Vulnerabilities
We have reported on API vulnerabilities in kids’ smartwatches before. The watches remain vulnerable to API attacks, these stories just keep pouring in:
- The European Union is recalling Enox Safe-Kid-One smartwatches because of vulnerable APIs. The APIs have no authentication or encryption, so attackers can access them, retrieve any information on them (like location), change settings, initiate calls.
- PenTestPartners found a serious API vulnerablity in the Gator smartwatches. The API was using an undocumented parameter
User[Grade]to identify the user level. The web UI had the parameter set to1, but if attackers changed the value to0, they got full admin access to the whole platform and all devices. Security by obscurity does not work.
APIs behind dating apps can be quite bad, too. The APIs of Jack’d, a dating app for gay and bisexual men, do not require any authentication or authorization, only the mobile app does. The image IDs seem to be sequential and thus open to enumeration. This means that anyone knowing the API URL can just go and retrieve these private images of the application users one by one.
Even devices meant to protect your network can have vulnerable APIs: CUJO AI firewall device got hacked through its APIs. The firewall exposed APIs that did not require authorization. The APIs were meant to be used by the mobile app to communicate with the cloud service. However, lack of authorization meant that any user with a valid x-auth-token could enumerate other users, access their policies, and even change them.
Tools
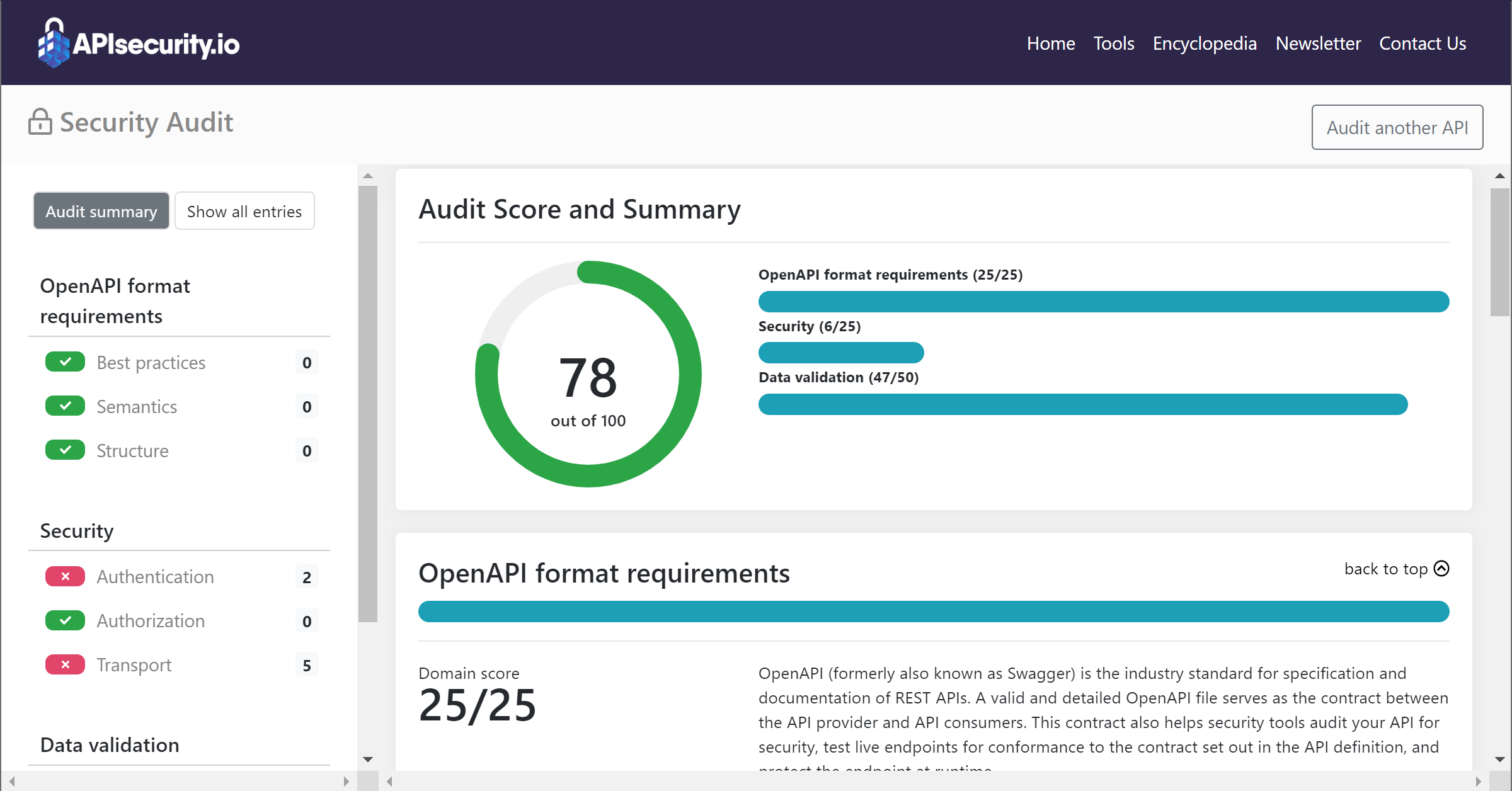
If you have OpenAPI (formerly known as Swagger) definitions, APISecurity.io now offers API Contract Security Audit. This is an online security audit tool you can use to check your APIs for security and other issues:
- Go to https://apisecurity.io/tools/audit.
- Upload your OpenAPI file, and wait while Security Audit checks it.
- Check the audit report for the overall grade, and drill down into individual sections.
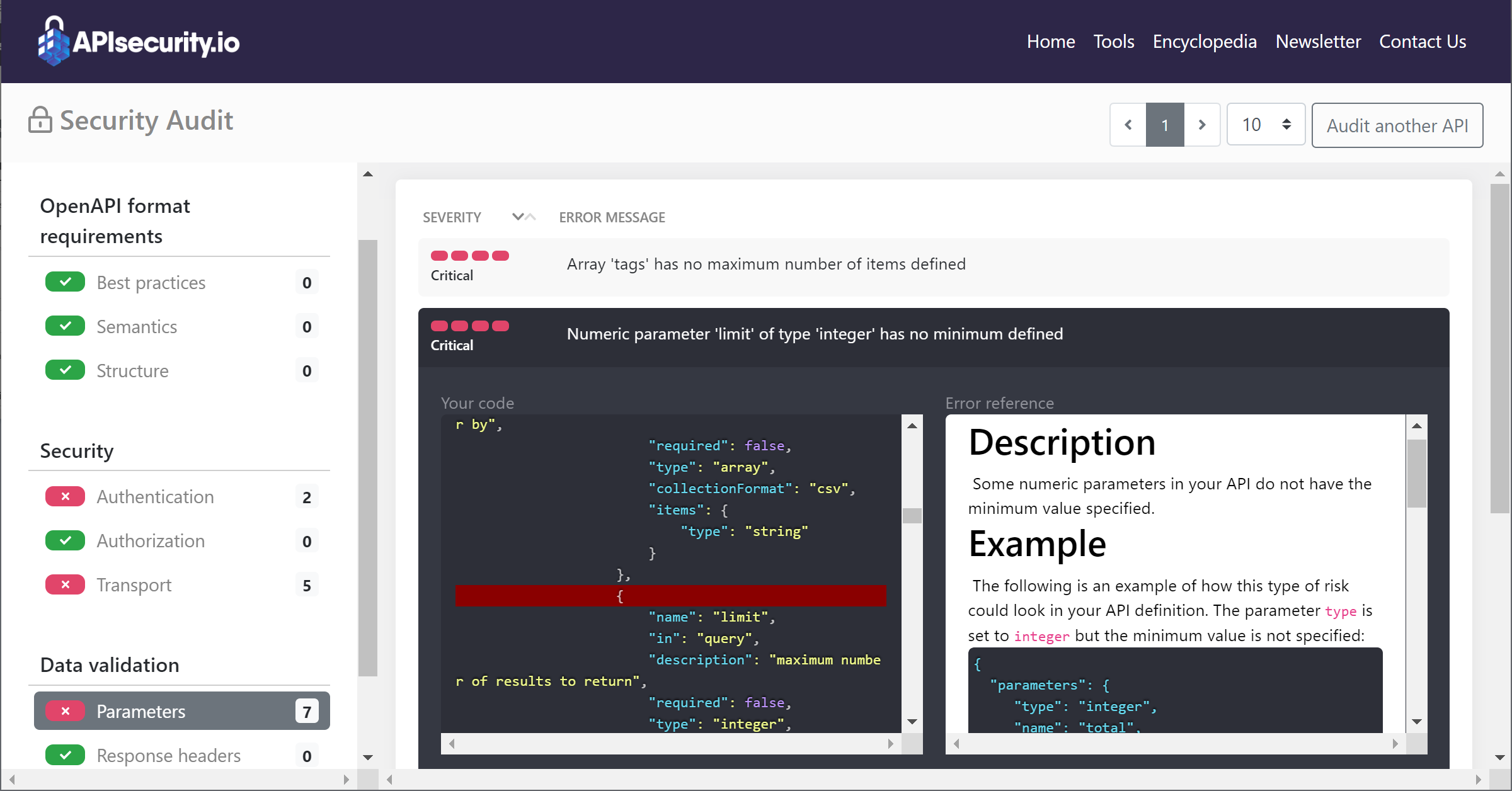
- Click the found issues for detailed descriptions, possible exploit scenarios, and recommended remediation for them.
Best Practices
Speaking of OpenAPI, see the introduction to schema-first API design and OpenAPI Specification write-up by Yos Riady. His focus is on developer efficiency, but he also talks about how contract-based APIs help to design and enforce security.
Governance
Google is now charging developers hefty fees for a security audit if they want to use Gmail APIs. If your application is using Gmail API, tomorrow (Feb 15, 2019) is your last day to submit it to a security review.
The cost is $15K-$75K. If not passed (or not submitted), Google will cut your API access. Interesting API security governance step…
You can subscribe to this weekly newsletter at https://APISecurity.io
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy