This week, we take a look at the recent API vulnerabilities reported at Microsoft and Truecaller Guardians, the new penetration testing labs for API security, and an upcoming webinar on the API security process at Ford Motors.
Vulnerability: Microsoft online accounts
API endpoints for resetting account passwords are a frequent attack vector. Attackers brute-force these by supplying as many possible combinations of password reset codes as they can within the time window available to them.
Laxman Muthiyah found a way to break into the password reset API for all Microsoft’s online accounts. He requested a password reset code — a 7-digit one in Microsoft’s case — for the target account and then tried to brute-force his way in by calling the verification API with all possible combinations from multiple locations.
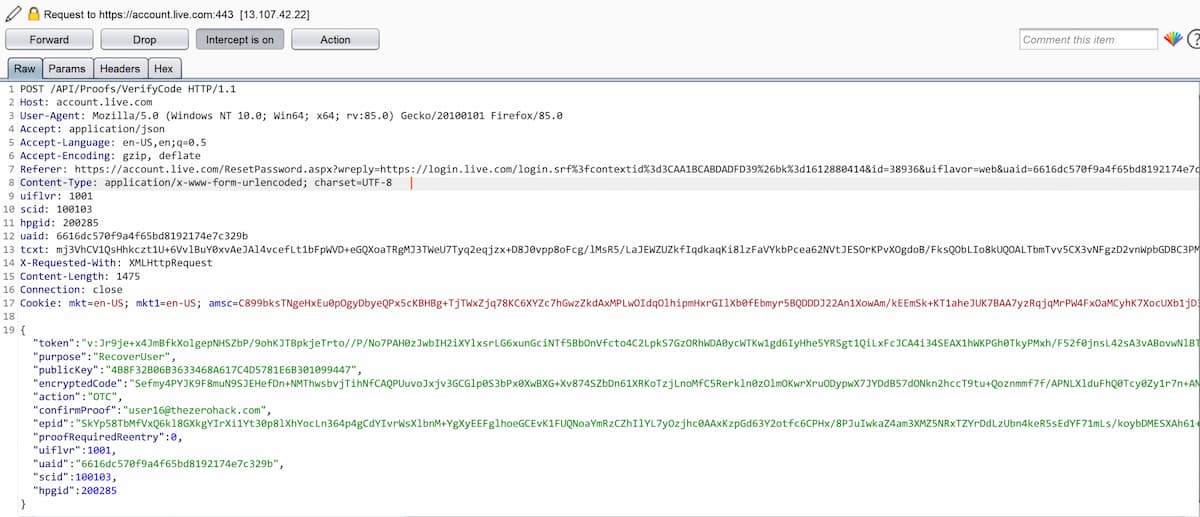
Microsoft had actually already taken measures to make it harder to break into the system:
- The API did not accept the code just as plain numbers but had some basic encryption between the client and the API that the attacker had to figure out. This also made it impossible to use off-the-shelf iteration tools like Burp plugins.
- The API had rate-limiting in place.
- The API detected attacks with parallel requests from multiple endpoints quite quickly, blacklisted the IP addresses, and rejected all codes from them, including the correct one.
Despite this, Muthiyah managed to demonstrate that he could still get in if he deployed the automated attack simultaneously from thousands of clients. Even if an account was protected with two-factor authentication (2FA), the same operation just had to be repeated for the 6-digit 2FA code.
For his efforts and report, Muthiyah received the award of $50,000. Microsoft has fixed the issue.
We have previously covered a similar vulnerability that Muthiyah reported for Instagram.
Lessons learned here:
- Password reset endpoints are frequently a source of OWASP API:2 Broken Authentication vulnerability.
- Assume that attackers can launch distributed attacks from multiple IP addresses.
- MFA helps but can be vulnerable to similar attacks.
- The more complex reset codes you use, the harder it will be to brute-force them. An alphanumeric code of the same length has a lot more combinations.
- Smart rate-limiting mechanisms serve as additional protection.
Vulnerability: Truecaller Guardians
Truecaller has recently launched its Guardians app that allows permanently sharing your real-time location with trusted contacts, like your family. Anand Prakash found a way to take over any account in the system and access sensitive information of users and their family members.
The vulnerability lay in the API that allowed users to log into the app using their Truecaller account. All attackers had to do was to first log into their own Truecaller account and then, when going to the Guardians app, substitute their phone number in the payload with that of their intended victim. The app then used that phone number as the ID to match the user with the profile.
POST /v0/user HTTP/1.1
Host: api. getguardians. com
Content-Type: application/json
Accept: */*
Connection: close
Content-Length: 656
User-Agent: Guardians/1.1.3 (com.truesoftware.Guardians; build:1.1.3; iOS 14.4.0) Alamofire/5.4.1
Accept-Language: en-IN;q=1.0, kn-IN;q=0.9, hi-IN;q=0.8, hi-Latn-IN;q=0.7
Authorization: Bearer aQ4AOdxwPPWJM06sICQMQRWlANOC1crV
Accept-Encoding: gzip, deflate
{
"userVerificationInput": {
"nonTCUserToken": "",
"tcUserSignature": "[Attacker's Signature]",
"tcUserPayload": "[Attacker's Payload]"
},
"phoneNumber": {
"countryCode": "IN",
"number": "[Victim's Phone Number]"
},
"tcUser": true,
"ios": true
}- There was no protection against payload tampering (this wasn’t a signed token)
- The Guardians app did not validate in any way that the phone number in the incoming request belonged to the user authenticated in Truecaller. It would just give full access to the account to anyone presenting a known phone number.
This is another example of OWASP API:2 Broken Authentication vulnerability. Be careful with your authentication workflow design, especially when you are looking at a federated scenario and users logging into one system then get access into another.
Training: API security pentesting labs
Penetration testing is best learned by practice. PentesterLab has created a special category and started adding API security labs to their site. One hands-on API security lab is already available, with 3 more in the works.
Perfect opportunity to get some hands-on experience.
API security in the enterprise: Ford Motors
Rolling out a successful API security program in a large enterprise can be a challenge.
Next Thursday, March 18th at 8 AM (PST), Darren Shelcusky, Manager of Vehicle & Connectivity Cybersecurity at Ford Motor Company, tells how their process was.
In the webinar, Darren will explain Ford’s approach to API security and their journey to enforce security compliance while ensuring productivity of hundreds of developers managing thousands of APIs.
Registration is open here.
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy
