have articles on whether the growth in APIs compromises security, how API traffic visibility is a key for API security, and some basic tips on locking down APIs to improve security.
Vulnerability: API access control vulnerability in scheduling platform Easy!Appointments
This week, we have an API vulnerability in the open-source scheduling platform Easy!Appointments, courtesy of The Daily Swig. The vulnerability was discovered by security researcher Francesco Carlucci, and it is tracked as CVE-2022-048, with a CVSS score of 9.1.
Carlucci discovered that the method ajax_get_calendar_events() passed three parameters – startDate, endDate, csrfToken – and no authentication tokens or headers. Unfortunately, he also found that it was possible to obtain a suitable CSRF token simply by visiting the website’s public bookings form, capturing the token with the browser developer tools, and then submitting this on the unprotected API. This simple attack could allow an attacker to query all calendar data, including any PII of users included in the bookings.
Carlucci also commented that the Easy!Appointments used a PHP framework CodeIgniter which did not include built-in support for authentication of API endpoints, forcing users to implement their own authentication. Unfortunately, it is all too easy to omit this during development, as was the case here. Best practice would be to use standard authentication middleware, such as that provided by frameworks like Laravel.
Carlucci submitted his discovery through the bug bounty platform Huntr and directly to the application developer. A patched version of the platform, v1.4.3, was released on 8 March, and users are advised to update to this version, or to use a patching script provided by the developer.
Article: Are new APIs compromising security?
An age-old conundrum for enterprises is how to balance business agility driven by innovation against the security risks that may be created by this fast-paced innovation. Nowhere is this more acutely felt than with APIs, as discussed in our first article this week.
APIs are increasingly an essential element of digital transformation, enabling the integration of disparate systems to meet partner and customer needs. The growth of these APIs is widely regarded as growing exponentially. Unfortunately, this also poses a challenge from a security perspective due to an over-reliance on perimeter-based security controls, such as firewalls or network segmentation. APIs allow a direct end-to-end connection between a (potentially malicious) client and a data backend.
According to the author, a savvy enterprise should keep the following in mind with regard to API security:
- Although it is important to address API vulnerabilities (such as the OWASP API security Top 10), a focus should be given to flaws in business logic, too.
- Maintaining an accurate and up-to-date API inventory is key to understanding the organization’s risk profile.
- APIs can also be misused or abused by malicious actors, like in data mining or scraping — it’s not enough to merely prevent direct breaches through flaws.
- Be wary of rogue actors within your partner or 3rd party organizations who have unfettered access to your APIs.
Article: Visibility is key for API security
Next up this week is a quick read on the importance of API traffic visibility, both in east-west and north-south directions. Traditionally, CISOs have focused on north-south traffic (that which connects to 3rd parties and external systems) and tended to neglect east-west traffic (internal traffic connecting internal systems).
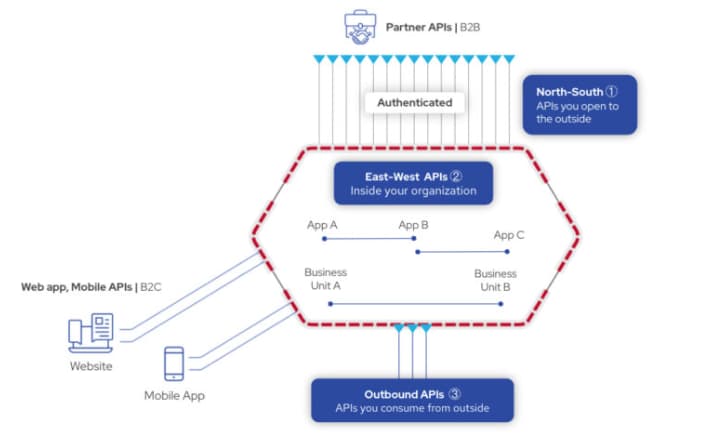
The author suggests that traditional security techniques based on network and endpoint protection which look for command/control, reconnaissance, lateral movement, and exfiltration are not suited for API security. APIs allow direct exposure of systems to a client and fly below the radar of traditional network and endpoint protection. API security solutions should provide monitoring of traffic across all compass points to properly protect against API threats.
Article: Locking down APIs to improve security
Our final item this week is another quick read on simple and practical steps for improving API security by locking down your APIs.
The author reiterates the importance of maintaining an accurate and up-to-date inventory of the organization’s APIs to quantify risk and manage a security strategy, and goes on to suggest five key reasons why organizations are failing to address API security gaps:
- Dangerously narrow view of API security: API security goes beyond pure vulnerability reduction and should embrace a broader definition that also covers abuse and misuse cases and complex business logic flaws.
- Exponential threat of an API breach: Due to the interconnected nature of APIs, the risk of a breach is exponential. A breach in one API may expose several connected systems.
- Flying blind in an ever-changing landscape: Without an accurate inventory of APIs, it is difficult to manage risk.
- Limited API security functionality with traditional tools: Traditional tools, such as WAFs and SAST/DAST, typically do not work well with APIs.
- Confusion around ownership: Multiple teams are involved with the development of APIs, and this creates confusion as to who is ultimately responsible for API security.
Keeping these five points in mind when planning your API security is a long step towards more secure APIs and systems.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy