This week, we take a look at the recently discovered API attack in NoxPlayer, the latest annual “State of Web Application Security” report by Radware, a detailed step-by-step pentesting tutorial, and a recording of a session on API security and Azure API management from AppSec Israel.
Vulnerability: NoxPlayer
[UPDATE] We have been contacted by a BigNox representative assuring us that the security issues have been fixed. They also advised that the original ESET research article has been modified to include their statement on the measures taken.
NoxPlayer is an Android emulator for PCs and Macs. BigNox, the company behind the emulator, claims that they have over 150 million users predominantly in Asian countries.
The product has an automatic update system where the client invokes a cloud API to check for updates, download, and install them. Security researchers from ESET discovered that this API got hacked to deliver malware instead of normal updates.
The researchers discovered that attackers made the API to selectively deliver to targeted users malware URLs instead of those of regular updates:
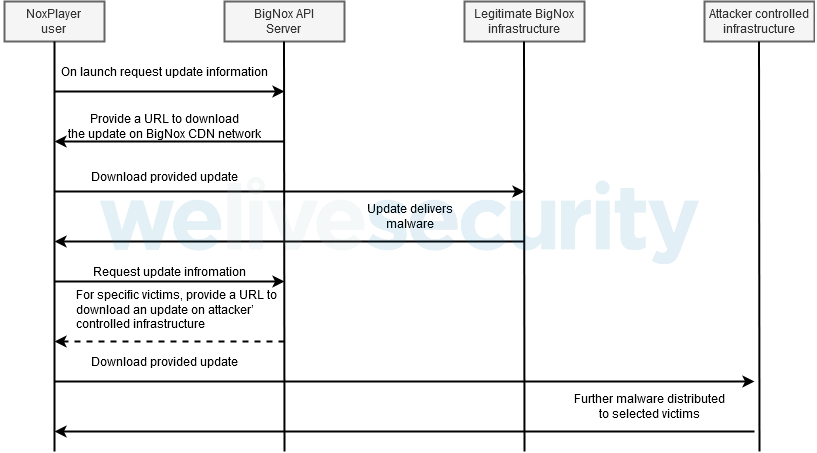
This was a relatively sophisticated attack, and it showed why data validation needs to happen not only on API requests but also on responses. Defining strict patterns for returned data (in this particular case, a regular expression for acceptable update URLs) could have prevented the attack.
Industry statistics: State of Web Application Security Report
Radware has released their “2020-2021 State of Web Application Security Report”. Their main conclusion is that API abuse has become the leading threat in the field.
Here are a few of the report highlights:
- Nearly 40% of organizations surveyed reported that more than one-half of their applications are exposed to the internet or third-party services through APIs.
- 55% of organizations experience a DoS attack against their APIs at least monthly.
- 49% experience some form of injection attack at least monthly.
- 42% experience an element or attribute manipulation at least monthly.
Unfortunately, Radware also found that application security specialists have limited influence on application design and lifecycle:
- In approximately 90% of organizations, security staff is not the prime influencer on application development architecture or the budget.
- Some 43% of companies said security should not interrupt the end-to-end automation of the release cycle.
Tutorials: Pentesting step-by-step
If you want to learn more about penetration testing exercises, here’s a nice step-by-step report by Nairuz Abulhul.
He took over a Hack The Box machine using vulnerable APIs:
- An API failure leaked the admin username in the exception text.
- Another exception leaked the serializer information.
- Finally, lack of input validation allowed him to perform an injection and take over the box.
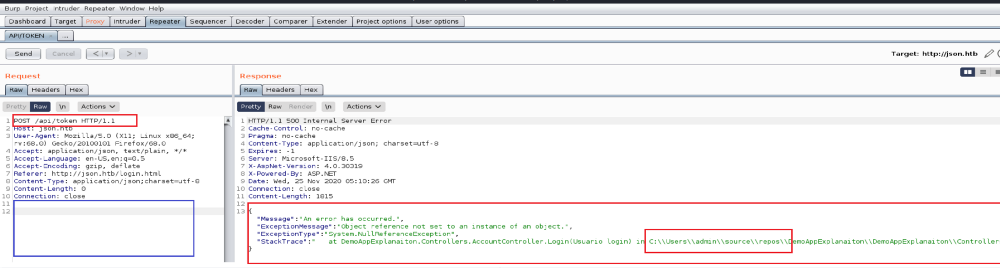
Obviously, this is also a good reminder to all API providers why excessive data exposure is a big deal, and data validation is critical.
Videos: Building better security for your API platform using Azure API Management
If you have APIs running in Microsoft Azure, this conference talk recording should be valuable to you.
In his talk from AppSec Israel, Eldert Grootenboer goes through security best practices when using Azure API Management:
“This session will show how we can use Azure API Management to leverage better security for your APIs. Expect everything around hardening security of your services, with demo’s, best practices, and tips and tricks from the field.”
Get API Security news directly in your Inbox.
By clicking Subscribe you agree to our Data Policy